- 7 Tem 2013
- 8,192
- 653
Network-Based Attacks
Network-based attacks have increased a lot, you can do it by purchasing virtual machines or paying money to websites.

What are the types of network-based attacks?
Password Cracking Attacks
DoS & DDoS Attacks
MAC Flooding Attacks
MiTM Attacks
DNS Spoofing Attacks
Harp Spoofing Attacks

Password Cracking Attacks
Password cracking is the process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords. In other words, it's an art of obtaining the correct password that gives access to a system protected by an authentication method.
1)Active Password Cracking Attack
Brute Force Attacks
Password Spraying Attacks
Brute Force Attack
a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found. Alternatively, the attacker can attempt to guess the key which is typically created from the password using a key derivation function. This is known as an exhaustive key search. So, brute force is a indefinite attack.

Password spraying is an attack that attempts to access a large number of accounts (usernames) with a few commonly used passwords. Traditional brute-force attacks attempt to gain unauthorized access to a single account by guessing the password. Password Spraying attacks for small institutions. The reason is that small institutions never give importance to website security.

2)Passive Password Cracking Attack
Hash Crack Attacks
Rainbow Table Attacks
Hash Crack Attacks
We must create a wordlist to do this attack. Hash Crack Attack is for a website's database.
Rainbow Table Attacks
a rainbow table attack is a type of hacking wherein the perpetrator tries to use a rainbow hash table to crack the passwords stored in a database system. A rainbow table is a hash function used in cryptography for storing important data such as passwords in a database.

Dos & DDoS Attacks
A DoS attack is a denial of service attack where a computer is used to flood a server with TCP and UDP packets. A DDoS attack is where multiple systems target a single system with a DoS attack. The targeted network is then bombarded with packets from multiple ********s. Every website has a capacity so the website starts to slow down if there is a dos & ddos attacks.

MAC Flooding Attacks
a media access control attack or MAC flooding is a technique employed to compromise the security of network switches. The attack works by forcing legitimate MAC table contents out of the switch and forcing a unicast flooding behavior potentially sending sensitive information to portions of the network where it is not normally intended to go. Every device has a MAC address. MAC address are the identities of electronic devices (tablet, computer, phone etc.)

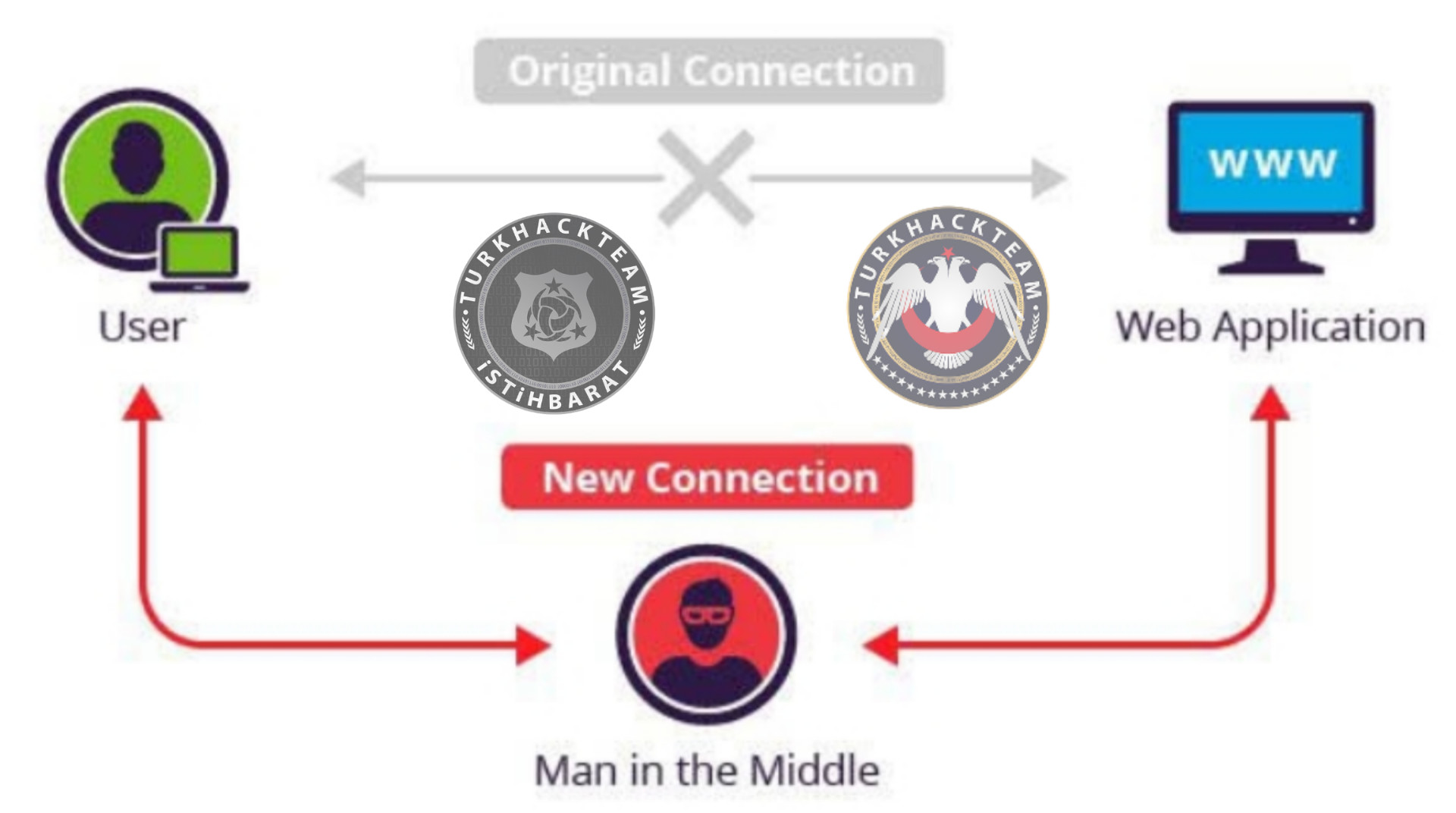
MITM Attacks
MITM is an attack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within the reception range of an unencrypted Wi-Fi access point could insert themselves as a man-in-the-middle.
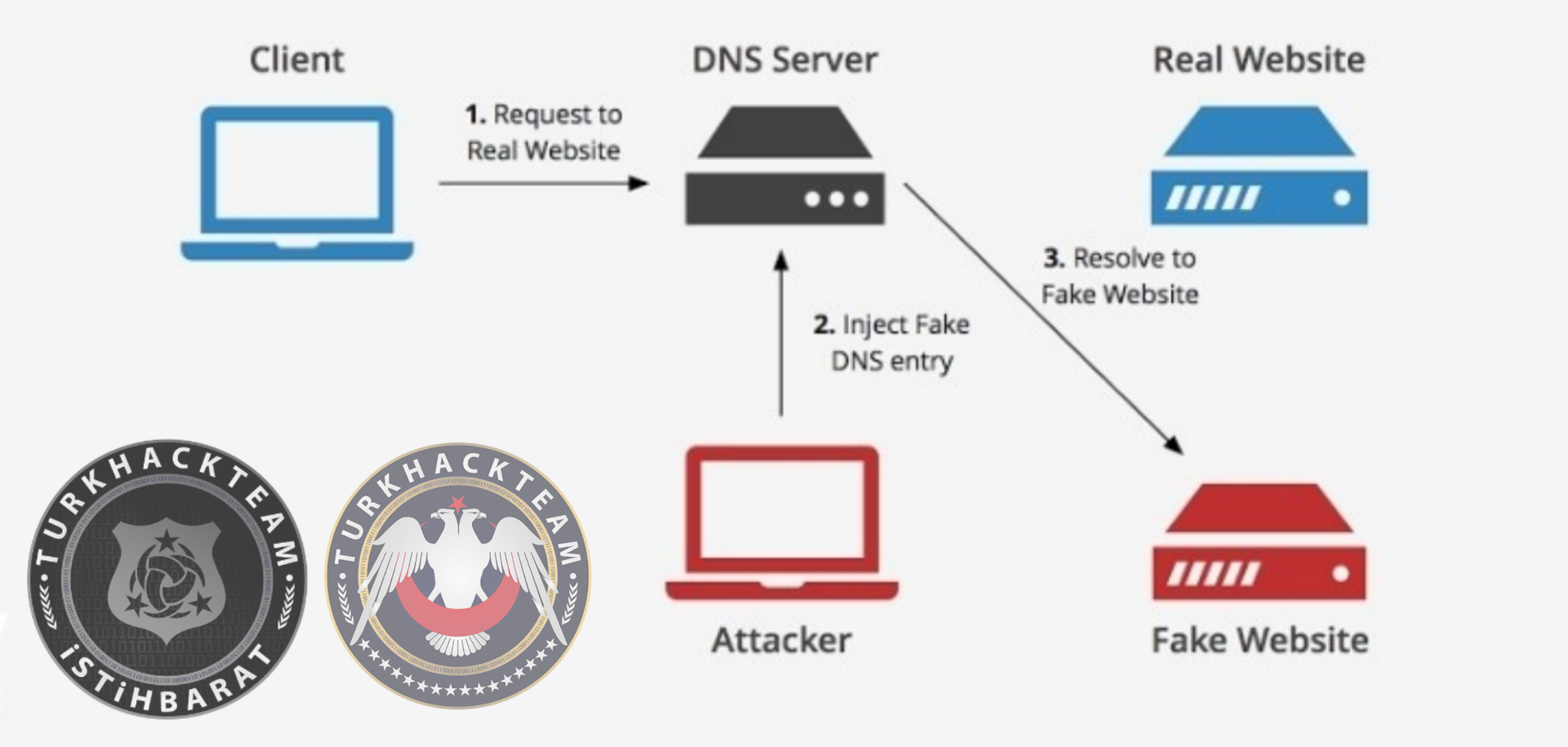
DNS Spoofing Attacks
a spoofing attack is a situation in which a person or program successfully identifies as another by falsifying data, to gain an illegitimate advantage. DNS Spoofing is an attack in which altered DNS records are used to redirect online traffic to a fraudulent website that resembles its intended destination. Once there, users are prompted to login into (what they believe to be) their account, giving the perpetrator the opportunity to steal their access credentials and other types of sensitive information. Furthermore, the malicious website is often used to install worms or viruses on a users computer, giving the perpetrator long-term access to it and the data it stores.

Arp Spoofing Attacks
Arp Spoofing Attacks are similar to Man in The Middle Attacks. ARP spoofing is a type of attack in which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of an attacker's MAC address with the IP address of a legitimate computer or server on the network. They can even watch you using this attack.

Source: https://www.turkhackteam.org/web-server-guvenligi/1911891-ag-tabanli-saldirilar.html
Translator dRose98
Network-based attacks have increased a lot, you can do it by purchasing virtual machines or paying money to websites.

What are the types of network-based attacks?
Password Cracking Attacks
DoS & DDoS Attacks
MAC Flooding Attacks
MiTM Attacks
DNS Spoofing Attacks
Harp Spoofing Attacks

Password Cracking Attacks
Password cracking is the process of attempting to gain Unauthorized access to restricted systems using common passwords or algorithms that guess passwords. In other words, it's an art of obtaining the correct password that gives access to a system protected by an authentication method.
1)Active Password Cracking Attack
Brute Force Attacks
Password Spraying Attacks
Brute Force Attack
a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found. Alternatively, the attacker can attempt to guess the key which is typically created from the password using a key derivation function. This is known as an exhaustive key search. So, brute force is a indefinite attack.

Password spraying is an attack that attempts to access a large number of accounts (usernames) with a few commonly used passwords. Traditional brute-force attacks attempt to gain unauthorized access to a single account by guessing the password. Password Spraying attacks for small institutions. The reason is that small institutions never give importance to website security.

2)Passive Password Cracking Attack
Hash Crack Attacks
Rainbow Table Attacks
Hash Crack Attacks
We must create a wordlist to do this attack. Hash Crack Attack is for a website's database.
Rainbow Table Attacks
a rainbow table attack is a type of hacking wherein the perpetrator tries to use a rainbow hash table to crack the passwords stored in a database system. A rainbow table is a hash function used in cryptography for storing important data such as passwords in a database.

Dos & DDoS Attacks
A DoS attack is a denial of service attack where a computer is used to flood a server with TCP and UDP packets. A DDoS attack is where multiple systems target a single system with a DoS attack. The targeted network is then bombarded with packets from multiple ********s. Every website has a capacity so the website starts to slow down if there is a dos & ddos attacks.


MAC Flooding Attacks
a media access control attack or MAC flooding is a technique employed to compromise the security of network switches. The attack works by forcing legitimate MAC table contents out of the switch and forcing a unicast flooding behavior potentially sending sensitive information to portions of the network where it is not normally intended to go. Every device has a MAC address. MAC address are the identities of electronic devices (tablet, computer, phone etc.)

MITM Attacks
MITM is an attack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within the reception range of an unencrypted Wi-Fi access point could insert themselves as a man-in-the-middle.

DNS Spoofing Attacks
a spoofing attack is a situation in which a person or program successfully identifies as another by falsifying data, to gain an illegitimate advantage. DNS Spoofing is an attack in which altered DNS records are used to redirect online traffic to a fraudulent website that resembles its intended destination. Once there, users are prompted to login into (what they believe to be) their account, giving the perpetrator the opportunity to steal their access credentials and other types of sensitive information. Furthermore, the malicious website is often used to install worms or viruses on a users computer, giving the perpetrator long-term access to it and the data it stores.


Arp Spoofing Attacks
Arp Spoofing Attacks are similar to Man in The Middle Attacks. ARP spoofing is a type of attack in which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of an attacker's MAC address with the IP address of a legitimate computer or server on the network. They can even watch you using this attack.

Source: https://www.turkhackteam.org/web-server-guvenligi/1911891-ag-tabanli-saldirilar.html
Translator dRose98





