Step 1 Fire Up Kali & Open Crunch
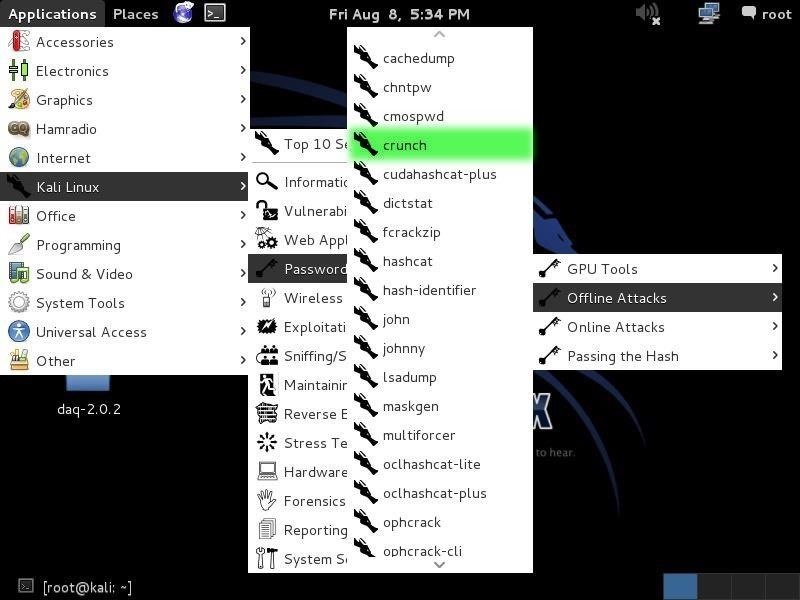
Let's start by firing up Kali and opening crunch by going to Applications -> Kali Linux -> Password Attacks -> Offline Attacks -> crunch.
This will open the crunch screen like that below.
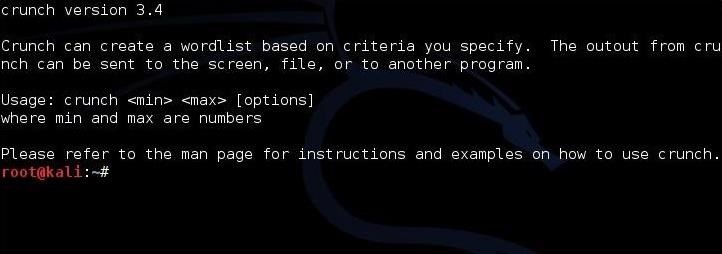
Unlike many other hacking applications, crunch doesn't provide us with much info in its opening screen. I believe that's because crunch, although relatively simple to work with initially, has so many sophisticated options that the developer has put much of the information in man pages.
Step 2 The Crunch Syntax
The basic syntax for crunch looks like this:
Now, let's go over what's included in the syntax above.
Step 3 The Crunch Manual
Let's go to the man pages for crunch by typing:
This should open the manual pages for crunch like that below. The developers of crunch have packed these pages with a lot of info on how to get the most out of crunch.
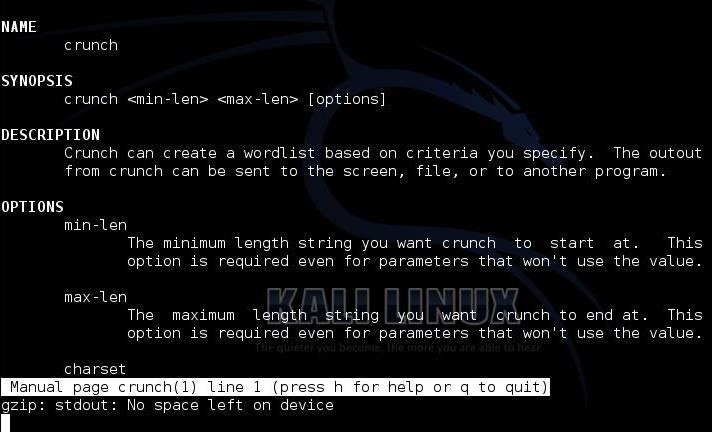
If we page down a bit in these man pages, we will come to this page (notice at the bottom, it says we are at line 70).
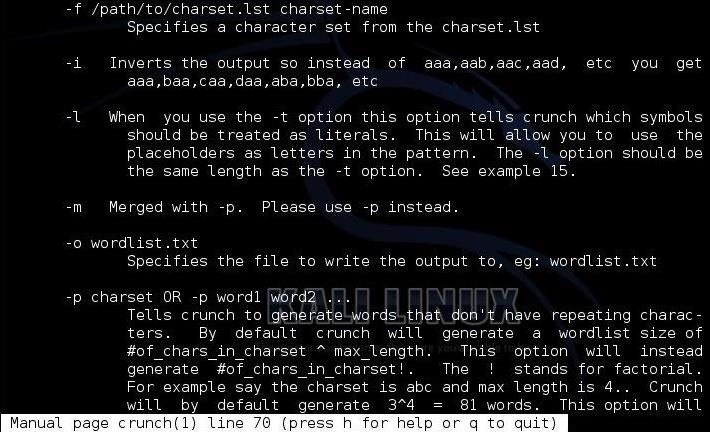
At the top we see the -f switch. This switch allows us to choose the character set we want to use to generate our wordlist. The syntax is:
Here we tell crunch where the charset.lst is with the full path and then select a particular character set from that list. In Kali, the charset.lst is at:
Step 4 Create Some Simple Wordlists
Let's start by generating some simple wordlists for password cracking. Let's assume that we know the company has passwords between 4 and 8 characters. We can generate all the possibilities in crunch by typing:
Where the first number (4) is the shortest word length and the second (8) is the longest word length.
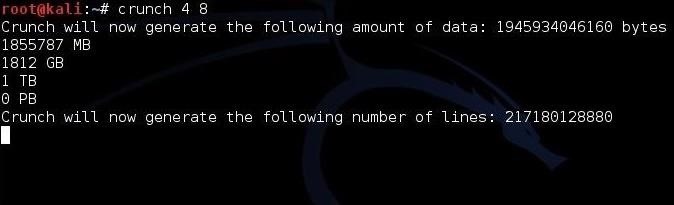
When we execute this statement, crunch estimates how large the file will be (1812 GB) and then begins to generate the list.
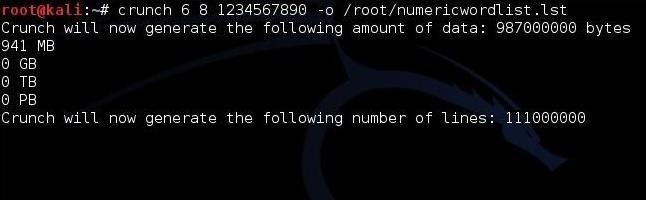
What if we knew that the target always used number passwords between 6 and 8 characters? We could generate a complete list of password possibilities meeting this criteria and send them to a file in the root user's directory called numericwordlist.lst by typing:
If we knew that the target's birthday was July 28 and they likely used that date (people often use their birthdates in their passwords to make it easier to remember) at the end of a ten character password? We could generate all the possibilities of ten-character passwords that end with 0728 and send the output to a file in the root user's directory named birthdaywordlist.lst, by typing:
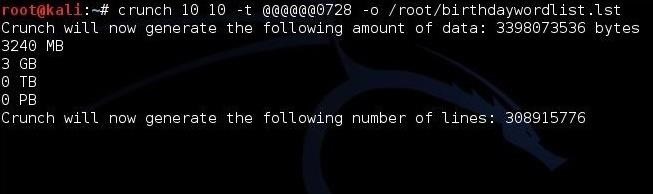
The @ sign is use to represent a wildcard of all possibilities, while the literals "0728" represent the fixed values.
Step 5 Complex Wordlists with Crunch
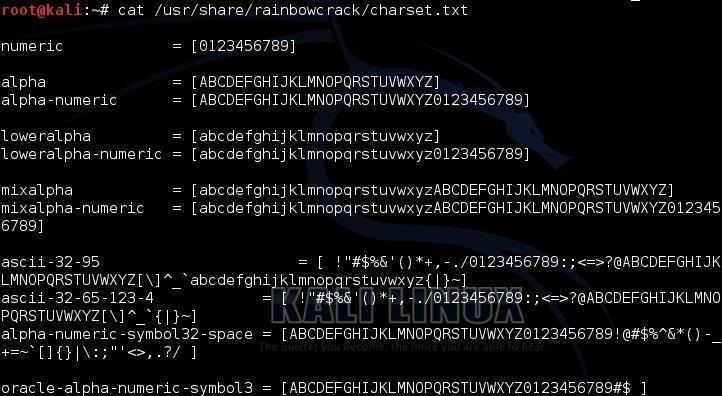
One of the beauties of crunch is the ability to select a specific character set or create your own character set for generating your password list. If we know the likely character set the target is using for their password, we can select the character set to generate our password list. We can find the choice of character sets at:
Now, if we know that our target is using an eight character password with only alphabetic characters, we can generate a list of all the possibilities in crunch with the command:
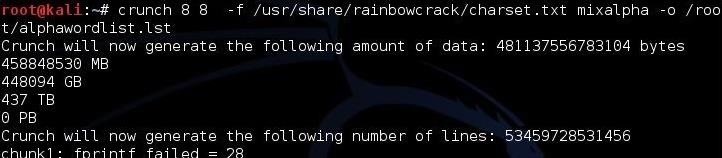
This will generate all the 8-character passwords using only the alphabetic characters (no numbers or special characters) and storing them in a file called alphawordlist.lst in the root user's directory.
When cracking passwords, there are multiple methods of cracking unknown passwords. These include dictionary, rainbow table, brute force and others. If we know that parameters of the password or know something about the target and their possible passwords (birthday, pet names, spouse, etc.), crunch can be a very useful tool for generating specific wordlists to be used in a dictionary-like attack.
Let's start by firing up Kali and opening crunch by going to Applications -> Kali Linux -> Password Attacks -> Offline Attacks -> crunch.

This will open the crunch screen like that below.

Unlike many other hacking applications, crunch doesn't provide us with much info in its opening screen. I believe that's because crunch, although relatively simple to work with initially, has so many sophisticated options that the developer has put much of the information in man pages.
Step 2 The Crunch Syntax
The basic syntax for crunch looks like this:
Kod:
kali > crunch <min> max<max> <characterset> -t <pattern> -o <output filename>Now, let's go over what's included in the syntax above.
Kod:
min = The minimum password length.
max = The maximum password length.
characterset = The character set to be used in generating the passwords.
-t <pattern> = The specified pattern of the generated passwords. For instance, if you knew that the target's birthday was 0728 (July 28th) and you suspected they used their birthday in their password (people often do), you could generate a password list that ended with 0728 by giving crunch the pattern @@@@@@@0728. This word generate passwords up to 11 characters (7 variable and 4 fixed) long that all ended with 0728.
-o <outputfile> = This is the file you want your wordlist written to.Step 3 The Crunch Manual
Let's go to the man pages for crunch by typing:
Kod:
kali > man crunchThis should open the manual pages for crunch like that below. The developers of crunch have packed these pages with a lot of info on how to get the most out of crunch.

If we page down a bit in these man pages, we will come to this page (notice at the bottom, it says we are at line 70).

At the top we see the -f switch. This switch allows us to choose the character set we want to use to generate our wordlist. The syntax is:
Kod:
-f /path/to/charset.lst <charactersetname>Here we tell crunch where the charset.lst is with the full path and then select a particular character set from that list. In Kali, the charset.lst is at:
Kod:
/usr/share/rainbowcrack/charset.lstStep 4 Create Some Simple Wordlists
Let's start by generating some simple wordlists for password cracking. Let's assume that we know the company has passwords between 4 and 8 characters. We can generate all the possibilities in crunch by typing:
Kod:
kali > crunch 4 8Where the first number (4) is the shortest word length and the second (8) is the longest word length.

When we execute this statement, crunch estimates how large the file will be (1812 GB) and then begins to generate the list.
What if we knew that the target always used number passwords between 6 and 8 characters? We could generate a complete list of password possibilities meeting this criteria and send them to a file in the root user's directory called numericwordlist.lst by typing:
Kod:
kali > crunch 6 8 1234567890 -o /root/numericwordlist.lst
If we knew that the target's birthday was July 28 and they likely used that date (people often use their birthdates in their passwords to make it easier to remember) at the end of a ten character password? We could generate all the possibilities of ten-character passwords that end with 0728 and send the output to a file in the root user's directory named birthdaywordlist.lst, by typing:
Kod:
kali > crunch 10 10 -t @@@@@@0728 -o /root/birthdaywordlist.lst
The @ sign is use to represent a wildcard of all possibilities, while the literals "0728" represent the fixed values.
Step 5 Complex Wordlists with Crunch
One of the beauties of crunch is the ability to select a specific character set or create your own character set for generating your password list. If we know the likely character set the target is using for their password, we can select the character set to generate our password list. We can find the choice of character sets at:
Kod:
/usr/share/rainbowcrack/charset.txt
Now, if we know that our target is using an eight character password with only alphabetic characters, we can generate a list of all the possibilities in crunch with the command:
Kod:
kali > crunch 8 8 -f /usr/share/rainbowcrack/charset.txt mixalpha -o /root/alphawordlist.lst
This will generate all the 8-character passwords using only the alphabetic characters (no numbers or special characters) and storing them in a file called alphawordlist.lst in the root user's directory.
When cracking passwords, there are multiple methods of cracking unknown passwords. These include dictionary, rainbow table, brute force and others. If we know that parameters of the password or know something about the target and their possible passwords (birthday, pet names, spouse, etc.), crunch can be a very useful tool for generating specific wordlists to be used in a dictionary-like attack.






