- 21 Eki 2015
- 477
- 1
First of all Hello. We will set up TCP and UDP Connections and Testing with Netcat in VPS.

Linux known to have a large number of mature, useful command-line utilities in most distributions. Qualified system administrators can do most of their work using built-in tools without the need of install additional software.
Often called the Swiss networking tools knife, this versatile command helps you monitor, test and send network connections. It automatically monitors network connections, making it easy to gather information.
We will discover this in an Ubuntu 12.04 VPS, but netcat should be available on almost all modern Linux distributions. Ubuntu comes with the BSD variant of netcat. Other versions may not work differently or offer other options.

General Syntax
By default, netcat works by starting a TCP connection to the remote host.
The most basic Syntax
This will start TCP on the host defined in the specified port number. This basically works in a similar way to the old Linux telnet command. Our connection is completely unencrypted.
If you want to send a UDP packet instead of initiating a TCP connection, you can use the -u option.
You can specify a port range by putting a hyphen between the first and last.
This is often used with some additional flags.
In most systems, we can use netcat or NC interchangeably. They are nicknames for the same command.

Port Scanning with Netcat
How to use Netcat for Port Scanning?
One of the most common uses of netcat is the port scanner. While Netcat is probably not the most advanced tool for business(nmap is a better choice in most cases), but it can perform simple port scans to easily identify open ports.
We do this by specifying a set of ports to scan, along with the option to perform a scan instead of starting a connection as we did above.
We can scan up to 1000 ports by giving the following command.
With the -z option, we have also selected the -v option to tell netcat to provide more detailed information.
The output will look like this:
As you can see, this provides a lot of information and tells you whether the scan for each port was successful.
If you are using a domain name, you will need to use this form.
However, your scan will be much faster if you know the IP address you need. Then you can use the -n flag to indicate that you dont need to resolve the IP address by using DNS.
The returned messages are actually sent to the standart error. We can send standart error messages to the standart output, this allows us to filter results more easily.
We will redirect the standart error to the standart output using the syntax 2>&1bash. Then we will filter the results with grep:
Here we can see that the only port open on the remote computer in the range of 1 1000 is port 22 which is the traditional SSH port.

How to communicate with Netcat?
Netcat isnt limited to sending TCP and UDP packets. It can also listen on a port for connections and packets. This gives us the opportunity to link two netcat instances in a client-server relationship.
A distinction that only relates to which computer is the server and which client is during initial configuration. Once the connection is established the communication is exactly the same in both directions.
On a machine, you can tell netcat to listen on a specific port for connections. We can do this by providing the -l parameter and selecting a port:
This will tell netcat to listen for TCP connections on port 4444. As a Normal (non-rooted) user, you cant open any ports under 1000 as a security measure.
On a second server, we can connect to the first machine in the port number we selected. We are doing it the way we have connected before:
It will look like nothing happened. However, you can now send messages to both sides of the connection and these messages will appear at the both ends.
Write a message and press ENTER. It will appear on both the local and the remote screen. This will work in the opposite direction as well.
Hen you are finished transmitting messages, you can press CTRL-D to close the TCP connection.

Sending Files with Netcat
We can perform more useful tasks based on the previous sample.
As we establish a regular TCP connection, we can transfer almost any kind of information over this connection. It isnt limited to chat messages written by user.
We can use this information to convert netcat info a file transfer program.
Once again, we need to choose one end of the link to listen to the links. However instead of printing the information on the screen as we did in the last example, we will place all the information directly in a file:
Create a simple text file on the second computer by typing:
Now we can use this file as an input for the netcat connection to the listen computer. The file will be transmitted as if we wrote it interactively:
On the computer waiting for a connection, we can see that we have a new file named imported with the contents of the file we wrote to the other computer:
As you can see, by piping(dont know what he is talking) things, we can easily use this connection to transfer all kinds of things.
For example, when creating an unnamed tarball, we can transfer the entire directory by transfer it to the remote system an opening it to the remote directory.
At the end of the recipient, we can guess by writing a file that must be removed :
The finish line (-) means that the tar will run on the standart input piped from netcat over the network when a connection is made.
On the side of the directory content we want to transfer, we can package them into a tarball and send them to the remote computer via netcat:
This time, the dash in the tar command means to targe and compress the contents of the current array (as indicated by the wildcard) and write the result to the standard output.
Then this is written directly to the TCP connection, then it is taken from the other end and opened to the current directory of the remote computer.
This is just an example of transferring more complex data from one computer to another. Another common idea is to use the command to display a disk to one side and transfer it to a remote computer. We will not address that here.

Using Netcat As A Simple Web Server
We configure Netcat to listen for connections to communicate and transfer files. We can also use the same concept to run netcat as a very simple web server. This can be useful for testing the pages that you create.
First, lets make a simple HTML file on a server:
Here are some simple HTML that you can use in your file:
Save and close the file.
Without root privileges, you cant present this file on the default web port on Port 80.
We can select port 8888 as the normal user.
If you want to present this page once to check how it is displayed, you can run the following command:
Now you can access content in your browser by visiting:
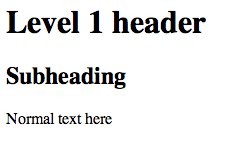
This will present the page and the netcat link will close. If you try to refr3sh page, the page will disappear:

We can wrap the last command in an infinite loop so that netcat can serve the page indefinitely:
This allows you to continue receiving the connection after the first connection is closed.
We can stop the loop by typing CTRL-C on the server.
This allows you to see how a page is viewed in the browser, but doesnt provide much more functionality.
You should never use this to deliver real websites. There is no security and simple things like connections dont work properly.

Conclusion
Now you should have a pretty good idea of what netcat can be used for. It is a versatile tool that can be useful for diagnosing problems and verifying that base-level functionality works correctly with TCP/UDP connections.
Using Netcat, you can easily communicate between different computer for fast interactions. Netcat tries to make network interactions between computers transparent by eliminating the complexity of creating connections.
Source: https://www.turkhackteam.org/web-se...sde-kurmak-ve-netcat-ile-test-etmek-icin.html

Linux known to have a large number of mature, useful command-line utilities in most distributions. Qualified system administrators can do most of their work using built-in tools without the need of install additional software.
Often called the Swiss networking tools knife, this versatile command helps you monitor, test and send network connections. It automatically monitors network connections, making it easy to gather information.
We will discover this in an Ubuntu 12.04 VPS, but netcat should be available on almost all modern Linux distributions. Ubuntu comes with the BSD variant of netcat. Other versions may not work differently or offer other options.

General Syntax
By default, netcat works by starting a TCP connection to the remote host.
The most basic Syntax
Kod:
[COLOR="Lime"]$ netcat [options] host port[/COLOR]This will start TCP on the host defined in the specified port number. This basically works in a similar way to the old Linux telnet command. Our connection is completely unencrypted.
If you want to send a UDP packet instead of initiating a TCP connection, you can use the -u option.
Kod:
[COLOR="lime"]$ netcat -u host port[/COLOR]You can specify a port range by putting a hyphen between the first and last.
Kod:
$ netcat host startport-endportThis is often used with some additional flags.
In most systems, we can use netcat or NC interchangeably. They are nicknames for the same command.

Port Scanning with Netcat
How to use Netcat for Port Scanning?
One of the most common uses of netcat is the port scanner. While Netcat is probably not the most advanced tool for business(nmap is a better choice in most cases), but it can perform simple port scans to easily identify open ports.
We do this by specifying a set of ports to scan, along with the option to perform a scan instead of starting a connection as we did above.
We can scan up to 1000 ports by giving the following command.
Kod:
$ netcat -z -v domain.com 1-1000With the -z option, we have also selected the -v option to tell netcat to provide more detailed information.
The output will look like this:
Kod:
output
nc: connect to domain.com port 1 (tcp) failed: Connection refused
nc: connect to domain.com port 2 (tcp) failed: Connection refused
nc: connect to domain.com port 3 (tcp) failed: Connection refused
nc: connect to domain.com port 4 (tcp) failed: Connection refused
nc: connect to domain.com port 5 (tcp) failed: Connection refused
nc: connect to domain.com port 6 (tcp) failed: Connection refused
nc: connect to domain.com port 7 (tcp) failed: Connection refused
Connection to domain.com 22 port [tcp/ssh] succeeded!As you can see, this provides a lot of information and tells you whether the scan for each port was successful.
If you are using a domain name, you will need to use this form.
However, your scan will be much faster if you know the IP address you need. Then you can use the -n flag to indicate that you dont need to resolve the IP address by using DNS.
Kod:
$ netcat -z -n -v 198.51.100.0 1-1000The returned messages are actually sent to the standart error. We can send standart error messages to the standart output, this allows us to filter results more easily.
We will redirect the standart error to the standart output using the syntax 2>&1bash. Then we will filter the results with grep:
Kod:
[COLOR="lime"]netcat -z -n -v 198.51.100.0 1-1000 2>&1 | grep succeeded[/COLOR]
Kod:
[COLOR="lime"]output
Connection to 198.51.100.0 22 port [tcp/*] succeeded![/COLOR]Here we can see that the only port open on the remote computer in the range of 1 1000 is port 22 which is the traditional SSH port.

How to communicate with Netcat?
Netcat isnt limited to sending TCP and UDP packets. It can also listen on a port for connections and packets. This gives us the opportunity to link two netcat instances in a client-server relationship.
A distinction that only relates to which computer is the server and which client is during initial configuration. Once the connection is established the communication is exactly the same in both directions.
On a machine, you can tell netcat to listen on a specific port for connections. We can do this by providing the -l parameter and selecting a port:
Kod:
$ netcat -l 4444This will tell netcat to listen for TCP connections on port 4444. As a Normal (non-rooted) user, you cant open any ports under 1000 as a security measure.
On a second server, we can connect to the first machine in the port number we selected. We are doing it the way we have connected before:
Kod:
$ netcat domain.com 4444It will look like nothing happened. However, you can now send messages to both sides of the connection and these messages will appear at the both ends.
Write a message and press ENTER. It will appear on both the local and the remote screen. This will work in the opposite direction as well.
Hen you are finished transmitting messages, you can press CTRL-D to close the TCP connection.

Sending Files with Netcat
We can perform more useful tasks based on the previous sample.
As we establish a regular TCP connection, we can transfer almost any kind of information over this connection. It isnt limited to chat messages written by user.
We can use this information to convert netcat info a file transfer program.
Once again, we need to choose one end of the link to listen to the links. However instead of printing the information on the screen as we did in the last example, we will place all the information directly in a file:
Kod:
netcat -l 4444 > received_fileCreate a simple text file on the second computer by typing:
Kod:
echo "Hello, this is a file" > original_fileNow we can use this file as an input for the netcat connection to the listen computer. The file will be transmitted as if we wrote it interactively:
Kod:
netcat domain.com 4444 < original_fileOn the computer waiting for a connection, we can see that we have a new file named imported with the contents of the file we wrote to the other computer:
Kod:
cat received_file
Kod:
output
Hello, this is a fileAs you can see, by piping(dont know what he is talking) things, we can easily use this connection to transfer all kinds of things.
For example, when creating an unnamed tarball, we can transfer the entire directory by transfer it to the remote system an opening it to the remote directory.
At the end of the recipient, we can guess by writing a file that must be removed :
Kod:
netcat -l 4444 | tar xzvf -The finish line (-) means that the tar will run on the standart input piped from netcat over the network when a connection is made.
On the side of the directory content we want to transfer, we can package them into a tarball and send them to the remote computer via netcat:
Kod:
tar -czf - * | netcat domain.com 4444This time, the dash in the tar command means to targe and compress the contents of the current array (as indicated by the wildcard) and write the result to the standard output.
Then this is written directly to the TCP connection, then it is taken from the other end and opened to the current directory of the remote computer.
This is just an example of transferring more complex data from one computer to another. Another common idea is to use the command to display a disk to one side and transfer it to a remote computer. We will not address that here.

Using Netcat As A Simple Web Server
We configure Netcat to listen for connections to communicate and transfer files. We can also use the same concept to run netcat as a very simple web server. This can be useful for testing the pages that you create.
First, lets make a simple HTML file on a server:
Kod:
nano index.htmlHere are some simple HTML that you can use in your file:
Kod:
index.html
<html>
<head>
<title>Test Page</title>
</head>
<body>
<h1>Level 1 header</h1>
<h2>Subheading</h2>
<p>Normal text here</p>
</body>
</html>Save and close the file.
Without root privileges, you cant present this file on the default web port on Port 80.
We can select port 8888 as the normal user.
If you want to present this page once to check how it is displayed, you can run the following command:
Kod:
printf 'HTTP/1.1 200 OK\n\n%s' "$(cat index.html)" | netcat -l 8888Now you can access content in your browser by visiting:
Kod:
http://server_IP:8888
This will present the page and the netcat link will close. If you try to refr3sh page, the page will disappear:

We can wrap the last command in an infinite loop so that netcat can serve the page indefinitely:
Kod:
$ while true; do printf 'HTTP/1.1 200 OK\n\n%s' "$(cat index.html)" | netcat -l 8888; doneThis allows you to continue receiving the connection after the first connection is closed.
We can stop the loop by typing CTRL-C on the server.
This allows you to see how a page is viewed in the browser, but doesnt provide much more functionality.
You should never use this to deliver real websites. There is no security and simple things like connections dont work properly.

Conclusion
Now you should have a pretty good idea of what netcat can be used for. It is a versatile tool that can be useful for diagnosing problems and verifying that base-level functionality works correctly with TCP/UDP connections.
Using Netcat, you can easily communicate between different computer for fast interactions. Netcat tries to make network interactions between computers transparent by eliminating the complexity of creating connections.
Source: https://www.turkhackteam.org/web-se...sde-kurmak-ve-netcat-ile-test-etmek-icin.html
Translator: Provido





