Hello everyone, friends, I'm Coderx37. Today, we will discuss EEG signals and the security of these signals in the field of biometric data. It is strongly recommended to read this topic before delving into it.
READING TIME: 13 minutes
Introduction:
The purpose of this text is to evaluate the fate of authentication systems requiring high security in today's world using EEG signals.

READING TIME: 13 minutes
Introduction:
The purpose of this text is to evaluate the fate of authentication systems requiring high security in today's world using EEG signals.

- In today's world, biometric methods such as fingerprint, iris recognition, voice analysis, and facial recognition are commonly used for individuals to securely authenticate their identities. However, these methods have some vulnerabilities, and there is a risk of creating counterfeit biometric data. Therefore, to enhance the security of authentication systems, it is necessary to explore different biometric features.
In line with this need;
Electroencephalogram (EEG) signals stand out as a prominent biometric feature.
EEG signals reflect brain activity, and it is widely accepted that this activity creates a personalized trace. Moreover, EEG signals have a more secure structure compared to other biometric data and require an extremely challenging process to be copied.
Where does this security come from?- Personal and Complex Traces: Each individual's EEG signals are unique, and these signals reflect the person's brain activity. Brain activity is intricately related to the individual's thought processes, emotional state, and other biometric features. Therefore, EEG signals leave a personalized and complex trace.
- Difficulty in Brain Access: EEG signals directly measure an individual's brain activity. This means that for someone to steal the signals, they would need physical access to the person's brain activity. Other biometric data, such as fingerprints or facial recognition, can be more easily copied.
- Ever-Changing Nature: EEG signals respond to the person's continuously changing mental and emotional states. This ever-changing nature complicates copying attempts. Other biometric features have a fixed structure and are therefore more easily copied.
Kişinin EEG verilerini kafasına zorla makine takıp almaya çalışmanız durumunda kişi anlık korku duygusu ile gereken işlemi tamamlayamayacaktır.
- Hardware and Software Requirements: Specialized hardware and software are necessary for the accurate measurement of EEG signals.
This makes unauthorized signal theft more complex.
Biometric identity authentication systems are used in various applications, especially for technological devices such as phones and computers that we never separate from. However, issues such as data privacy, data security, and error rates need to be handled with great care.
Knowledge-based identity authentication is a system where users authenticate their identities using unique number combinations or secret information like username-password pairs. This confidential information is stored in a dedicated database for security purposes. When users enter this confidential information, their identities are verified when they match the information in the database. However, the disadvantage of these systems is the risk of users' combinations or username-password information easily falling into the wrong hands.
Possession-based identity authentication allows users to enter the system using objects that are often unique and associated with themselves, such as door keys, cryptographic keys, or magnetic cards. However, this identity authentication method involves potential risks such as the loss of these objects.
When these two risky situations are considered, another approach emerges.
Biometric Identity Verification
Biometric identity verification utilizes unique physiological or behavioral characteristics that distinguish individuals from others. Features such as fingerprints, EEG, facial recognition, iris scanning, palm prints, or signatures are used for identity verification and precisely define a person's identity.
The potential for EEG signals in biometric recognition is based on the following factors:
Uniqueness: Each individual's EEG signals are unique. Anatomical and physiological differences in the brain lead to the formation of unique EEG patterns for each person. This uniqueness can be utilized to distinguish one person from others.
Security: EEG signals are considered a biometric feature that is difficult to physically copy or counterfeit. Compared to other biometric features, it may be a more secure method of identification because EEG signals reflect an activity directly occurring in the brain and are challenging to manipulate externally.
Dynamism: EEG signals reflect changes over time. Brain activity varies depending on factors such as an individual's mental state, emotional state, and level of attention. This dynamism can enable a more robust and reliable biometric recognition system.
Scalability: EEG signals can be recorded in different situations and for different tasks. This allows biometric recognition systems to be used in various scenarios. For example, an EEG-based recognition system can be used in attention-focused tasks or situations where brain activity is evaluated in response to emotional reactions. Processing, feature extraction, and classification methods are required to perform biometric recognition with EEG signals. Programs like MATLAB provide commonly used tools for the analysis of EEG signals.
In summary, EEG signals have the potential for biometric recognition due to factors such as uniqueness, security, dynamism, and scalability. However, developing an EEG-based recognition system can be complex, and advanced signal processing and data analysis techniques may be necessary to improve accuracy.
So, how is this verification process carried out?
Pattern Matching: In this method, pre-recorded EEG patterns of an individual are stored in a database. During identity verification or recognition, current EEG signals are recorded and compared with the stored patterns. An matching score is calculated using similarity criteria, and when a specific threshold is exceeded, an individual is recognized or authenticated.
Since it's so secure and logical, why isn't it being used right now?
The cost of devices that can measure EEG signals is at a level that someone who is interested in this field as a hobby cannot afford. Because of the high cost, access to this technology is quite challenging. Sensors that collect biometric data such as eye, fingerprint, and facial sensors, which are competitors, are procured at a much lower cost.

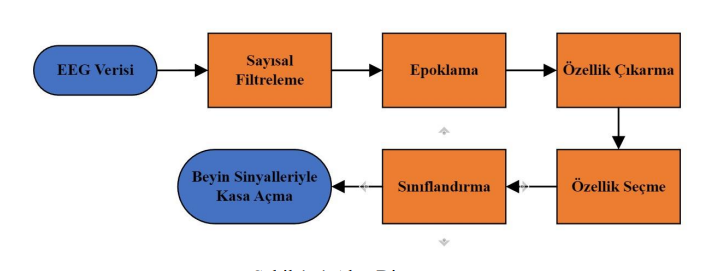
Data Filtering and Epoching
The brain is a complex structure that continuously operates and responds to every situation. To obtain the desired data within such data traffic, we need to apply specific filtering processes. Let's now look at filtering techniques:
Epoching involves dividing the EEG signal into time intervals to analyze it in smaller segments. This method is used to examine specific events or conditions on the signal. For example, in a task-based EEG experiment, epochs are created to analyze brain activity related to a specific stimulus or task period.
Low-Pass Filter: A low-pass filter reduces or filters components above a certain frequency. This filter focuses on low-frequency components by eliminating high-frequency noise in EEG signals.
High-Pass Filter: A high-pass filter reduces or filters components below a certain frequency. This filter focuses on high-frequency components by eliminating low-frequency noise in EEG signals.
Band-Pass Filter: A band-pass filter preserves components within a specific frequency range while reducing or filtering components at other frequencies. This filter allows concentration on a specific frequency band. For example, it is used to emphasize wave activity in a specific EEG frequency range.
Band-Stop Filter: A band-stop filter eliminates or reduces components within a specific frequency range while preserving components at other frequencies. This filter is used to remove noise in unwanted frequency bands.
FINAL AND EXPERIMENT
Before making EEG systems an integral part of today with uncertain ideas about their accuracy, we should be aware of the following requirements and situations:
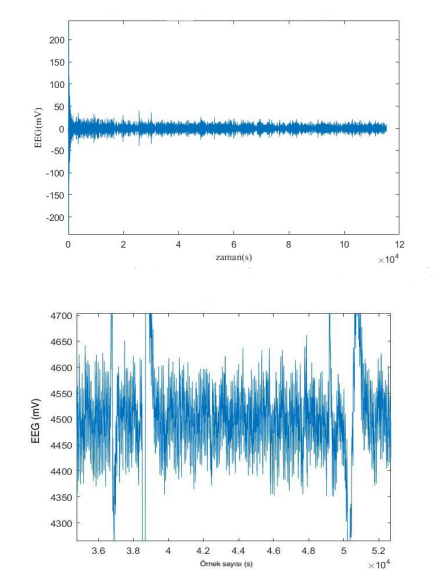
EEG signals are currently obtained with large and expensive devices attached to the head, and they are not portable.
Although a data verification process takes about 15-20 seconds, the initial EEG measurements take about 15 minutes.
There is no known harm to health, but it is known that focusing on a specific situation and then thinking about that situation again can cause mental fatigue.
Now let's consider the results technically:
Let's consider a scenario: We have 8 participants, 3 males and 5 females, and create datasets with 14-channel EEG signals obtained from them. Let's handle all the necessary epoching and filtering processes.
In this experiment, the participants are asked to open a safe through thought processes.
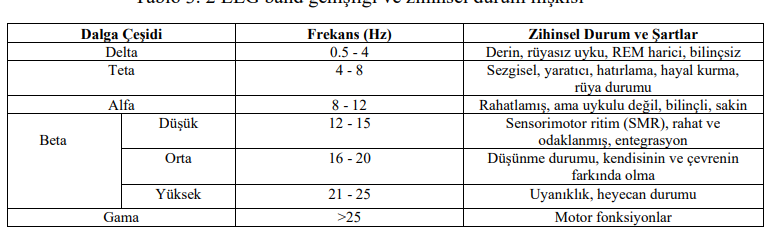
Based on the data obtained from this experiment, it is determined that the shortest duration for opening the safe is 10 seconds, and the frequency range that corresponds to the focus and thinking state at the time of data collection is found to be Beta Low and Beta Mid, based on the literature review conducted. Performance evaluation tables created separately for each lower frequency band show that the Decision Trees algorithm, using 10% (3 features) of the features in the Beta-Mid frequency band, performs the best with a 100% accuracy rate.
Knowledge-based identity authentication is a system where users authenticate their identities using unique number combinations or secret information like username-password pairs. This confidential information is stored in a dedicated database for security purposes. When users enter this confidential information, their identities are verified when they match the information in the database. However, the disadvantage of these systems is the risk of users' combinations or username-password information easily falling into the wrong hands.
Possession-based identity authentication allows users to enter the system using objects that are often unique and associated with themselves, such as door keys, cryptographic keys, or magnetic cards. However, this identity authentication method involves potential risks such as the loss of these objects.
When these two risky situations are considered, another approach emerges.
Biometric Identity Verification
Biometric identity verification utilizes unique physiological or behavioral characteristics that distinguish individuals from others. Features such as fingerprints, EEG, facial recognition, iris scanning, palm prints, or signatures are used for identity verification and precisely define a person's identity.
The potential for EEG signals in biometric recognition is based on the following factors:
Uniqueness: Each individual's EEG signals are unique. Anatomical and physiological differences in the brain lead to the formation of unique EEG patterns for each person. This uniqueness can be utilized to distinguish one person from others.
Security: EEG signals are considered a biometric feature that is difficult to physically copy or counterfeit. Compared to other biometric features, it may be a more secure method of identification because EEG signals reflect an activity directly occurring in the brain and are challenging to manipulate externally.
Dynamism: EEG signals reflect changes over time. Brain activity varies depending on factors such as an individual's mental state, emotional state, and level of attention. This dynamism can enable a more robust and reliable biometric recognition system.
Scalability: EEG signals can be recorded in different situations and for different tasks. This allows biometric recognition systems to be used in various scenarios. For example, an EEG-based recognition system can be used in attention-focused tasks or situations where brain activity is evaluated in response to emotional reactions. Processing, feature extraction, and classification methods are required to perform biometric recognition with EEG signals. Programs like MATLAB provide commonly used tools for the analysis of EEG signals.
In summary, EEG signals have the potential for biometric recognition due to factors such as uniqueness, security, dynamism, and scalability. However, developing an EEG-based recognition system can be complex, and advanced signal processing and data analysis techniques may be necessary to improve accuracy.
So, how is this verification process carried out?

Pattern Matching: In this method, pre-recorded EEG patterns of an individual are stored in a database. During identity verification or recognition, current EEG signals are recorded and compared with the stored patterns. An matching score is calculated using similarity criteria, and when a specific threshold is exceeded, an individual is recognized or authenticated.
Since it's so secure and logical, why isn't it being used right now?
The cost of devices that can measure EEG signals is at a level that someone who is interested in this field as a hobby cannot afford. Because of the high cost, access to this technology is quite challenging. Sensors that collect biometric data such as eye, fingerprint, and facial sensors, which are competitors, are procured at a much lower cost.

Data Filtering and Epoching
The brain is a complex structure that continuously operates and responds to every situation. To obtain the desired data within such data traffic, we need to apply specific filtering processes. Let's now look at filtering techniques:
Epoching involves dividing the EEG signal into time intervals to analyze it in smaller segments. This method is used to examine specific events or conditions on the signal. For example, in a task-based EEG experiment, epochs are created to analyze brain activity related to a specific stimulus or task period.
Low-Pass Filter: A low-pass filter reduces or filters components above a certain frequency. This filter focuses on low-frequency components by eliminating high-frequency noise in EEG signals.
High-Pass Filter: A high-pass filter reduces or filters components below a certain frequency. This filter focuses on high-frequency components by eliminating low-frequency noise in EEG signals.
Band-Pass Filter: A band-pass filter preserves components within a specific frequency range while reducing or filtering components at other frequencies. This filter allows concentration on a specific frequency band. For example, it is used to emphasize wave activity in a specific EEG frequency range.
Band-Stop Filter: A band-stop filter eliminates or reduces components within a specific frequency range while preserving components at other frequencies. This filter is used to remove noise in unwanted frequency bands.

FINAL AND EXPERIMENT
Before making EEG systems an integral part of today with uncertain ideas about their accuracy, we should be aware of the following requirements and situations:
EEG signals are currently obtained with large and expensive devices attached to the head, and they are not portable.
Although a data verification process takes about 15-20 seconds, the initial EEG measurements take about 15 minutes.
There is no known harm to health, but it is known that focusing on a specific situation and then thinking about that situation again can cause mental fatigue.
Now let's consider the results technically:
Let's consider a scenario: We have 8 participants, 3 males and 5 females, and create datasets with 14-channel EEG signals obtained from them. Let's handle all the necessary epoching and filtering processes.
In this experiment, the participants are asked to open a safe through thought processes.
Based on the data obtained from this experiment, it is determined that the shortest duration for opening the safe is 10 seconds, and the frequency range that corresponds to the focus and thinking state at the time of data collection is found to be Beta Low and Beta Mid, based on the literature review conducted. Performance evaluation tables created separately for each lower frequency band show that the Decision Trees algorithm, using 10% (3 features) of the features in the Beta-Mid frequency band, performs the best with a 100% accuracy rate.
Prediction models have been created for the targeted lower frequency bands, and detections have been carried out in the minimum time. Models showed different performances for each created frequency band range. The safe opening process was conducted with 10-second epochs, resulting in a 100% accuracy rate.
In conclusion, with prediction models created in a 10-second period, the safe opening process was performed with high accuracy.
So, it seems possible for us to use EEG signals as biometric data in the near future.
THANK YOU FOR READING.
Source: @Coderx37 https://www.turkhackteam.org/konula...mleri-uzerine-arastirma.2049348/#post-9870485
In conclusion, with prediction models created in a 10-second period, the safe opening process was performed with high accuracy.
So, it seems possible for us to use EEG signals as biometric data in the near future.
THANK YOU FOR READING.
Source: @Coderx37 https://www.turkhackteam.org/konula...mleri-uzerine-arastirma.2049348/#post-9870485






