According to Statista, more than 3,5 billion people use a phone with Googles Android operating system daily.
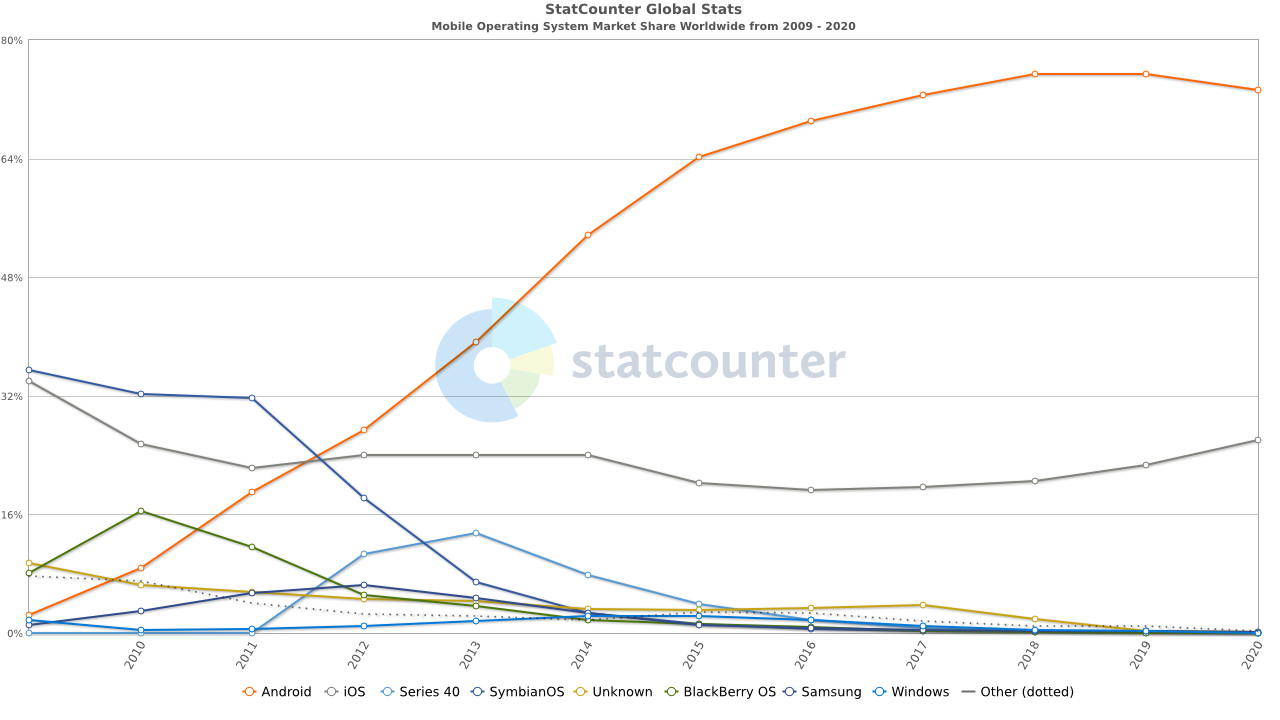
In just over than 10 years, Android has become the undisputed mobile operating system market leader with over 75% market share.
While Android has a core based on Open Source software, the conventional version of Android that you find on most smartphones also includes a set of proprietary libraries and APIs that are used by many mobile applications. This also locks users in the Google ecosystem.
Even if you arent using those apps on your Android phone or forgo adding a Google account , your device still engages with many of those Google services and Google powered features without your knowledge, in order to function correctly.
Most of these services are embedded in the apps you use daily right from the development phase. From receiving a notification from your banking app, to trying to locate where your taxi driver is while hailing a ride, the dependence on Google dominates the user experience.
Removing Googles Play Store can result in the phones key functionality not working. This in turn would prevent popular apps from running and would distort the user experience . You could rightfully go down the route of doing without Googles Services for example with a Linux phone. The downside is ending up with no apps at all. Another option is to use a custom ROM with an alternative app store like Fdroid that distributes only free and open source apps but you would be limited in terms of apps to choose from.
microG is a open source, free software re-implementation of Googles proprietary libraries.
Weve invited its creator and developer, Marvin Wißfeld, to explain more about the key implementation concepts behind microG.
Question: Can you tell us a bit more about you and your background?
Answer: I started programming when I was just 12 years old. Ive been contributing to open-source projects since 2010. I finished my Masters degree in Computer Science just two years ago. I very much enjoy tinkering with the Android operating system but am also involved in developments around the open IETF standard for instant messaging XMPP.

Q: How did the microG project start ?
I removed Google apps and services from my first smartphone in 2012. My main issue with CyanogenMod without Google services has been that the GPS was extremely slow, easily eating 23 percent of the battery time before being able to fix a l o c a t i o n. To solve this issue I developed an alternative to Googles network-based l o c a t i o n component. A few months later I desperately wanted to play a game that required to log-in with a Google account which required me to develop an alternative Google account manager component. These works laid the foundation of what microG is today, though it became a much larger project when Google started to provide the Play Services, an ever-growing collection of proprietary services.
Q: Do you work alone or do you have more developers on the project ?
I founded microG as an open-source project, accepting contributions from every interested developer. More than 50 individuals contributed code or translations. However, still more than 90% of the current codebase is written by myself.
Q: Please can you explain in layman terms how microG is able to simulate the Google services and get apps to run on Android smartphones?
The Android operating system allows developers to create apps that are not visible to end users but only act as a service that is accessed by other apps. The various Google services are provided through such service apps. When accessing those service apps, end-user applications do so via a special language that was pre-defined for this communication. microG looks and behaves exactly like the original Google service apps and understands the language that is spoken in such communication. This way its impossible for apps to find out if they run in a Google infrastructure or on a system using microG.
One key components of the looking like Google is the signature spoofing. All Android apps are cryptographically signed using the private key of their developer. Because private key signing the Google services is only in their hands, microG can not create a signature that looks like its from Google. Luckily, apps are not supposed to verify the cryptographic signature themselves, but only ask the operating system to do so. Thus, operating systems that support such signature spoofing, like /e/OS, can tell apps that they verified that microG is properly signed with a private key of Google, even if it isnt.
Q: Recently microG added optional support for the COVID-19 contact tracing framework. Please can you share details as to how this contact tracing framework works.
The Exposure Notifications API used by COVID-19 contact tracing apps provides four features to those apps:
Bluetooth Advertising: Your phone persistently broadcasts a so called Rolling Proximity Identifier (RPI) via Bluetooth. Every 10 minutes, your device generates a new RPI to be published, to make it impossible to track you. The RPIs are derived from a private key that is generated randomly once per day by your device. This derivation cryptographically guarantees that RPIs can not be linked to each other, except if you shared the private key.
Bluetooth Scanning: About every 5 minutes your phone scans for nearby Bluetooth devices that broadcast RPIs and stores the RPI together with a timestamp in a local database.
Key Sharing: When you have been tested positive for COVID-19, you can ask your phone to share your private keys of the last 14 days with the COVID-19 contact tracing app. Only with this private key is it possible for others to see if theyve been in contact with you for more than 10 minutes. The implementation of microG will make sure that this key sharing does not happen without explicit user consent.
Risk calculation: Based on the list of private keys shared by the companion app and the list of RPIs collected in the last 14 days, your phone checks if you have been in close contact with a person that reportedly was tested positive. Your phone computes a total risk score and provides information on the date and time, contact length, and signal strength of the exposure to the companion app. The companion app will not learn which keys or people were in close contact, neither will it get any insights on where the contact happened.
Before these features are enabled, microG asks the user for explicit consent. All of this happens locally on the device and no interaction with Google or Apple servers is required. Additionally, most governments agreed to make their companion app open-source so that they can be reviewed by the public that they do not include any unwanted data transmission beside the key sharing as described above.
Q: A number of users on the /e/ forum keep checking with us on how safe microG is as they see references to Google in the code or file names. How would you answer that question?
There are mainly two reasons why Google appears in the microG source code:
As I described above, microG has to speak a special language with apps using the services it provides. This language often contains the word Google. If microG didnt include the same words in the language, communication wouldnt be possible.
Some services of microG require that your device connects to a server from Google. The most prominent of such services is the push notification service. This service would be entirely impossible without your device getting push notification from Google, and thus your device has to talk with Google servers. However, all services of microG that require connecting to Google services are optional and can be turned off without issues for those services that do not need to connect to Google. It is important to note that as long as you are not signed into a Google account with microG, these server connections remain anonymous.
Q: Any plans of future modifications and enhancements for microG?
microG has a lot of room for adding more features and improving on the existing ones. Currently I am focusing on adding full support for a service called Firebase Authentication which is used in many apps during the login or registration process and thus if its missing, these applications fail when trying to log you in. The work on microG is never finished anyways: Google adds new proprietary services to Android every few months.
About the microG project: https://microg.org/
Source: https://edevelopers-blog.medium.com/microg-what-you-need-to-know-b213bf03565e
Turkish Version: https://www.turkhackteam.org/google-android/1974835-microg-hakkinda-bilmeniz-gerekenler.html
In just over than 10 years, Android has become the undisputed mobile operating system market leader with over 75% market share.

While Android has a core based on Open Source software, the conventional version of Android that you find on most smartphones also includes a set of proprietary libraries and APIs that are used by many mobile applications. This also locks users in the Google ecosystem.
Even if you arent using those apps on your Android phone or forgo adding a Google account , your device still engages with many of those Google services and Google powered features without your knowledge, in order to function correctly.
Most of these services are embedded in the apps you use daily right from the development phase. From receiving a notification from your banking app, to trying to locate where your taxi driver is while hailing a ride, the dependence on Google dominates the user experience.
Removing Googles Play Store can result in the phones key functionality not working. This in turn would prevent popular apps from running and would distort the user experience . You could rightfully go down the route of doing without Googles Services for example with a Linux phone. The downside is ending up with no apps at all. Another option is to use a custom ROM with an alternative app store like Fdroid that distributes only free and open source apps but you would be limited in terms of apps to choose from.
microG is a open source, free software re-implementation of Googles proprietary libraries.
Weve invited its creator and developer, Marvin Wißfeld, to explain more about the key implementation concepts behind microG.
Question: Can you tell us a bit more about you and your background?
Answer: I started programming when I was just 12 years old. Ive been contributing to open-source projects since 2010. I finished my Masters degree in Computer Science just two years ago. I very much enjoy tinkering with the Android operating system but am also involved in developments around the open IETF standard for instant messaging XMPP.

Q: How did the microG project start ?
I removed Google apps and services from my first smartphone in 2012. My main issue with CyanogenMod without Google services has been that the GPS was extremely slow, easily eating 23 percent of the battery time before being able to fix a l o c a t i o n. To solve this issue I developed an alternative to Googles network-based l o c a t i o n component. A few months later I desperately wanted to play a game that required to log-in with a Google account which required me to develop an alternative Google account manager component. These works laid the foundation of what microG is today, though it became a much larger project when Google started to provide the Play Services, an ever-growing collection of proprietary services.
Q: Do you work alone or do you have more developers on the project ?
I founded microG as an open-source project, accepting contributions from every interested developer. More than 50 individuals contributed code or translations. However, still more than 90% of the current codebase is written by myself.
Q: Please can you explain in layman terms how microG is able to simulate the Google services and get apps to run on Android smartphones?
The Android operating system allows developers to create apps that are not visible to end users but only act as a service that is accessed by other apps. The various Google services are provided through such service apps. When accessing those service apps, end-user applications do so via a special language that was pre-defined for this communication. microG looks and behaves exactly like the original Google service apps and understands the language that is spoken in such communication. This way its impossible for apps to find out if they run in a Google infrastructure or on a system using microG.
One key components of the looking like Google is the signature spoofing. All Android apps are cryptographically signed using the private key of their developer. Because private key signing the Google services is only in their hands, microG can not create a signature that looks like its from Google. Luckily, apps are not supposed to verify the cryptographic signature themselves, but only ask the operating system to do so. Thus, operating systems that support such signature spoofing, like /e/OS, can tell apps that they verified that microG is properly signed with a private key of Google, even if it isnt.
Q: Recently microG added optional support for the COVID-19 contact tracing framework. Please can you share details as to how this contact tracing framework works.
The Exposure Notifications API used by COVID-19 contact tracing apps provides four features to those apps:
Bluetooth Advertising: Your phone persistently broadcasts a so called Rolling Proximity Identifier (RPI) via Bluetooth. Every 10 minutes, your device generates a new RPI to be published, to make it impossible to track you. The RPIs are derived from a private key that is generated randomly once per day by your device. This derivation cryptographically guarantees that RPIs can not be linked to each other, except if you shared the private key.
Bluetooth Scanning: About every 5 minutes your phone scans for nearby Bluetooth devices that broadcast RPIs and stores the RPI together with a timestamp in a local database.
Key Sharing: When you have been tested positive for COVID-19, you can ask your phone to share your private keys of the last 14 days with the COVID-19 contact tracing app. Only with this private key is it possible for others to see if theyve been in contact with you for more than 10 minutes. The implementation of microG will make sure that this key sharing does not happen without explicit user consent.
Risk calculation: Based on the list of private keys shared by the companion app and the list of RPIs collected in the last 14 days, your phone checks if you have been in close contact with a person that reportedly was tested positive. Your phone computes a total risk score and provides information on the date and time, contact length, and signal strength of the exposure to the companion app. The companion app will not learn which keys or people were in close contact, neither will it get any insights on where the contact happened.
Before these features are enabled, microG asks the user for explicit consent. All of this happens locally on the device and no interaction with Google or Apple servers is required. Additionally, most governments agreed to make their companion app open-source so that they can be reviewed by the public that they do not include any unwanted data transmission beside the key sharing as described above.
Q: A number of users on the /e/ forum keep checking with us on how safe microG is as they see references to Google in the code or file names. How would you answer that question?
There are mainly two reasons why Google appears in the microG source code:
As I described above, microG has to speak a special language with apps using the services it provides. This language often contains the word Google. If microG didnt include the same words in the language, communication wouldnt be possible.
Some services of microG require that your device connects to a server from Google. The most prominent of such services is the push notification service. This service would be entirely impossible without your device getting push notification from Google, and thus your device has to talk with Google servers. However, all services of microG that require connecting to Google services are optional and can be turned off without issues for those services that do not need to connect to Google. It is important to note that as long as you are not signed into a Google account with microG, these server connections remain anonymous.
Q: Any plans of future modifications and enhancements for microG?
microG has a lot of room for adding more features and improving on the existing ones. Currently I am focusing on adding full support for a service called Firebase Authentication which is used in many apps during the login or registration process and thus if its missing, these applications fail when trying to log you in. The work on microG is never finished anyways: Google adds new proprietary services to Android every few months.
About the microG project: https://microg.org/
Source: https://edevelopers-blog.medium.com/microg-what-you-need-to-know-b213bf03565e
Turkish Version: https://www.turkhackteam.org/google-android/1974835-microg-hakkinda-bilmeniz-gerekenler.html
Son düzenleme:






