

Greetings to all of you, friends. In today's topic we are going to solve the CTF machine called WebOSINT, which is included in TryHackMe. Before we start solving our CTF machine, let's look at what the word Osint means.
OSINT, which is defined as the abbreviation of Open Source Intelligence, means Open Source Intelligence in Turkish. OSINT is defined as intelligence activities that do not require any confidentiality, are publicly available, obtained by filtering (analyzing) information collected for a specific purpose that decides whether it has an intelligence nature or not.

We will do exactly that with this CTF machine. Our machine consists of a total of 9 tasks. Let's get started.

Task 1: If You Don't Have a Website
Our machine has given us a site called RepublicOfKoffee.com and wants us to collect information about this site. As the name of Task 1 suggests, when we want to go to the site, we get an error that there is no such website. However, this does not mean that we cannot find information about the target site. We can find the opposite, let's start our intensive research work now.
First, let's perform a search through Google.
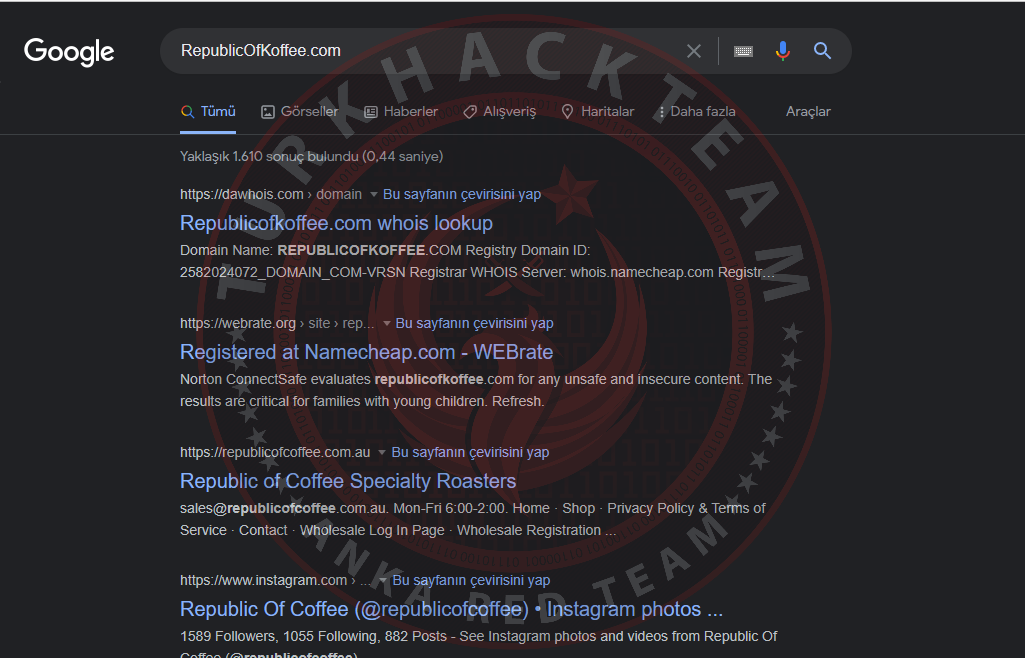
There is no website, but there is some information about the site in the search result.
We continue by saying that Task 1 is completed.

Task 2: Whois Registration
The 'Whois' lookup is the most basic form of domain reconstruction available. There are multiple websites that will do this for you as well.
Personally, I recommend going directly to the lookup.icann.org. This tells you in detail that the current hosting company is being used and naming the servers. Looking at the raw data option will show more details. We have already recommended this site.

Or we can get some information about the target site by searching with the whois command through the terminal.
1. What is the name of the company where the domain name is registered?
If we search through the terminal;
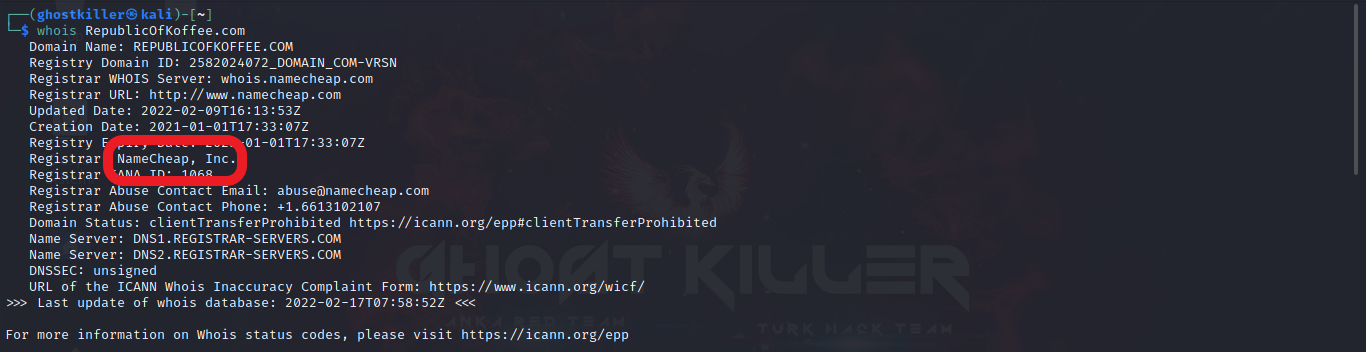
If we search through the website;

Our response: NAMECHEAP INC

2. What phone number is listed for the registrar? (do not include country code or special characters/spaces)
We can get our answer by auditing the Raw Registry RDAP Response and the Raw Registrar RDAP Response.
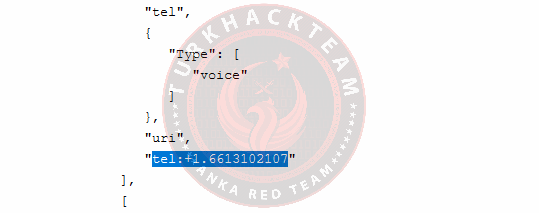
Or we can reach it from our whois search result through the terminal.
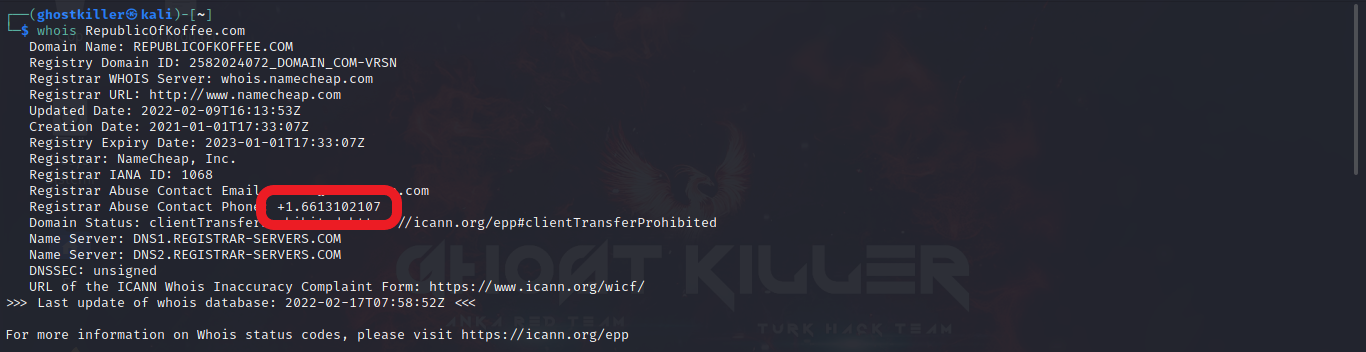
Our response: 6613102107

3. What is the first name server listed for the site?
Via our search site

Or we can reach our answer from the search result we make through the terminal.
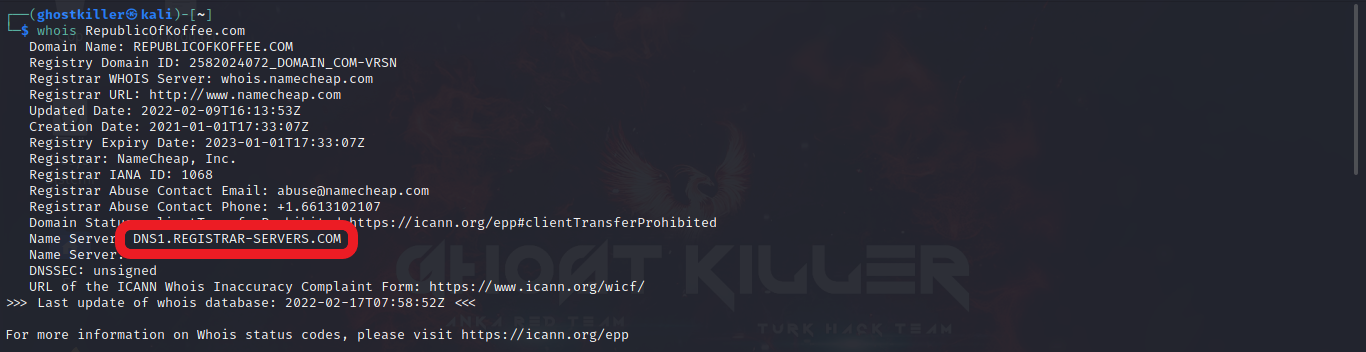
Our response: DNS1.REGISTRAR-SERVERS.COM

4. What is listed for the registrant's name?
Again, using these search results, you can see that the name is actually "redacted for privacy."
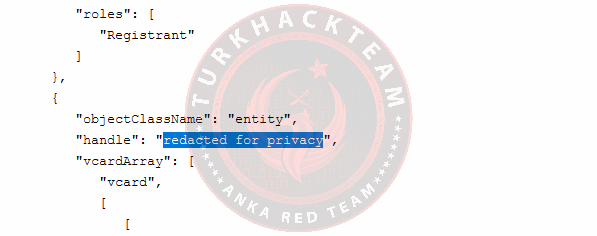
Our response: redacted for privacy

5. Which country is the registrant?
When we continue to examine the results;
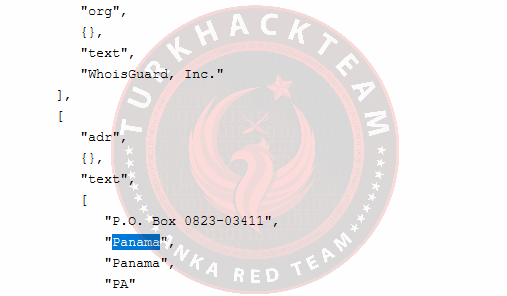
We see that the country that registered is Panama.
Our response: Panama

Personally, I recommend going directly to the lookup.icann.org. This tells you in detail that the current hosting company is being used and naming the servers. Looking at the raw data option will show more details. We have already recommended this site.

Or we can get some information about the target site by searching with the whois command through the terminal.
1. What is the name of the company where the domain name is registered?
If we search through the terminal;

If we search through the website;


Our response: NAMECHEAP INC

2. What phone number is listed for the registrar? (do not include country code or special characters/spaces)
We can get our answer by auditing the Raw Registry RDAP Response and the Raw Registrar RDAP Response.

Or we can reach it from our whois search result through the terminal.

Our response: 6613102107

3. What is the first name server listed for the site?
Via our search site

Or we can reach our answer from the search result we make through the terminal.

Our response: DNS1.REGISTRAR-SERVERS.COM

4. What is listed for the registrant's name?
Again, using these search results, you can see that the name is actually "redacted for privacy."

Our response: redacted for privacy

5. Which country is the registrant?
When we continue to examine the results;

We see that the country that registered is Panama.
Our response: Panama

Task 3: Ghosts of Past Websites
To learn more here, we'll use Internet Archive: Digital Library of Free & Borrowable Books, Movies, Music & Wayback Machine.
We have to use the Wayback Machine to look at the history of the site. If we use it to search for 'RepublicofKoffee.com', we can see that there have been 25 captures since 2015.


1. What is the blogger's first name?
Let's start with the oldest date from December 31, 2015, that is, the beginning:
Let's examine the site that appears.

Let's scroll down and you'll see a bunch of blog posts:
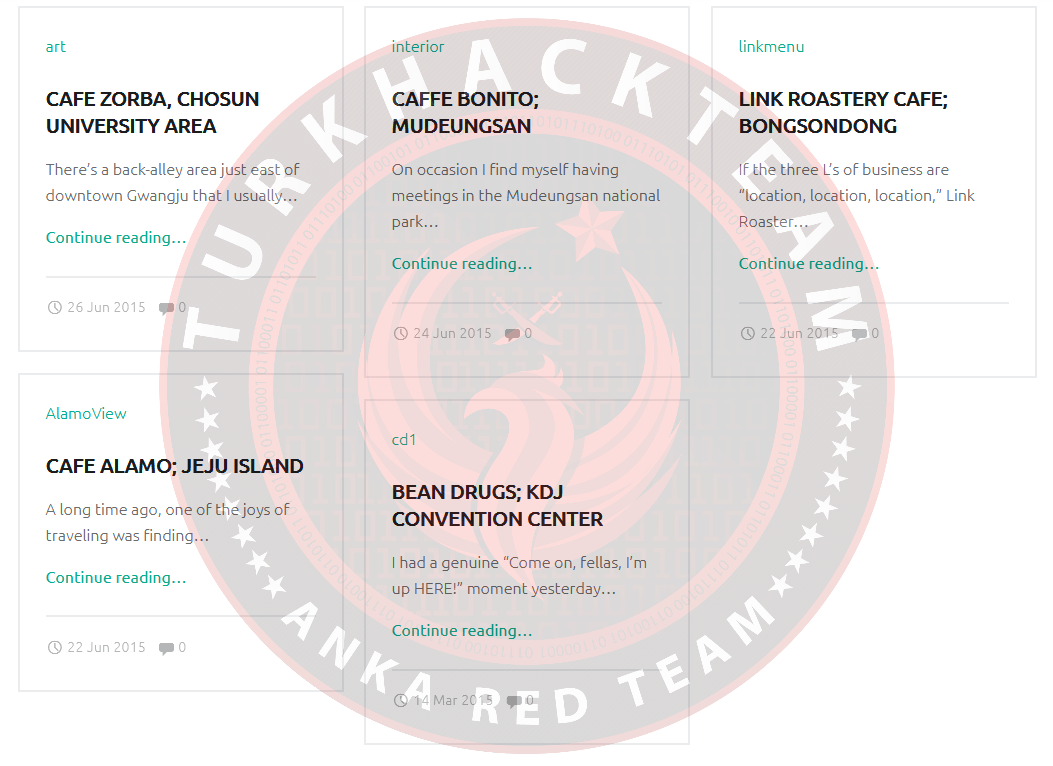
Let's go into any of the blog posts that come up.

We can see that the author of the blog is "Steve".
Our Response: Steve

2. From which city and country was the author writing?
When we examine the blog post we have chosen above, we come across a city name called Gwangju.

We can find this in more detail by doing a search through Google.

You can see Steve talking about the city of Gwangju in South Korea:
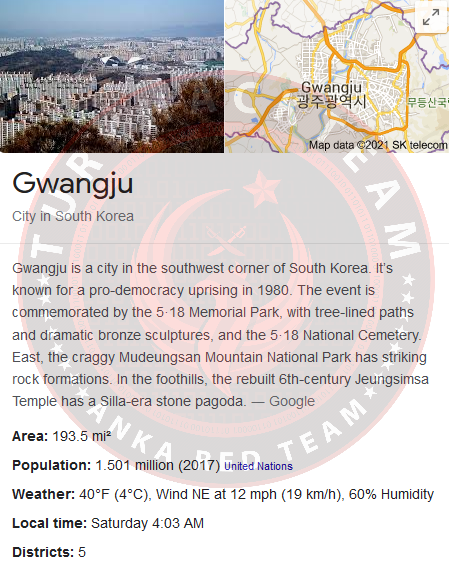
Our Response: Gwangju, South Korea

3. [Research] What is the name (in English) of the temple inside the National Park that the author often mentions?
This question prompted us to review and read Steve's blog posts, and I kept reviewing it until I found this section:
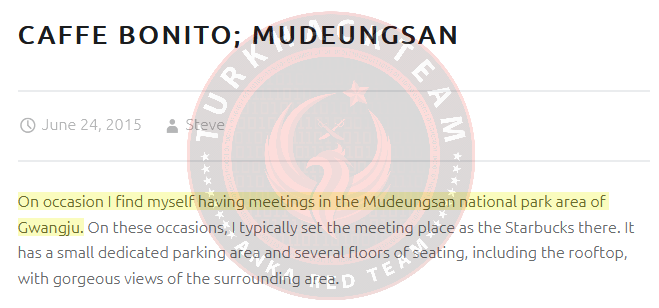
The author is talking about the 'temple of Mudeungsan National Park' here. Let's use Google to search. As a result of the search, we also found some information.
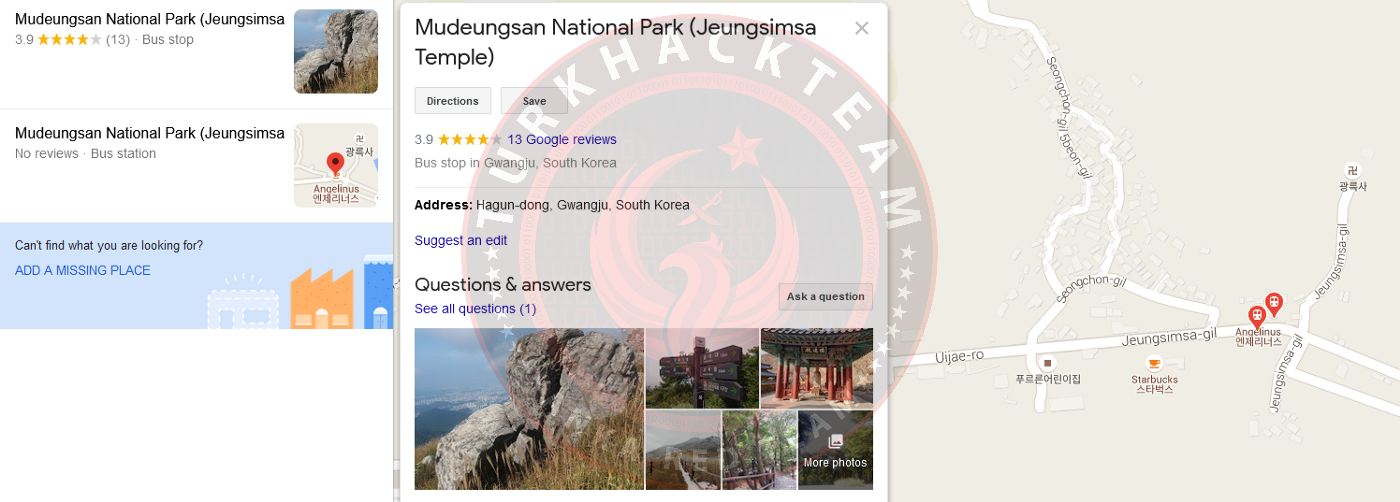
We can see that the English name of the temple is Jeungsimsa Temple. At the same time, when we look at the map, we can even see that there is a Starbucks café quite close by.
If you are interested, the picture of the temple is as follows;

Our Response: Jeungsimsa Temple

We have to use the Wayback Machine to look at the history of the site. If we use it to search for 'RepublicofKoffee.com', we can see that there have been 25 captures since 2015.


1. What is the blogger's first name?
Let's start with the oldest date from December 31, 2015, that is, the beginning:
Let's examine the site that appears.


Let's scroll down and you'll see a bunch of blog posts:

Let's go into any of the blog posts that come up.

We can see that the author of the blog is "Steve".
Our Response: Steve

2. From which city and country was the author writing?
When we examine the blog post we have chosen above, we come across a city name called Gwangju.

We can find this in more detail by doing a search through Google.

You can see Steve talking about the city of Gwangju in South Korea:

Our Response: Gwangju, South Korea

3. [Research] What is the name (in English) of the temple inside the National Park that the author often mentions?
This question prompted us to review and read Steve's blog posts, and I kept reviewing it until I found this section:

The author is talking about the 'temple of Mudeungsan National Park' here. Let's use Google to search. As a result of the search, we also found some information.

We can see that the English name of the temple is Jeungsimsa Temple. At the same time, when we look at the map, we can even see that there is a Starbucks café quite close by.
If you are interested, the picture of the temple is as follows;

Our Response: Jeungsimsa Temple

Task 4: Introduction to DNS
In this task, ViewDNS.info - Your one source for DNS related tools! We will use a view dns info site called quite useful and useful, which gives us information about the dns information of the target site.
1. What was the IP address of RepublicOfKoffee.com as of October 2016?
Let's use the IP History tool for this.
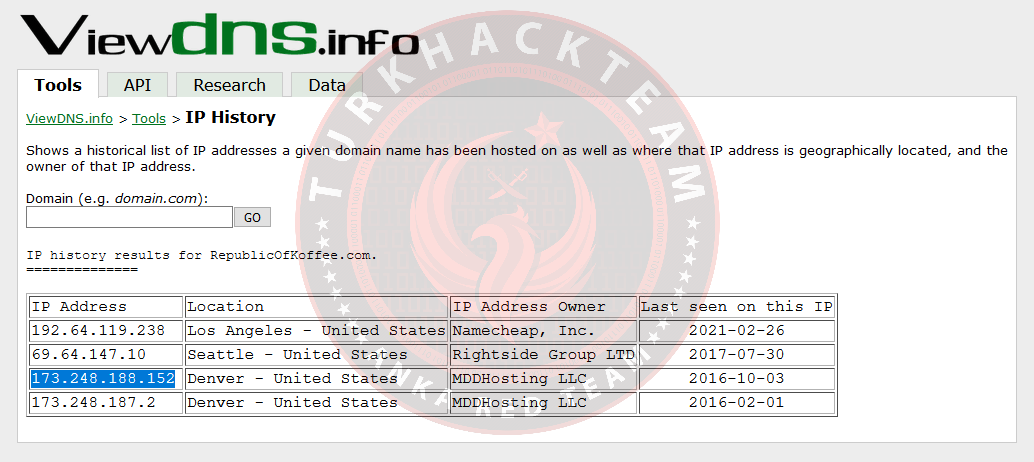
Our response: 173.248.188.152

2. Based on other domains hosted on the same IP address, what kind of hosting service can we assume our target is using safely?
For this, I used the Reverse IP lookup tool. It attracted 97 different domains for this private IP:
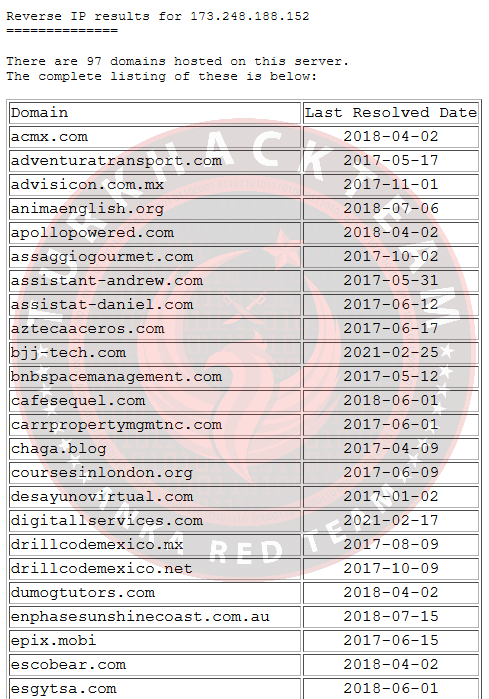
Check out the tip for the question, "What kind of hosting plan is used by websites with a tight budget that usually doesn't have a lot of visitors?" he says.
The answer to this is SHARED web hosting. Click HERE to learn about some other different species.

Our response: Shared

3. How many times has the IP address changed in the domain history?
You can go back to Question #1 for this:

It seems to have changed 4 times.
Our Response: 4

1. What was the IP address of RepublicOfKoffee.com as of October 2016?
Let's use the IP History tool for this.

Our response: 173.248.188.152

2. Based on other domains hosted on the same IP address, what kind of hosting service can we assume our target is using safely?
For this, I used the Reverse IP lookup tool. It attracted 97 different domains for this private IP:

Check out the tip for the question, "What kind of hosting plan is used by websites with a tight budget that usually doesn't have a lot of visitors?" he says.
The answer to this is SHARED web hosting. Click HERE to learn about some other different species.


Our response: Shared

3. How many times has the IP address changed in the domain history?
You can go back to Question #1 for this:

It seems to have changed 4 times.
Our Response: 4

Task 5: Removing the Training Wheels
In Mission 5, we're starting again with a completely new domain name.
To us in office;
"Congratulations on coming this far. For this task you will need all the skills you have learned so far. All I have for you is a domain name:
heat[dot]net"
Say. So let's get started.


1. What is the second name server listed for the domain?
Let's open our terminal and perform a search using the whois command in line with the information given to us.
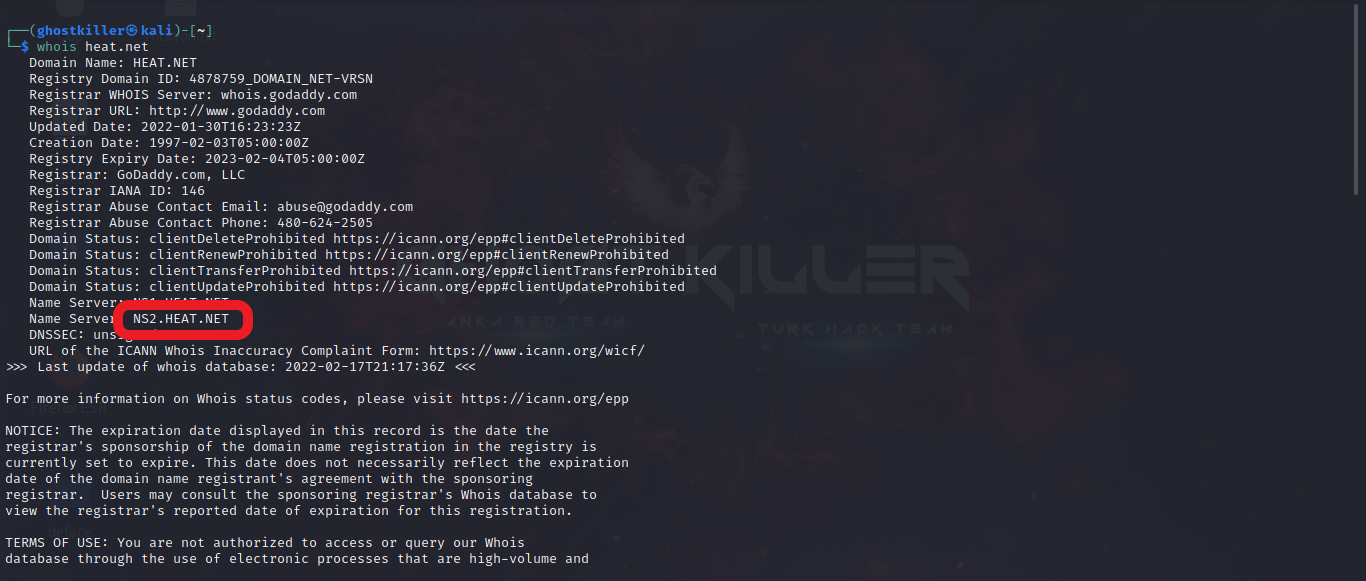
Our Response: NS2.HEAT.NET

2. At what IP address is the domain listed as of December 2011?
For this, let's use the IP History tool in views dns info.
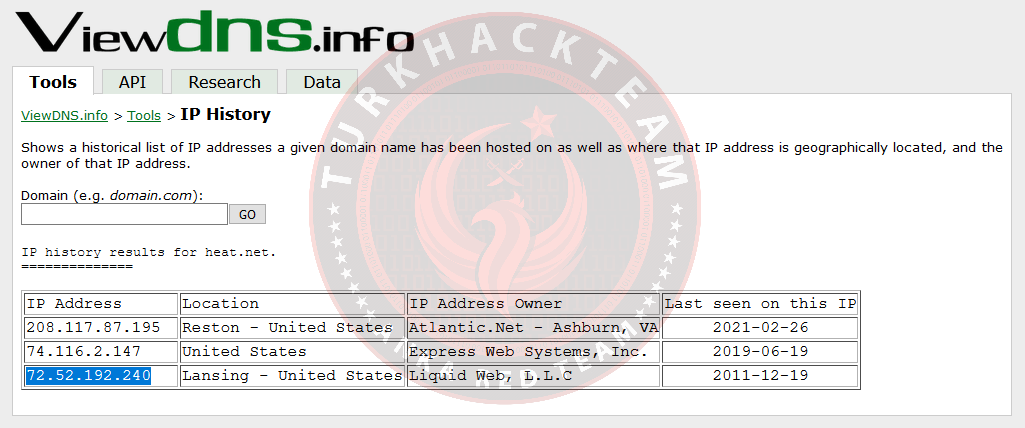
Our Response: 72.52.192.240

3. Depending on the domains that share the same IP, what kind of hosting service is the domain owner using?
Using the current IP, let's use the Reverse IP Lookup tool. We found that this was most likely shared.
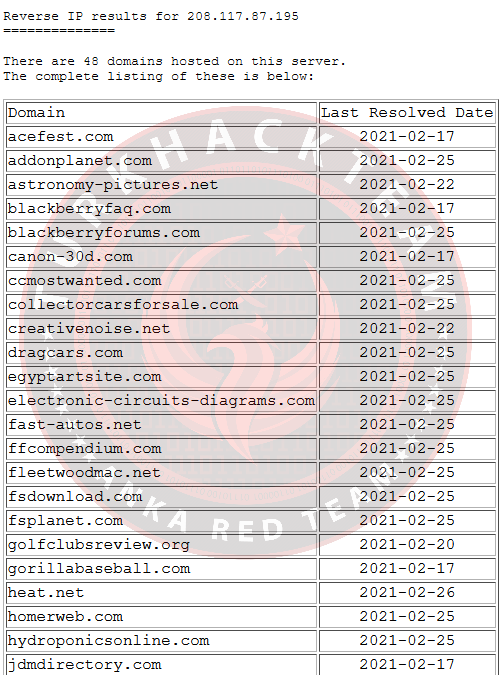
Our Response: Shared

4. When was the site first taken over by the internet archive? (MM/MM/YY format)
Using the Wayback Machine, we can see that this domain has been captured more than 600 times since June 1, 1997.
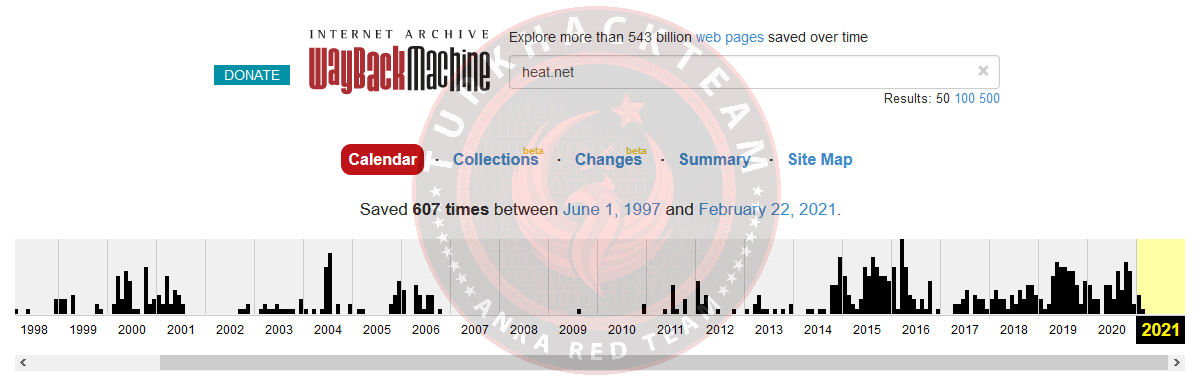
Here is the visibility of that page;
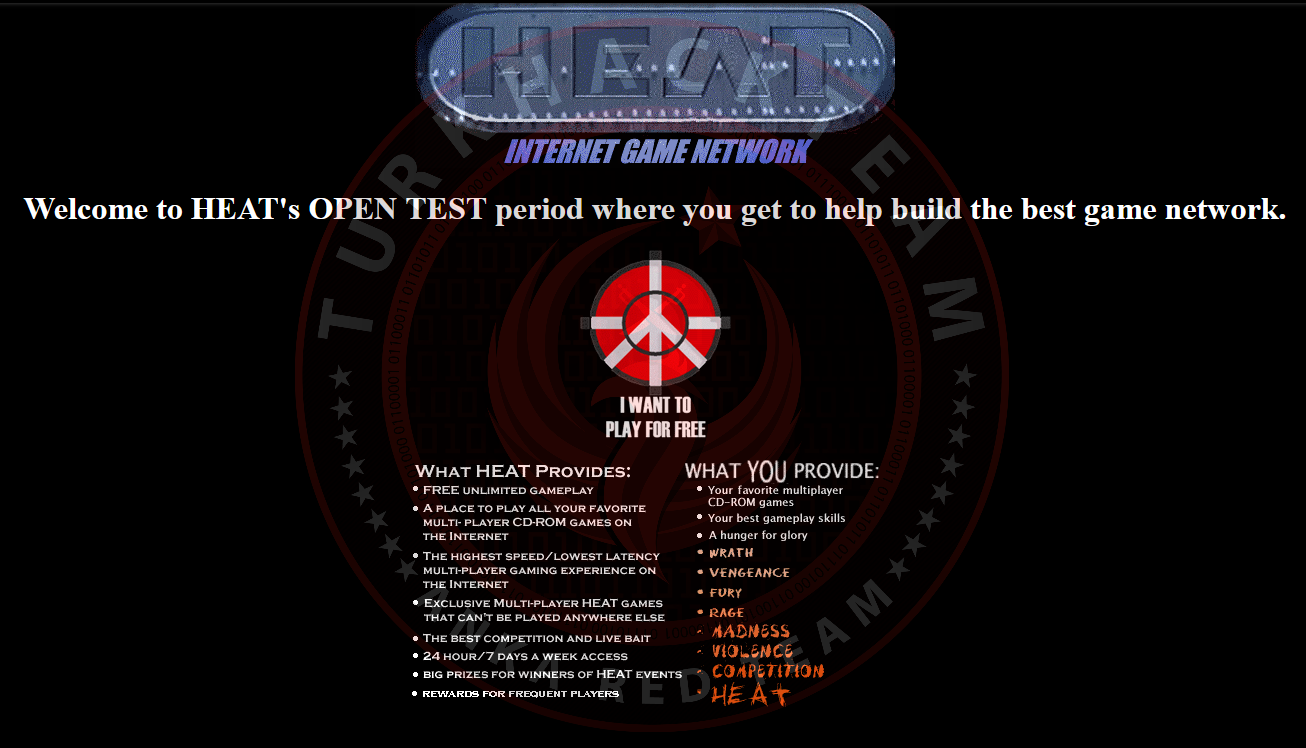
It's really an old site..
Our Response: 06/01/97

5. What is the first sentence of the first body paragraph since the last capture of 2001?
The last capture of 2021;

And here's the first sentence of the last capture;
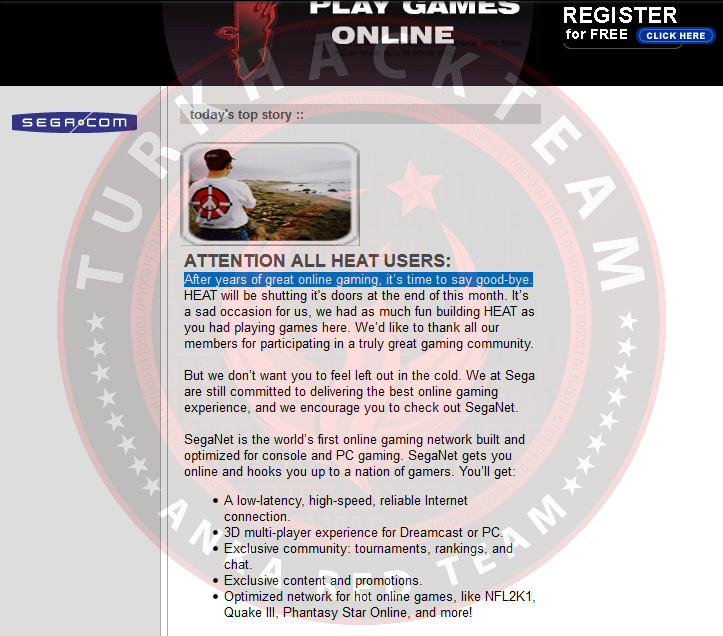
Our Response: After years of great online gaming, it's time to say good-bye.

6. Using your search engine skills, what was the name of the company responsible for the original version of the site?
Let's look for the company's motto. Let's look at the results in detail.

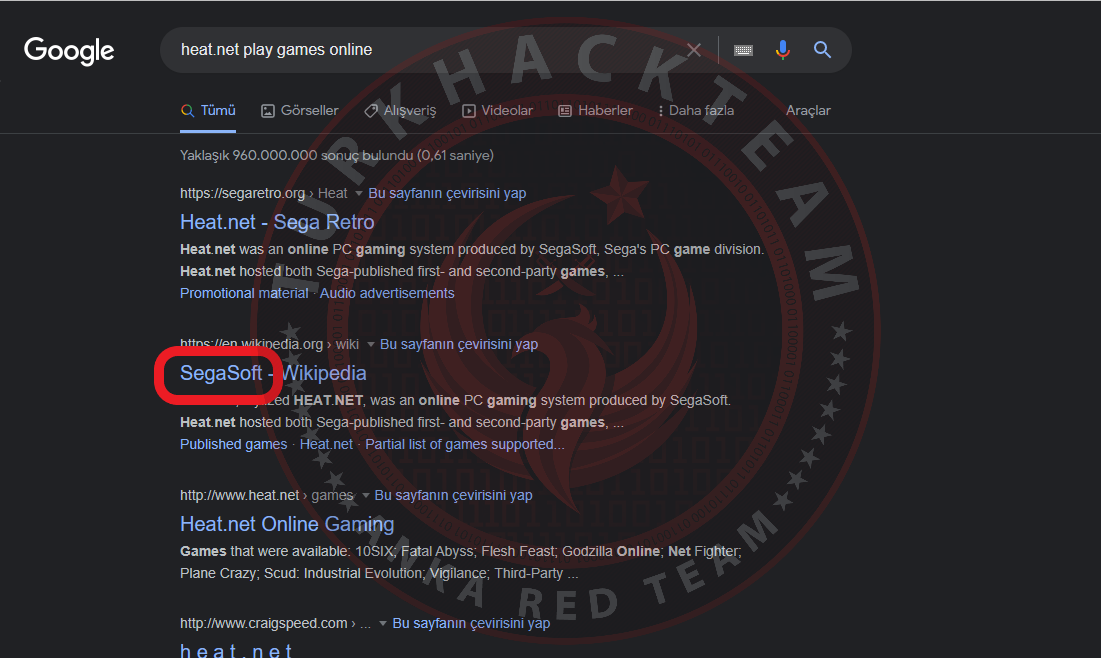
Our Response: SegaSoft

7. What does the first headline on the site say in the last capture of 2010?
Here is the last catch of 2010:

Apparently it's now an HVAC company. We can see the first title here.

Our response: Heat.net — Heating and Cooling

Task 6: Taking a look under the title of a website
We'll check the website to look for more tips for this next section.
1. How many internal links are there in the article text?
This doesn't work in a 2010 capture, so you can go to the current website in your browser.Heat.net | Heating and Cooling Information
Look at the right side of the homepage and there should be some links. "Need to Hire a Commercial Contractor?"
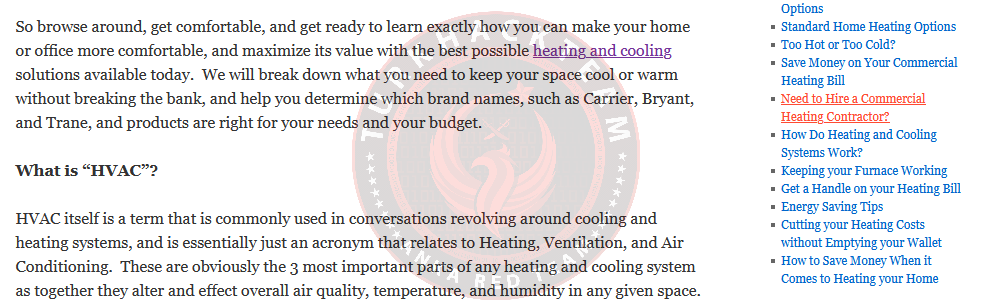
All questions in Task 6 are asked from this page.
It's pretty easy, just look at the text and count the links. You can understand what's internal by hovering over the link and verifying where it will take you. If it takes you to another heat.net page, it's internal.

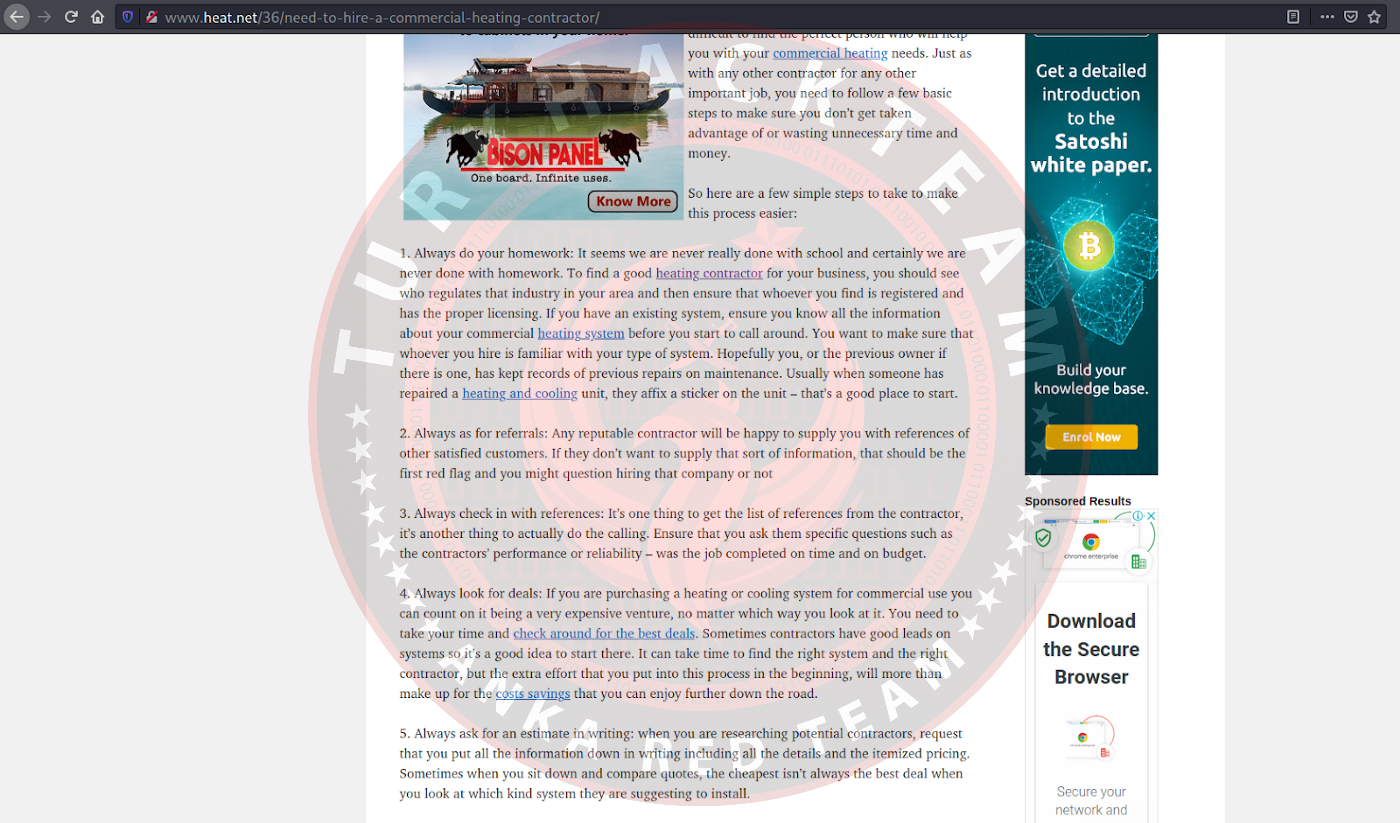
There are 5 connections available.
Our Responses: 5

2. How many external links are there in the article text?
Here, too, the idea is that when you hover over the link, it will show an external location.
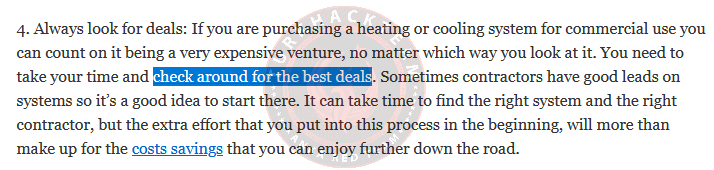
External connection 1 is available.
Our Response: 1

3. Website on the only external link to the article (this is not an advertisement)
When you hover over the link for the last question, the address of the site that takes you is our answer.

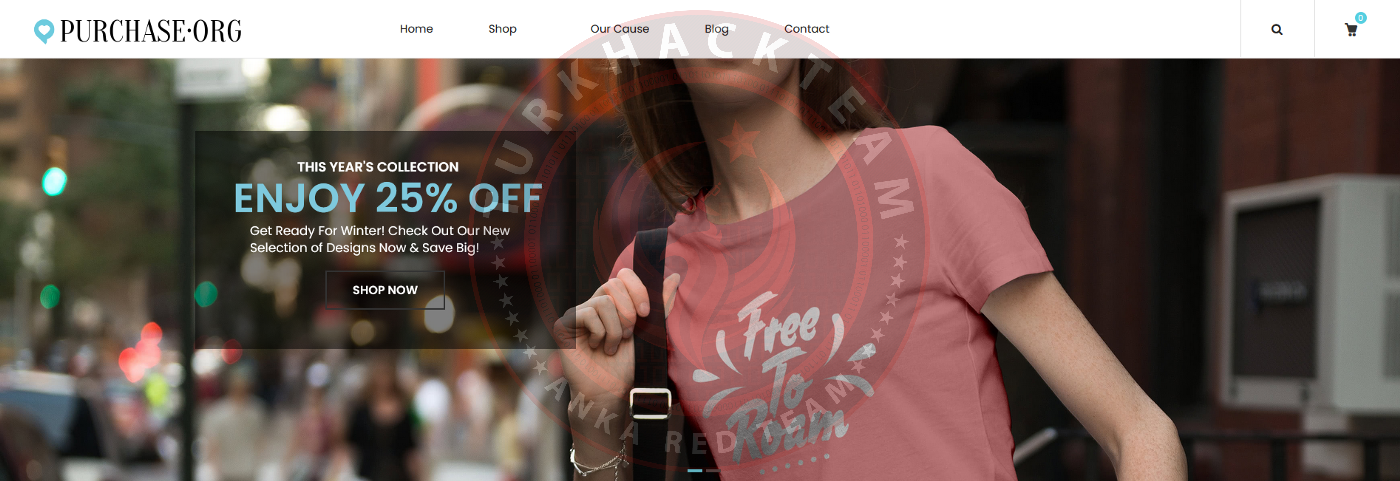
He directed us to such a site.
Our response: purchase.org

4. Try to find the Google Analytics code linked to the site
For this question, right-click anywhere on the page and choose to view the source code. We can carry out this operation by pressing CTRL + U at the same time.
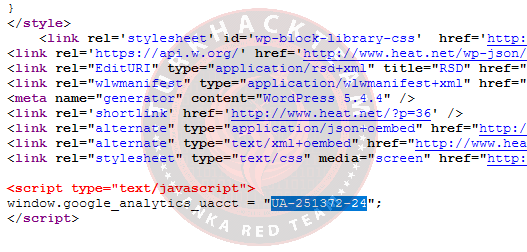
Our Response: UA-251372-24
This will lead you to the Google AdSense ID.

5. Is the Google Analytics code used on another website? Sagittarius or Nay
We can use NerdyData.com - Search The Web's Source Code for Technologies to search for the Google Adsense ID.
Here we see that only one website uses it.

Not used on any other site.
Our response: Nay

6. Is there any affiliate code embedded in the link to this website? Sagittarius or Nay
You can tell if a link has affiliate codes by looking at it. If you hover over it and it just directs you to 'www.purchase.org', no, there's no code attached to it.
But if you see a bunch of additional information, it could be an affiliate link.
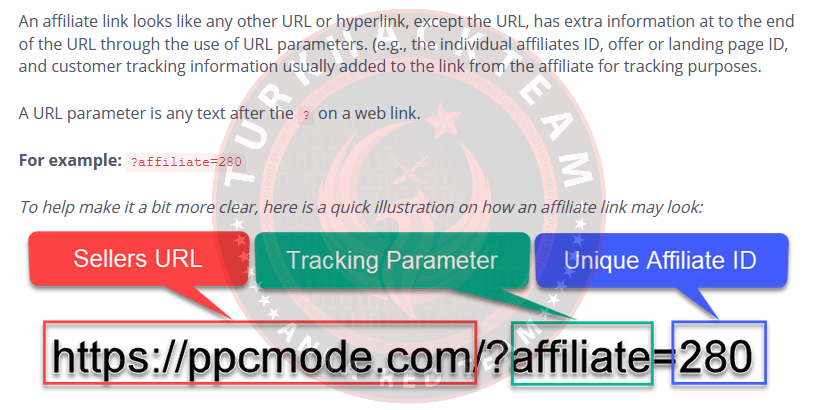
We can take this chart from THIS website which explains affiliate links a bit more if you want to read more.
This leads to the conclusion that Task 6 is ongoing.
Our response: Nay

Mission 7: Final Exam: Connect the Points
In Task 7 we are told;
The last struggle...
"Experienced OSINT researchers will tell you that chasing rabbit holes day and night without being able to make some solid connections is not OSINT.
OSINT refers to patterns that begin to emerge as you connect the dots in the analysis of data.
Congratulations! You've found that our goal is heat[.] links to a clear, interesting external site. There's a question, though: Why???
There is no affiliate code in the link, so there is no apparent financial link between the two. Maybe there is another connection.
This is your final exam and you have exactly one question.
Get busy!"
Saying.


1. Use the tools in Task 4 to confirm the connection between the two sites. Try to understand without a hint.
If you go back to Task 5 when we use the IP History Tool for 'heat.net', we can see that the website is owned by Liquid Web, L.L.
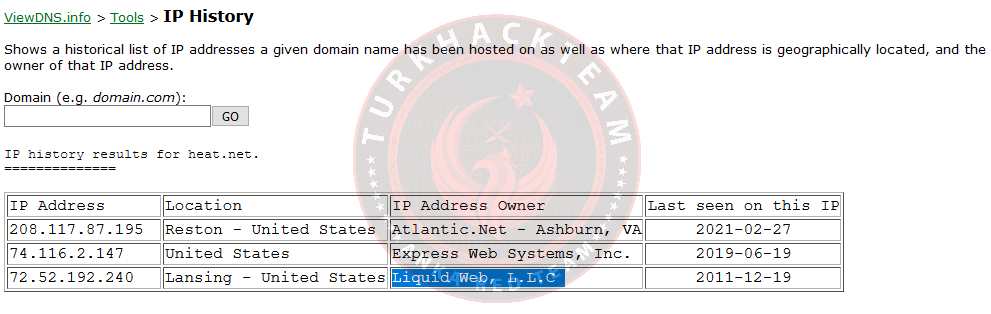
After using the same vehicle for 'purchase.org', it turned out that they both belonged to the same company.
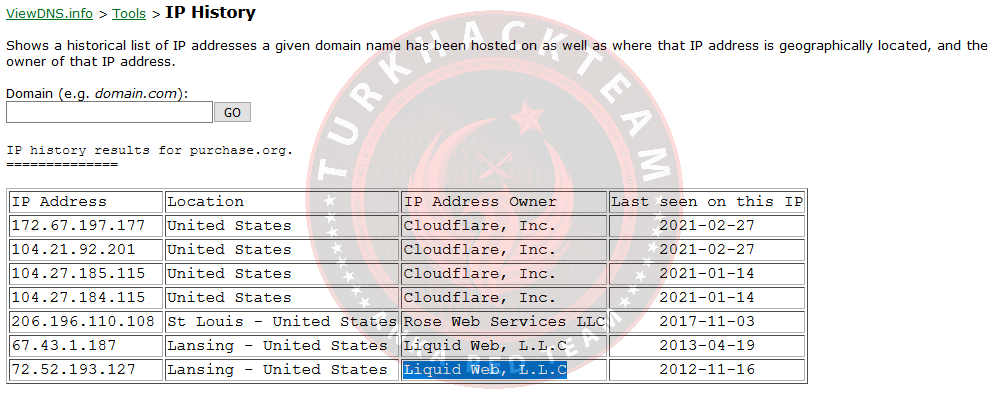
Answer to our question: Liquid Web, L.L.C

Task 8: Inquiry
We complete Task 8 by saying completed.

Mission 9: Completion
A note was left last in Task 9. The Turkish language is as follows;
A little web OSINT knowledge can go a long way in online research. A few examples of where it comes into play include all kinds of business OSINT, online scams, and even political journalism. If you want to see the most important example of the implementation of this type of research, I highly recommend taking a look at NixIntel's disclosure linking antifa.com to Russia, this is an incredible case study.
Make sure it can browse other OSINT boxes, such as:
- Searchlight IMINT Room and Geolocation for Geolocation and Image Analysis
- Google Dork room for advanced search engine operators
- OhSINT room for a little extra IMINT app
There are also two great podcasts that every OSINT practitioner should listen to on a regular basis. OSINT Curious podcast and Privacy, Security and OSINT Show.
Finally, a solid paid option that won't break the bank for OSINT training is TheOSINTion. If you liked the content of this room, you will LOVE the Business OSINT course they offer. I have no other relationship with the course than to be a satisfied customer.


Apart from that, we have successfully solved our CTF machine.
Thanks for reading. Hope to see you in another CTF solution...




Translator: @ByFelez
Subject Author @Ghost Killer
Subject:https://www.turkhackteam.org/konular/tryhackme-webosint-ctf-walkthrough-writeup.2008973/
Finally, a solid paid option that won't break the bank for OSINT training is TheOSINTion. If you liked the content of this room, you will LOVE the Business OSINT course they offer. I have no other relationship with the course than to be a satisfied customer.


Apart from that, we have successfully solved our CTF machine.

Thanks for reading. Hope to see you in another CTF solution...




Translator: @ByFelez
Subject Author @Ghost Killer
Subject:https://www.turkhackteam.org/konular/tryhackme-webosint-ctf-walkthrough-writeup.2008973/








