
Cyber Terorism and Ethical Hacking
What is Terrorism?
There are different definitions of the terms, Terrorism, and Terrorist in various sources. To maintain a general definition and keep it better in mind, it would be useful to write the definition of "terrorism" in Article 1 of the Law on Combating Terrorism numbered 3713:
Article 1 - Terrorism; the use of force and violence; to change any coercion, intimidation, or threat method directed towards the characteristics of the Republic specified in the Constitution, political, legal, social, secular, and economic order; the indivisibility of the State's territory and nation.
Any kind of criminal act that individuals belonging to an organization will commit in order to disrupt the integrity, weaken the authority of the Turkish State, endanger or eliminate the existence of the Republic, eliminate or capture it, eliminate basic rights and freedoms, disrupt the internal and external security of the state, disrupt public order, or protect the general health of the state is a crime to disturb the public order or protect the general health of the state.
While the term Terrorism expresses fear and terror, Terrorism must add continuity and political content to this concept. Terrorism has consequences that cannot be achieved through "war and diplomacy."
The systematic and calculated use of terrorism for political purposes, based on a theory, philosophy, and ideology, to achieve them, frighten them, and conform to them."(See Appendix-1)
What is Cyberterrorism?
There are many misconceptions and misunderstandings about cyberterrorism. First, we are examining this subject to provide an accurate definition.
Cyberterrorism is an unlawful threat to, and a harmful attack on, computers, network systems, information from official entities, and databases with the aim of intimidating and suppressing individuals and social and political authorities.
To classify an attack as cyberterrorism, it must also involve violence against an individual or property. Cyberterrorism can be characterized as attacks causing physical or lethal damage and resulting in significant economic losses. Serious attacks on critical infrastructure can be defined as cyberterrorism based on the impact they cause.
"In order for an attack to be considered cyberterrorism, disruption of essential services is required."
------------------------------------------------
EXAMPLES OF CYBERTERRORISM AROUND THE WORLD

In this section, we provide examples of cyberattacks by cyberterrorists against governments and individuals around the world. Computer hackers sometimes carry out cyberattacks individually, sometimes in groups, and occasionally on behalf of a government.
Cyber Attack on the U.S. National Security System

Kevin Mitnick
Kevin Mitnick, who was arrested and known as the world's mos famous hacker, destroyed the U.S. national security system by copying confidential corporate information in the United States (1995).
Cyber Attack on NASA's Computer System
At the age of 16, Jonathan James hacked NASA's computer system and downloaded software worth 1.7 million dollars. With a small program he sent to the Department of Defense, he was able to read all messages coming from the military (2000).
Cyber Attack on Bhabha Atomic Research Centre
Members of the global Milworm hacker group, New Zealander Venomous and British JF, in June 1998, managed to take control of the sub-system of India's Bhabha Atomic Research Centre in the city of Mumbai for days and obtain rich information about the government's tests. This group, expected to oppose the spread of nuclear weapons, later carried out the same attack on Pakistan.
Protest Attack against the U.S. and NATO
In 1998, young people from various regions of Eastern Europe took control of an aircraft in the region via the internet, protesting the U.S. and NATO's surveillance tower system and crashed it in a military area in Bosnia and Herzegovina. Despite government condemnation of the attacks, no arrests were made.
Cyber Attacks on the U.S. Military by China
The U.S. military has been a primary target of Chinese cyberattacks. This is followed by the Department of the Interior, the Department of Commerce, and the Department of Homeland Security. Industrial, academic, financial, and defense-related databases are also vulnerable to attacks. Unfortunately, U.S. officials have been very cautious in dealing with China, and they were hesitant to openly admit that the attacks were carried out by Chinese agents. A U.S. cyber security expert stated, "Chinese agents have already infiltrated half of your espionage system," but in fact, Chinese cyber warfare units gained access to the unclassified NIPR NET server of the Pentagon and produced the necessary software to break down this system during wartime. A U.S. official admitted that China had downloaded between 10 and 20 terabytes of information from NIPR NET, and also stated that the Chinese were considered a threat to the U.S.
-----------------------------
MEASURES TO BE TAKEN AGAINST CYBER TERRORISM

To combat cyber threats, practices must extend from individual responsibility to the international community. Responsibility, which starts at the individual level, increases and extends to private sector companies, then to public authorities, and finally to the international community. In practice, it is observed that countries make legal agreements and enter into administrative structures parallel to their perceptions of cyber threats.
**First and foremost, a legal framework must be established and laws must be enforced; then there should be international consensus.
Coordination of internal technical, intelligence, and operational units.
These tasks should be carried out by personnel who are experts in the field and capable of continuously monitoring evolving technology, and they should receive continuous training.
Countries should work together in identifying cyber threats.
Countries should collaborate on legal, administrative, and technical regulations.
Collaboration is essential in the fight against actions in cyberspace, as it is in all crimes.
Law enforcement agencies, data collection authorities, agencies, internet service providers, and all other relevant parties should be included.
Governments or international organizations should also take steps to protect illegal and personal data on the Internet, expand e-commerce, and strengthen communication security.
Governments should extradite those who harm individuals or organizations in another country through a cyberattack in their own country.**
Only in this way can criminals become aware of the potential threat they create on the internet and can be prevented.
What is Ethical Hacking and Who Are Ethical Hackers?

Ethical hacking, also known as computer hacking, involves an authorized attempt to gain unauthorized access to a computer system, application, or data. To conduct an ethical attack, the strategies and actions of malicious attackers must be replicated. This practice helps identify security vulnerabilities that can be addressed before a malicious attacker has a chance to exploit them.
Ethical computer hackers, also known as "white hats," are security experts who perform these security assessments. Their proactive work helps improve an organization's security posture. Ethical hacking missions, with the prior approval of the IT organization or owner, are the exact opposite of malicious computer hacking.
WORLDWIDE RECOGNIZED TURKISH AND FOREIGN HACKER GROUPS
TurkHackTeam

In short, THT or TurkHackTeam is one of Turkey's oldest Cybersecurity and Ethical Hacking forums, founded by a hacker using the nickname "Arsenik" in 2002. TurkHackTeam first gained attention by hacking one of the subdomains of Microsoft's web portal MSN, under the leadership of ZoRRoKiN. They describe themselves as a Turkish hacker group based on Atatürk's principles and nationalism.
This group claims to combat any form of cyber threat that may arise against Turkey and identifies itself as the underground world of the internet. With the leadership of Veteran 7 and the "Anka Attack Team," the group gained prominence through several sensational hack operations in 2015.
One of the group's former top-level executives, Herakles, carried out an operation against the Vatican, which made headlines in many international news portals, including the Washington Post. Another former leader, YeniCherix, hacked the Democratic Society Party. Turk Hack Team is a platform where projects in the field of social responsibility are also prepared. The first project was to send letters to the army and police for moral support after the escalation of terrorist incidents in 2016. In the same year, they distributed food through an association in Africa. Some group members later visited Anıtkabir for the November 10th Atatürk Memorial Day ceremonies and left a letter in the visitor book. In 2017, the group collected books from participants in response to online cybersecurity training and donated these books to middle and high schools that had been pre-determined to establish libraries. Between 2020 and 2021, they provided financial and moral support to village schools. In 2022, they provided food and shelter assistance to stray animals. TurkHackTimi - Anka Attack Teams performed some of the actions listed below. The assault teams are "Anka Red Team." Currently, GhostKiller and other highly knowledgeable managers are leading Anka Red Team. They call themselves the Turkish Cyber Army and follow the path of Atatürk. Their slogan is "Anytime we want, anywhere we want" The number of current members is constantly changing, so the exact number is unknown. They are quite secretive and engage in covert activities. In particular, Assault Teams receive extensive coverage in the media and press because they carry out attacks that Turkey can be proud of. TurkHackTeam's pro-government stance demonstrates that Turkey's planned nuclear energy facilities will not pose a potential threat.
TurkHackTeam's known widespread attacks:
On October 14, 2009, they hacked Domino's Pizza.
On January 27, 2012, the United Nations Development Program website was attacked.
On July 13, 2012, they attacked the Elysée Palace, the French presidential palace.
On September 11, 2012, UNESCO was hacked by them.
On September 14, 2012, they hacked a subdomain belonging to CERN.
On December 14, 2012, NATO's domain was attacked.
On April 15, 2015, they attacked the Vatican.
On April 24, 2015, the official websites of Armenia were attacked.
On May 25, 2015, many businesses in Egypt were attacked in protest of the death sentence of Mohammed Morsi, Egypt's first elected President.
On June 5, 2015, they hacked The Guardian, a British newspaper.
On June 17, 2015, under the "Fetih Operation," 1702 sites, including well-known brands and European states, were hacked.
On September 28, 2015, under the leadership of Veteran 7, the leader of the attack teams, the "Memleket Operation" hacked 4100 sites.
On December 25, 2015, parallel to attacks on Russia, attacks on sites were carried out in 2024.
On January 21, 2016, a member with the codename Th3Sehzade hacked 5100 websites simultaneously.
On August 30, 2016, 1781 US websites operated by Veteran 7, a leader of TurkHackTeam, were attacked by the "VICTORY OPERATION."
On September 19, 2016, the personal account and Facebook page of HDP deputy Mehmet Emin Adıyaman were attacked by Mrjava, BH80, and YaşasizDenek codenamed administrators.
On March 8, 2021, during the diplomatic crisis between the Republic of Turkey and Armenia and Greece, the Group, under the leadership of Veteran 7, blocked many official websites of Armenia and Greece, placed its own logo on the homepages of some sites, and seized documents from the databases of the two countries' governments.
On March 3, 2022, MIT University was attacked by a hacker named GhostKiller, a part of the Phoenix Red Team.
On March 8, 2022, the MTV Channel was attacked by a hacker named P4$A, a part of AnkaRedTeam.
On March 10, 2022, the Premier League website was hacked by the hacker P4$A.
On March 26, 2022, the HAWAR news agency was attacked by 'BOYBOX,' a member of the Anka Attack Team (Phoenix Red Team).
On March 30, 2022, FIFA suffered a heavy blow from the Attacking Teams Management unit.
On April 6, 2022, the defense and attack team "Anka Red Team," coordinated by Veteran 7 and GECEGEZEN, officially registered it with Zone-H, discovered a vulnerability in the Outlook.com subdomain, and hacked it.
On October 29, 2022, the attack teams led by GhostKiller, under the leadership of Veteran 7, carried out an operation by hacking more than 600 websites and seizing more than 1 million data.
On October 30, 2022, the flag of Turkey (ncpa5s4.png) was placed on the website of the so-called Kurdistan University, which supports the Kurdish terrorist organization (PKK/YPG).
As an official parade
it passed so beautifully before our eyes, didn't it?
Ayyıldız Tim

A hacker group founded in New Zealand in 2002 gained notoriety by hacking the U.S. Department of Defense website. Members of the group, who declare themselves patriots, are now in confrontation with Anonymous, who have declared war on Turkey. Ayyıldız Tim has carried out attacks on U.S., China, and Israel government websites. At the same time, it is believed that many websites belonging to the Syrian government have been hacked by Ayyıldız Tim. Ayyıldız Tim's defense of Turkey against Anonymous, especially in light of its recent attacks on Nuclear Energy and Cybersecurity in Turkey, demonstrates that Ayyıldız Tim poses no threat to the future cybersecurity of Turkey's planned nuclear facility.
Kıyamet Lejyonu

Legion of Doom, one of the oldest hacking groups, was founded in 1980 and ceased its activities in the 2000s. While the identities of some group members have been revealed, many, including the founder known as "Lex Luthor," remain unknown. The group was formed after a confrontation between Lex Luthor and another hacking group called Masters of Deception. The "Great Accord" between the Masters of Deception and Legion of Doom marked the beginning of what is known as the "Hacker Wars." Known for phone phreaking, the group targeted various government institutions and struck fear into the U.S. government.
Anonymous, whose exact founding date is unknown but announced its existence in 2008, is one of the largest hacking groups to date. Unlike other hacking groups, Anonymous conducts hack attacks for political purposes and has a close association with 4chan. Members of Anonymous, who choose to use "V for Vendetta" masks as their symbols, have been involved in numerous major hack attacks. The group's motive is not to steal or make money through hacking operations but to achieve its goals. Anonymous has successfully aided in the apprehension of a child predator and the resolution of a rape case, working voluntarily without direct involvement with the police. Despite having many members, Anonymous is driven by a single ideology and boasts millions of supporters. Anonymous transcends religious, linguistic, or national boundaries, engaging with the country they interact with in its language and actively opposing racist attitudes.
Kertenkele Mürettebatı

The group known as Lizard Squad, also referred to as "Black Hat hackers," gained notoriety for conducting Distributed Denial of Service (DDoS) attacks on gaming-related systems and websites. Although it was founded in 2014 with a focus on League of Legends, the group carried out DDoS attacks on networks, Destiny, Xbox, PlayStation Live, and even North Korean government websites. This hacker group, which primarily favored DDoS attacks, is believed to consist of only 7 members according to what is known.
Aldatma Ustaları

Masters of Deception, one of the oldest hacker groups, has been around since the early 1980s. Most of its members remain anonymous, and they share the information they acquire through their private ranking system. While some of this information is shared with the public over the internet, others are highly confidential. In 1993-1994, five members of the group were arrested with the efforts of the FBI and the Secret Service. Some were temporarily released, while others were sent to prison. Phiber Optik (real name Mark Abene), one of the group's earliest members, was among those imprisoned.
RedHack
, on the other hand, is one of the most well-known hacker groups in Turkey. The group's leader claimed in one of their interviews that RedHack was founded in May 1997. RedHack describes its ideology as using hacking for a fair, equal, and minimally exploitative order and world. RedHack consists of members who embrace Marxist and socialist ideologies. In February 2012, the hacker group successfully took over the website of the Ankara Police Department, gaining significant attention. RedHack has many members, but only 12 core members. Their motto is "If you eat rights, you will hack rights." RedHack often hacks the websites of government institutions and law enforcement agencies and has also assisted in closing and apprehending pedophiles' accounts. RedHack hacked the websites of three different milk companies to protest against the poisoning of hundreds of students and the distribution of milk to students. This hack received substantial support from social media users.
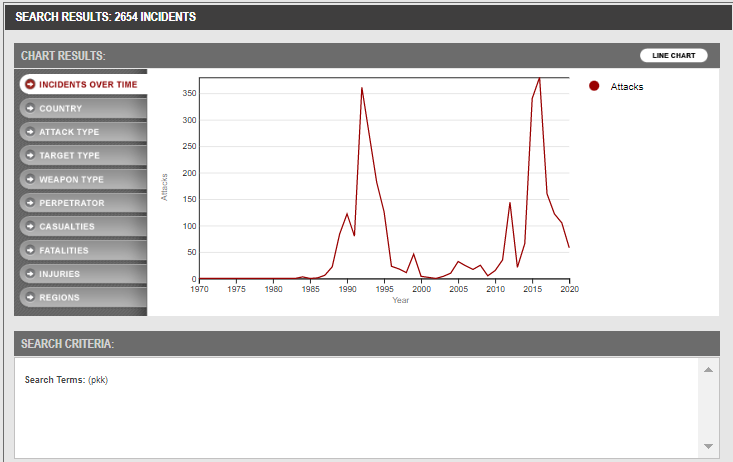
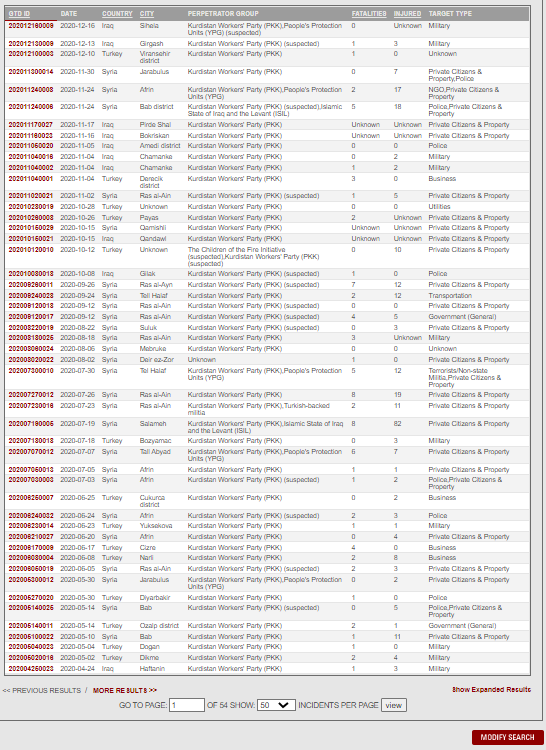
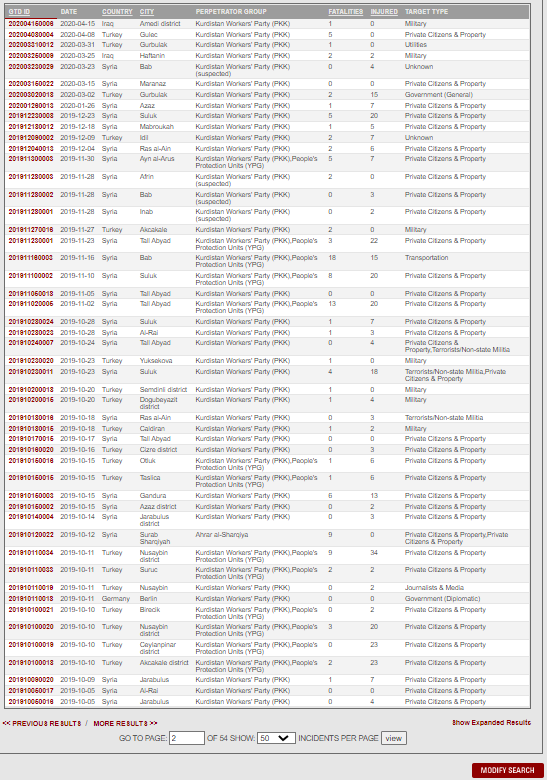
APPENDIX 1 - Global Terrorism Database
The graph below shows some of the terrorist attacks on the Republic of Turkey over the past 50 years, from 1970 to 2020. The two highest points on the graph are attacks that occurred in 1992 and 2016. Below this graph, there is a list of terrorist attacks carried out by the PKK terrorist organization only between 2018 and 2020. Cyberattacks have also increased in the last 20 years in parallel with this trend and are expected to continue to rise.
Soruce: @Zoptik https://www.turkhackteam.org/konular/siber-terorizm-ve-etik-korsanlik.2039102/#post-9854357
Son düzenleme:





