A suspected Pakistan-aligned advanced persistent threat (APT) group known as Transparent Tribe has been linked to an ongoing cyber espionage campaign targeting Indian and Pakistani Android users with a backdoor called CapraRAT.
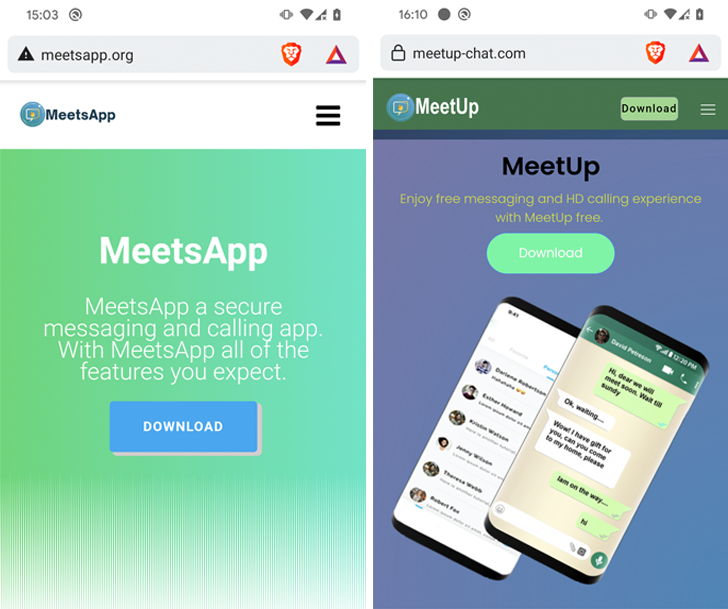
"Transparent Tribe distributed the Android CapraRAT backdoor via trojanized secure messaging and calling apps branded as MeetsApp and MeetUp," ESET said
As many as 150 victims, likely with military or political leanings, are estimated to have been targeted, with the malware (com.meetup.app) available to download from fake websites that masquerade as the official distribution centers of these apps.
It's being suspected that the targets are lured through a honeytrap romance scam wherein the threat actor approaches the victims via another platform and persuades them to install the malware-laced apps under the pretext of "secure" messaging and calling.
However, the apps, besides offering the promised functionality, come implanted with CapraRAT, a modified version of the open source AndroRAT that was first documented by Trend Micro in February 2022 and which exhibits overlaps with a Windows malware known as CrimsonRAT.
The backdoor is packed with an extensive set of features that allows it to take screenshots and photos, record phone calls and surrounding audio, and exfiltrate other sensitive information. It can also make calls, send SMS messages, and receive commands to download files.
That having said, users are also required to create an account by linking their phone numbers and completing an SMS verification step in order to access the app's functionalities.
The Slovak cybersecurity company stated the campaign is narrowly targeted and that it found no evidence that indicates the apps were available on the Google Play Store.
Transparent Tribe, also referred to as APT36, Operation C-Major, and Mythic Leopard, was recently attributed to another set of attacks targeting Indian government organizations with malicious versions of a two-factor authentication solution called Kavach.
The findings also arrive weeks after cybersecurity firm ThreatMon detailed a spear-phishing campaign by SideCopy actors targeting Indian government entities with an aim to deploy an updated version of a backdoor known as ReverseRAT.





