Today we will investigate OSI layers.
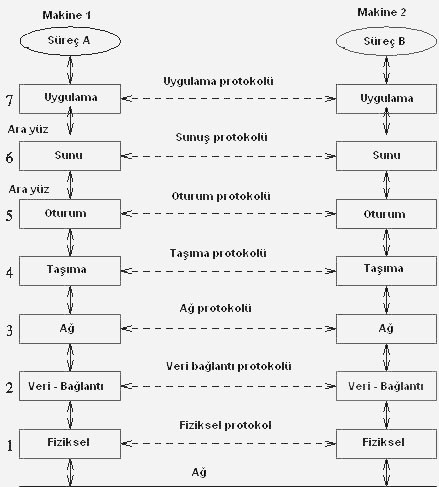
The purpose of all layers is to provide data flow to the next level.
LAYER 1 : THE BEGINNING
Layer 1 content that forms the basis of the OSI Layer;
Here, it is determined how the electrical or physical infrastructure will be followed for data transfer in the computer.
It is the place where it is decided whether the transferred data is transmitted Electrical or Radio signals.
The criteria for data in this layer is Bit. Data is encoded as 0 - 1 in this layer and this shape is moved.
The 0 and 1 sent by the sender are resolved by the receiver computer, and the 0 and 1 are sent from the receiver computer to the sender again.
Layer 2: Data Link Layer!
This layer sets the relevant rules for accessing and using the physical layer.
Access methods known as token ring or Ethernet work in this layer and these access methods process data according to their own protocols and transmit them to the other party.
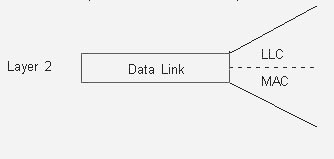
We can divide the Data Link Layer into two Groups.
1-Media Access Control(MAC)
2-Logical Link Control(LLC)
Layer 3: Network Layer(Where DDoS was tried first)
We started to come to our topic slowly. In this layer, data will now be migrated as a package and a glitch here will prevent the normal functioning of the service.
This layer has been a target for attacks since operations such as network traffic and routing will be carried out However, with the development of the systems, the attacks on this attack did not last very long. The weakness was eliminated quickly.
Layer 4: Transport Layer
TCP, UDP, SPX, protocols run on this layer. The most targeted layer for cyberattacks was this layer after layer 3. Syn 'Attacks, in other words, synchronized attacks are systems established for this Layer, in the light of technological developments on the disruption of services over this Vulnerability, Swichler, Traffic Analysis, Firewalls. Although precautions are taken, it can still be active today.
Layer 5: Session Layer(Botnets Basics)
Protocols such as PRC, NetBIOS, Named Pipes work in this Presentation layer, BotNet's foundations are slowly starting to unfold, and its first tried on this layer botnet attacks, and thus for the first time after this layer, the world's leading Trojan publishers turned their direction to Ddos and they dreamed of building a big network.
The biggest example(Mirai Botnet)
Layer 6: Presentation Layer (Defense / Attack)
Extensions like TIFF, EBCDIC, GIF, JPEG work in this layer. Encryption, compression and decompression of data in this layer is done in this layer. Its major task is to make this layer understand the sender's packet in the most understandable way for the receiver.
Layer 7: Application Layer (Botnet Invasion- Trojen - PHISHING )
SH, telnet, FTP, TFTP, SMTP, SNMP, HTTP, DNS protocols and browsers work on this layer.
Mails - Dns providers all work on this layer. The most advanced of the attack methods developed until today are applied on this layer. This is the layer protected by protection companies such as the million-dollar Cloudflare. Let's share with you some protocols that layer 7 was attacked.
FTP vb. - Defacer Hacking, PHISHING Sites Many elements such as Rat / Trojan broadcasting are served through these protocols.
Source:https://www.turkhackteam.org/web-se...i-katmanlarinda-zaafiyet-incelemesi-xmit.html
Translator: Thekoftte

The purpose of all layers is to provide data flow to the next level.
LAYER 1 : THE BEGINNING
Layer 1 content that forms the basis of the OSI Layer;
Here, it is determined how the electrical or physical infrastructure will be followed for data transfer in the computer.
It is the place where it is decided whether the transferred data is transmitted Electrical or Radio signals.
The criteria for data in this layer is Bit. Data is encoded as 0 - 1 in this layer and this shape is moved.
The 0 and 1 sent by the sender are resolved by the receiver computer, and the 0 and 1 are sent from the receiver computer to the sender again.
Layer 2: Data Link Layer!
This layer sets the relevant rules for accessing and using the physical layer.
Access methods known as token ring or Ethernet work in this layer and these access methods process data according to their own protocols and transmit them to the other party.
We can divide the Data Link Layer into two Groups.
1-Media Access Control(MAC)
2-Logical Link Control(LLC)

Layer 3: Network Layer(Where DDoS was tried first)
We started to come to our topic slowly. In this layer, data will now be migrated as a package and a glitch here will prevent the normal functioning of the service.
This layer has been a target for attacks since operations such as network traffic and routing will be carried out However, with the development of the systems, the attacks on this attack did not last very long. The weakness was eliminated quickly.
Layer 4: Transport Layer
TCP, UDP, SPX, protocols run on this layer. The most targeted layer for cyberattacks was this layer after layer 3. Syn 'Attacks, in other words, synchronized attacks are systems established for this Layer, in the light of technological developments on the disruption of services over this Vulnerability, Swichler, Traffic Analysis, Firewalls. Although precautions are taken, it can still be active today.
Layer 5: Session Layer(Botnets Basics)
Protocols such as PRC, NetBIOS, Named Pipes work in this Presentation layer, BotNet's foundations are slowly starting to unfold, and its first tried on this layer botnet attacks, and thus for the first time after this layer, the world's leading Trojan publishers turned their direction to Ddos and they dreamed of building a big network.
The biggest example(Mirai Botnet)
Layer 6: Presentation Layer (Defense / Attack)
Extensions like TIFF, EBCDIC, GIF, JPEG work in this layer. Encryption, compression and decompression of data in this layer is done in this layer. Its major task is to make this layer understand the sender's packet in the most understandable way for the receiver.
Layer 7: Application Layer (Botnet Invasion- Trojen - PHISHING )
SH, telnet, FTP, TFTP, SMTP, SNMP, HTTP, DNS protocols and browsers work on this layer.
Mails - Dns providers all work on this layer. The most advanced of the attack methods developed until today are applied on this layer. This is the layer protected by protection companies such as the million-dollar Cloudflare. Let's share with you some protocols that layer 7 was attacked.
FTP vb. - Defacer Hacking, PHISHING Sites Many elements such as Rat / Trojan broadcasting are served through these protocols.
Source:https://www.turkhackteam.org/web-se...i-katmanlarinda-zaafiyet-incelemesi-xmit.html
Translator: Thekoftte
Moderatör tarafında düzenlendi:




