Privilege Escalation | TurkHackTeam
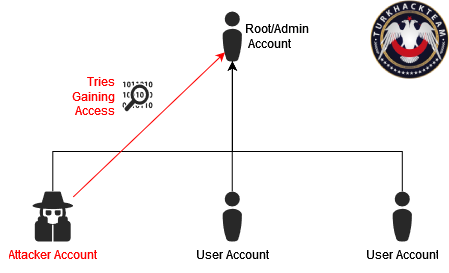
Privilege Escalation is an activity conducted by an attacker to increase the access level on a system. The goal is to elevate limited access to the highest level. The techniques used for privilege escalation vary depending on the target system. Here are the key points for Linux and Windows, which are commonly used operating systems:
For Linux:
- Kernel Exploit: The kernel is the component that provides the highest privileges to the system. Kernel exploits take advantage of kernel vulnerabilities and weaknesses to elevate access from a lower level to a higher level.
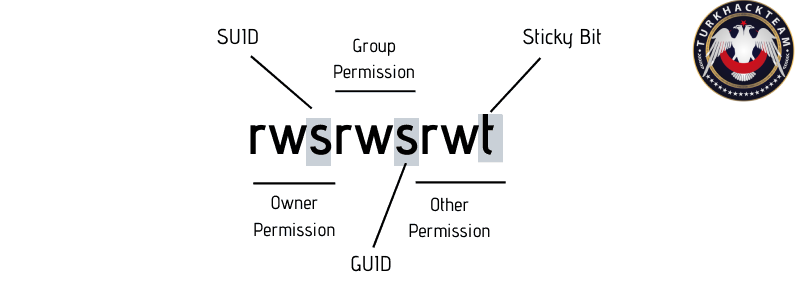
- SUID: In Linux, SUID allows files to be executed with the permissions of the file owner, bypassing the user's access level. If a file created by the system administrator (root) is given the SUID permission, any user can execute that file with administrative privileges.
For Windows:

- UAC (User Account Control) Bypass: Windows has the UAC mechanism, which limits user accounts to default access levels. An attacker can bypass or disable UAC to elevate their access level from the default to administrator.
- DLL Injection: By injecting a dynamic-link library (DLL) into the memory of an application, an attacker can execute code within the application. This method allows elevation of limited access to administrator level.
- Service Exploitation: This method can be performed on both Linux and Windows. Services can be assigned high privileges based on their operational principles and usage scenarios. An attacker can exploit security vulnerabilities in services to elevate their access to administrator level.
Son düzenleme:











