Hello everyone, today I will talk about "Malware Analysis" and the "Tools I Use," which are frequently asked about.

Firstly, what is malware? How does it spread? How many types of analysis methods are there? You should look into this topic to learn more:
Now, let's talk about where we will conduct these malware analyses.
Malware analyses are generally conducted in virtual PC environments such as (VM VirtualBox - VMware Workstation). They can also be done on operating systems like Linux. My recommendation is to do it via a virtual PC. The operating system you install is very important. I had installed "Windows 7" on my virtual machine. I also recommend conducting your analyses on Windows 7.
What is VM VirtualBox - VMware Workstation and how to install it can be learned from this video:
Do not conduct analysis or any other tasks on your real computer under any circumstances. Opening a trojan can cause significant damage to your computer. Be careful.
Even when I conduct analysis on a virtual PC, sometimes I encounter blue screen errors, that's how serious it can be
And remember, the most effective analysis method is dynamic. It is the type of analysis where we open the program and see what is happening.
First, let's create a server from a DarkComet RAT.
Our server is ready. Now let's identify and analyze the programs.

First, let's do our static analysis.
BinText
A small, very fast, and powerful text extractor that will particularly interest programmers. It can extract text from any file type and includes the ability to find plain ASCII text, Unicode (double-byte ANSI) text, and Resource strings, optionally in "advanced" view mode, providing useful information for each item. Comprehensive filtering helps prevent the listing of unwanted text. The collected list can be searched, and saved to a separate file in plain text or informative table format.
Here, we can see the "strings" values inside the program. Not bad for preliminary analysis.
CFF Explorer
CFF Explorer is designed to make it as easy as possible to review the internal structure of an executable application without missing any details. This application not only includes a range of tools that can assist engineers, but also programmers in reverse engineering. It offers a multi-file environment and a customizable interface.
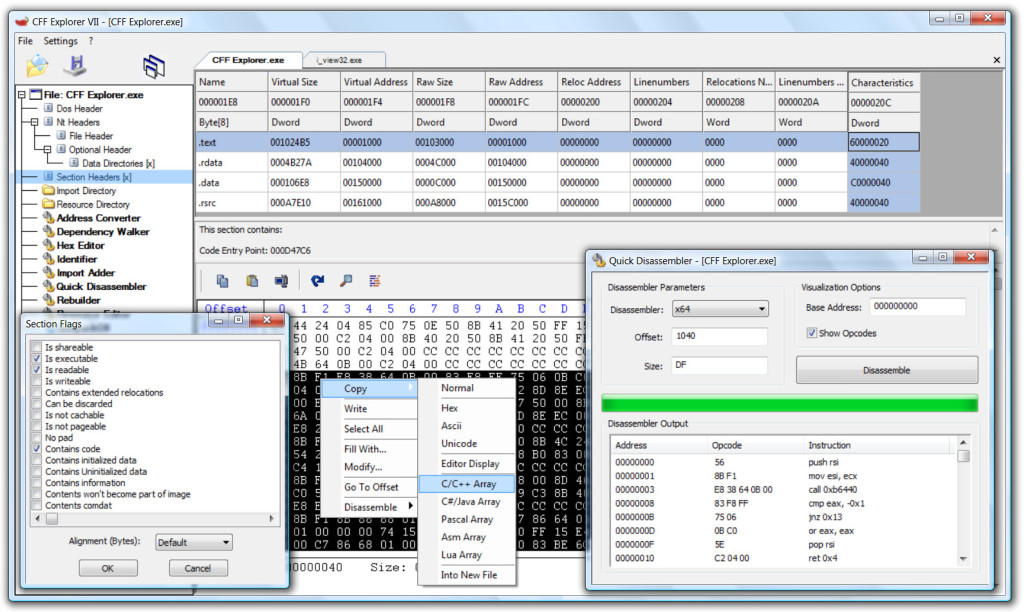
The purpose here is to see the DLL files running inside the program and to look at the data string values.
Remember, the more DLLs there are, the more processing there is on Windows.
Example: Avdapi.dll is used for registry edit operations, etc.
Exeinfo PE
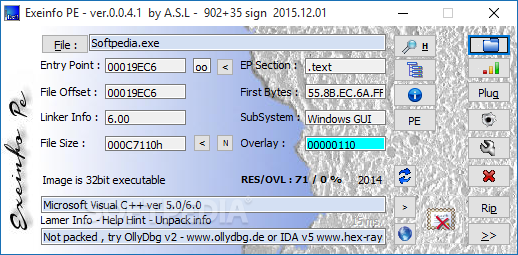
Exeinfo PE is a program that allows you to verify .exe files and check all their properties. Additionally, you can rename the file, directly open or delete the .exe file. Another provided information is the full size and entry point. In short, you can access dozens of different options to edit any Windows executable file.
All the analyses we've done so far were "static" analyses.
Now, we are moving on to dynamic analysis. (That is, we are running the program and analyzing it.)
OllyDbg
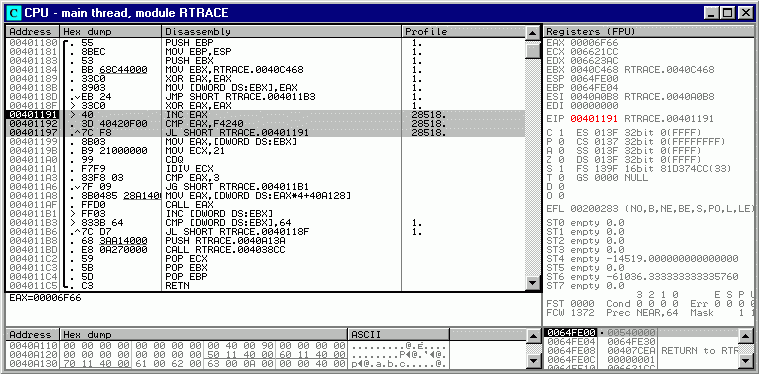
OllyDbg is commonly used for reverse engineering of programs. It is often used to crack software made by other developers. Due to its ease of use and availability, it is primarily used as the tool of choice for reverse engineering; it can be used by any 32-bit executable debugger and can be edited in real-time in bitcode/assembly. It is useful for programmers to ensure their programs work as intended and for analyzing malicious software.
As you can see, when we run our "server" with "ollydbg," it shows us our DNS address, port, the copied folder path inside, and any error message if present.
Autoruns
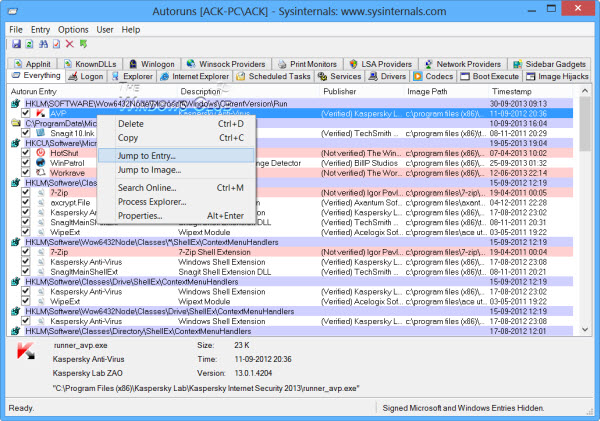
Autoruns is a free system startup management tool developed by Microsoft. It is a successful and easy-to-use application where you can directly intervene in the startup folder, Run, RunOnce, and other Registry values where programs loaded at the beginning of your operating system are determined. Additionally, in Autoruns, you will find Internet Explorer toolbars, extensions, automatically starting system services, and much more.
FileAlyzer
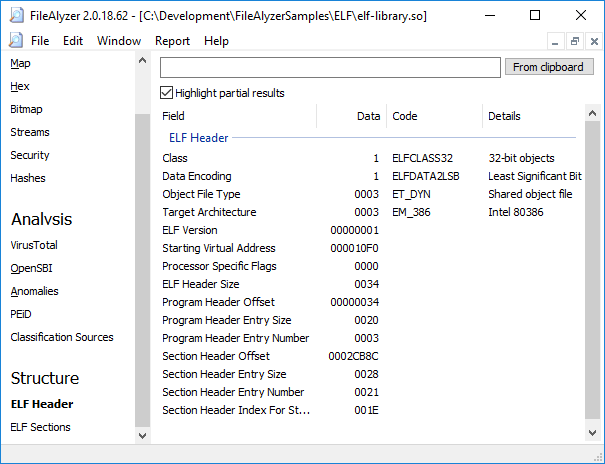
If you want to learn more about the inner life of files, FileAlyzer is the tool you urgently need!
FileAlyzer displays basic file contents for interpreted complex file structures that help you understand the purpose of a file, a standard hex viewer, and various customized screens.
It also supports the creation of advanced file signatures with OpenSBI - you can find the right features to write your own optimized malware file signatures with FileAlyzer!
As you can see, when we run the "Superantispyware.exe" program we named "binder," it shows us information about what will be added to the startup, deleted, etc.
It is a very nice and useful "File Analysis" program. You can see almost everything through this program...
Process Hacker
Process Hacker is a free and open-source process viewer program. Process Hacker shows you which programs or processes are using CPU and memory on your computer. With the program, you can easily terminate any program or process that you consider unnecessary or harmful. We can say that Process Hacker is a highly advanced version of Windows Task Manager.
CurrPorts

CurrPorts is network monitoring software that displays a list of all currently open TCP/IP and UDP ports on your local computer. For each port listed, it provides information about the process that opened the port, such as the process name, full path of the process, and version information of the process (product name, file description, etc.).
Additionally, CurrPorts allows you to close unwanted TCP connections, terminate the process that opened the ports, and save TCP/UDP port information to an HTML file, XML file, or tab-delimited text file.
CurrPorts also automatically highlights suspicious TCP/UDP ports in pink for unidentified applications (applications without version information and icons).
Since I will be testing from my own computer, I used "127.0.0.1" localhost. You will see the port number and IP address of the victim.
Regshot
Regshot is a dynamic malware analysis tool that allows an analyst to capture before-and-after snapshots of the Windows Registry. Typically, this is used to capture the system's snapshot before and immediately after running malware.
The purpose is to identify changes made in the registry by the malware. This indicates what the malware might be capable of, specifying any additional files dropped or any other Indicators of Compromise (IOCs).
Process Monitor
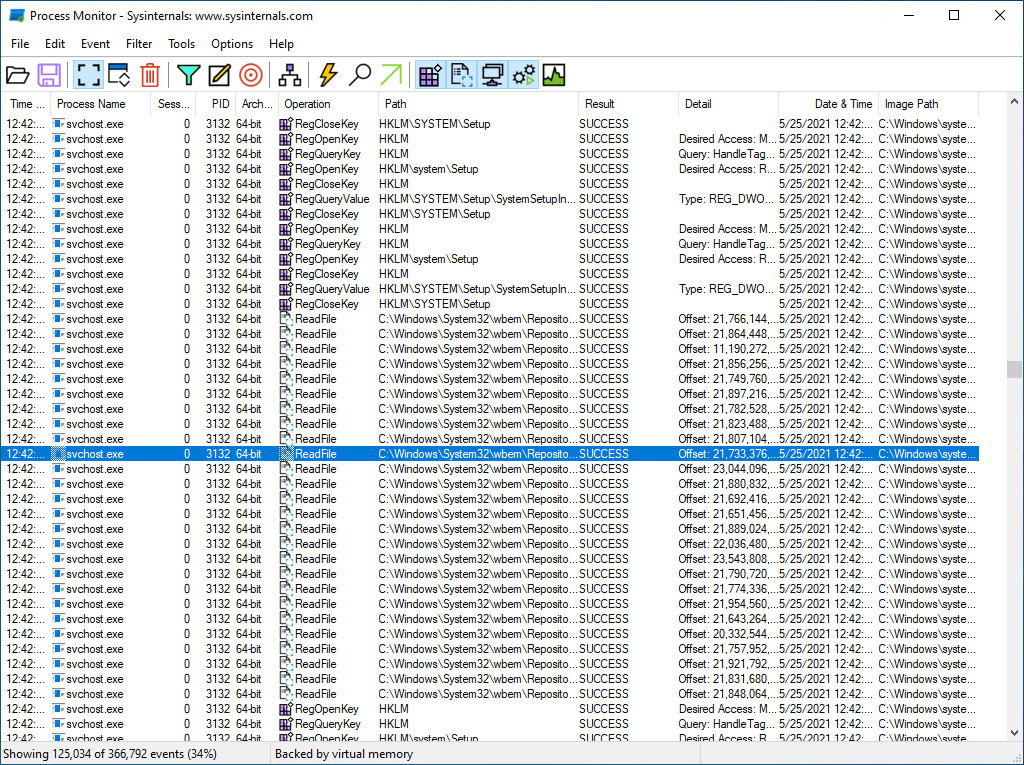
Process Monitor is an advanced monitoring tool for Windows that displays real-time file system, Registry, and process/thread activity. It combines the features of two former Sysinternals utility programs, Filemon and Regmon, and adds a rich and non-destructive filtering, comprehensive event properties such as session IDs and user names, reliable process information, integrated symbol-supported full thread stacks, and a comprehensive development list. For each process, it provides a concurrent log of activity to a file and more. Its unique powerful features make Process Monitor a fundamental utility in your troubleshooting and malware detection toolset on your system.
These explanations are brief and to the point. If you delve into them, you can make much better analyses over time.
The more you work, the more you learn.
Click here to download all the tools.
Source: Malware Analiz Araçlarım Ve Kullanımları // Black Turtle

Firstly, what is malware? How does it spread? How many types of analysis methods are there? You should look into this topic to learn more:
Now, let's talk about where we will conduct these malware analyses.
Malware analyses are generally conducted in virtual PC environments such as (VM VirtualBox - VMware Workstation). They can also be done on operating systems like Linux. My recommendation is to do it via a virtual PC. The operating system you install is very important. I had installed "Windows 7" on my virtual machine. I also recommend conducting your analyses on Windows 7.
What is VM VirtualBox - VMware Workstation and how to install it can be learned from this video:
Do not conduct analysis or any other tasks on your real computer under any circumstances. Opening a trojan can cause significant damage to your computer. Be careful.
Even when I conduct analysis on a virtual PC, sometimes I encounter blue screen errors, that's how serious it can be
And remember, the most effective analysis method is dynamic. It is the type of analysis where we open the program and see what is happening.
First, let's create a server from a DarkComet RAT.
Our server is ready. Now let's identify and analyze the programs.

First, let's do our static analysis.
BinText
A small, very fast, and powerful text extractor that will particularly interest programmers. It can extract text from any file type and includes the ability to find plain ASCII text, Unicode (double-byte ANSI) text, and Resource strings, optionally in "advanced" view mode, providing useful information for each item. Comprehensive filtering helps prevent the listing of unwanted text. The collected list can be searched, and saved to a separate file in plain text or informative table format.
Here, we can see the "strings" values inside the program. Not bad for preliminary analysis.
CFF Explorer
CFF Explorer is designed to make it as easy as possible to review the internal structure of an executable application without missing any details. This application not only includes a range of tools that can assist engineers, but also programmers in reverse engineering. It offers a multi-file environment and a customizable interface.

The purpose here is to see the DLL files running inside the program and to look at the data string values.
Remember, the more DLLs there are, the more processing there is on Windows.
Example: Avdapi.dll is used for registry edit operations, etc.
Exeinfo PE

Exeinfo PE is a program that allows you to verify .exe files and check all their properties. Additionally, you can rename the file, directly open or delete the .exe file. Another provided information is the full size and entry point. In short, you can access dozens of different options to edit any Windows executable file.
All the analyses we've done so far were "static" analyses.
Now, we are moving on to dynamic analysis. (That is, we are running the program and analyzing it.)
OllyDbg

OllyDbg is commonly used for reverse engineering of programs. It is often used to crack software made by other developers. Due to its ease of use and availability, it is primarily used as the tool of choice for reverse engineering; it can be used by any 32-bit executable debugger and can be edited in real-time in bitcode/assembly. It is useful for programmers to ensure their programs work as intended and for analyzing malicious software.
As you can see, when we run our "server" with "ollydbg," it shows us our DNS address, port, the copied folder path inside, and any error message if present.
Autoruns

Autoruns is a free system startup management tool developed by Microsoft. It is a successful and easy-to-use application where you can directly intervene in the startup folder, Run, RunOnce, and other Registry values where programs loaded at the beginning of your operating system are determined. Additionally, in Autoruns, you will find Internet Explorer toolbars, extensions, automatically starting system services, and much more.
FileAlyzer

If you want to learn more about the inner life of files, FileAlyzer is the tool you urgently need!
FileAlyzer displays basic file contents for interpreted complex file structures that help you understand the purpose of a file, a standard hex viewer, and various customized screens.
It also supports the creation of advanced file signatures with OpenSBI - you can find the right features to write your own optimized malware file signatures with FileAlyzer!
As you can see, when we run the "Superantispyware.exe" program we named "binder," it shows us information about what will be added to the startup, deleted, etc.
It is a very nice and useful "File Analysis" program. You can see almost everything through this program...
Process Hacker
Process Hacker is a free and open-source process viewer program. Process Hacker shows you which programs or processes are using CPU and memory on your computer. With the program, you can easily terminate any program or process that you consider unnecessary or harmful. We can say that Process Hacker is a highly advanced version of Windows Task Manager.
CurrPorts

CurrPorts is network monitoring software that displays a list of all currently open TCP/IP and UDP ports on your local computer. For each port listed, it provides information about the process that opened the port, such as the process name, full path of the process, and version information of the process (product name, file description, etc.).
Additionally, CurrPorts allows you to close unwanted TCP connections, terminate the process that opened the ports, and save TCP/UDP port information to an HTML file, XML file, or tab-delimited text file.
CurrPorts also automatically highlights suspicious TCP/UDP ports in pink for unidentified applications (applications without version information and icons).
Since I will be testing from my own computer, I used "127.0.0.1" localhost. You will see the port number and IP address of the victim.
Regshot

Regshot is a dynamic malware analysis tool that allows an analyst to capture before-and-after snapshots of the Windows Registry. Typically, this is used to capture the system's snapshot before and immediately after running malware.
The purpose is to identify changes made in the registry by the malware. This indicates what the malware might be capable of, specifying any additional files dropped or any other Indicators of Compromise (IOCs).
Process Monitor

Process Monitor is an advanced monitoring tool for Windows that displays real-time file system, Registry, and process/thread activity. It combines the features of two former Sysinternals utility programs, Filemon and Regmon, and adds a rich and non-destructive filtering, comprehensive event properties such as session IDs and user names, reliable process information, integrated symbol-supported full thread stacks, and a comprehensive development list. For each process, it provides a concurrent log of activity to a file and more. Its unique powerful features make Process Monitor a fundamental utility in your troubleshooting and malware detection toolset on your system.
These explanations are brief and to the point. If you delve into them, you can make much better analyses over time.
The more you work, the more you learn.
Click here to download all the tools.
Source: Malware Analiz Araçlarım Ve Kullanımları // Black Turtle





