Hundreds of website are being hacked each passing day. And you know why?
How does web know what we want?
What are the programming languages used in creating websites?
How can we gather informations from websites?
What is Web Technologies?
The result of the combination of more than one web technology is called "Web Technologies". Web technologies have more than one secondary element.
Secondary Elements of Web Technologies
Web Architect
HTML
HTML Encoding
URL
URL Encoding
What is Web Architect?
Jobs of web architect are creating and editing web software or web design.
HTML
HTML has an important place in web technologies. We've all heard of HTML. It is a language that helps create HTML websites.
HTML Encoding
HTML Encoding helps your website is displayed properly.
URL
We can say that URL is website basically. In the beginning of URL, there is 'http://' or 'https://'. In the middle of URL, there is main link such as www.turkhackteam. In the end of URL, there is extension such as '.com', '.org', etc.
URL Encoding
URL encoding is used to create valid and secure url address. Url encoding is being able to create "HTML".
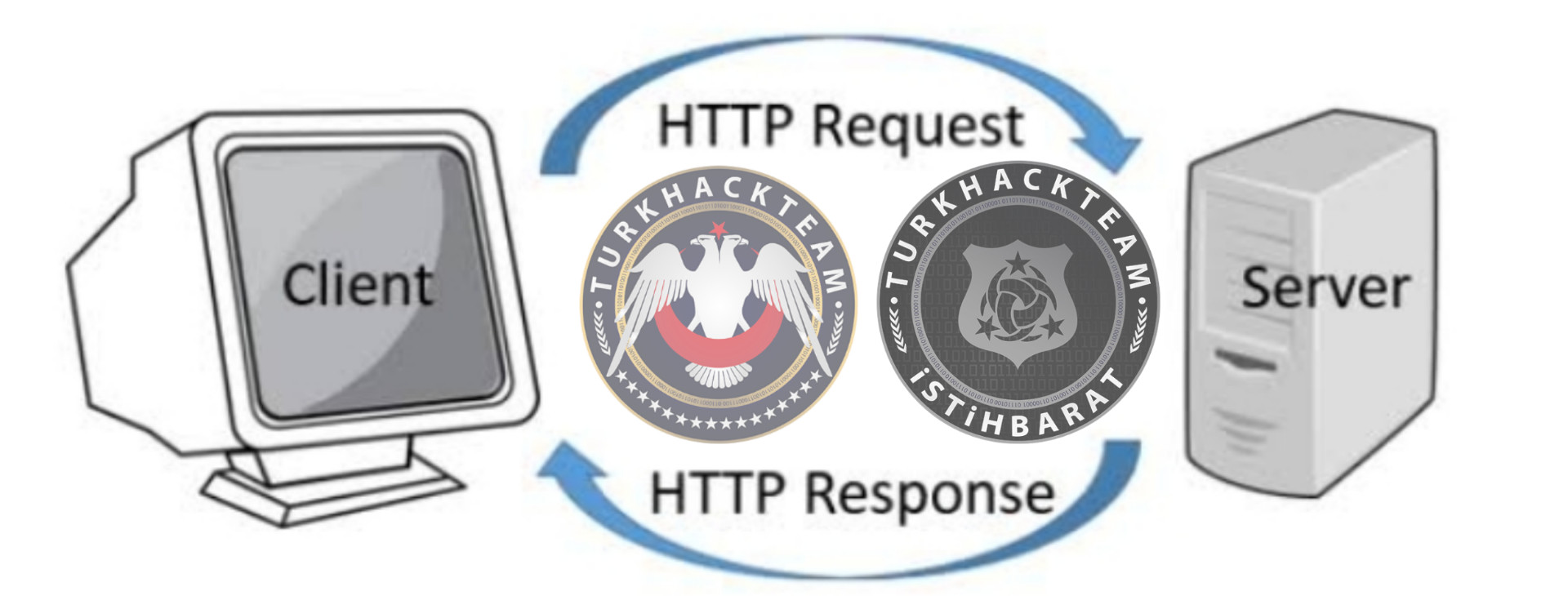
What are HTTP Basics?
What is HTTP?
We need to know what is HTTP before its basics.
Http leads to users who wanna visit web address. It makes to enter website easier. But http is not that secure.

What is HTTP Protocol?
Let's start with an example.
Let's say you entered into a website. http will be connected with the client while that website's server forwarding you to that page. When client responded, that means you're in the website. These events are happening in only split seconds
What is HTTP Cookie?
HTTP sends its own cookies to URLs that related to itself. Website owners can save these cookies if they want to.
What is HTTP Session?
It's used to recognize a visitor in http related website. It controls activities of each users' and they can show appropriate ads.
What is Burp Suite?
Burp Suite is a Java based Web Penetration Testing framework. It has become an industry standard suite of tools used by information security professionals. Burp Suite helps you identify vulnerabilities and verify attack vectors that are affecting web applications. Because of its popularity and breadth as well as depth of features, we have created this useful page as a collection of Burp Suite knowledge and information.

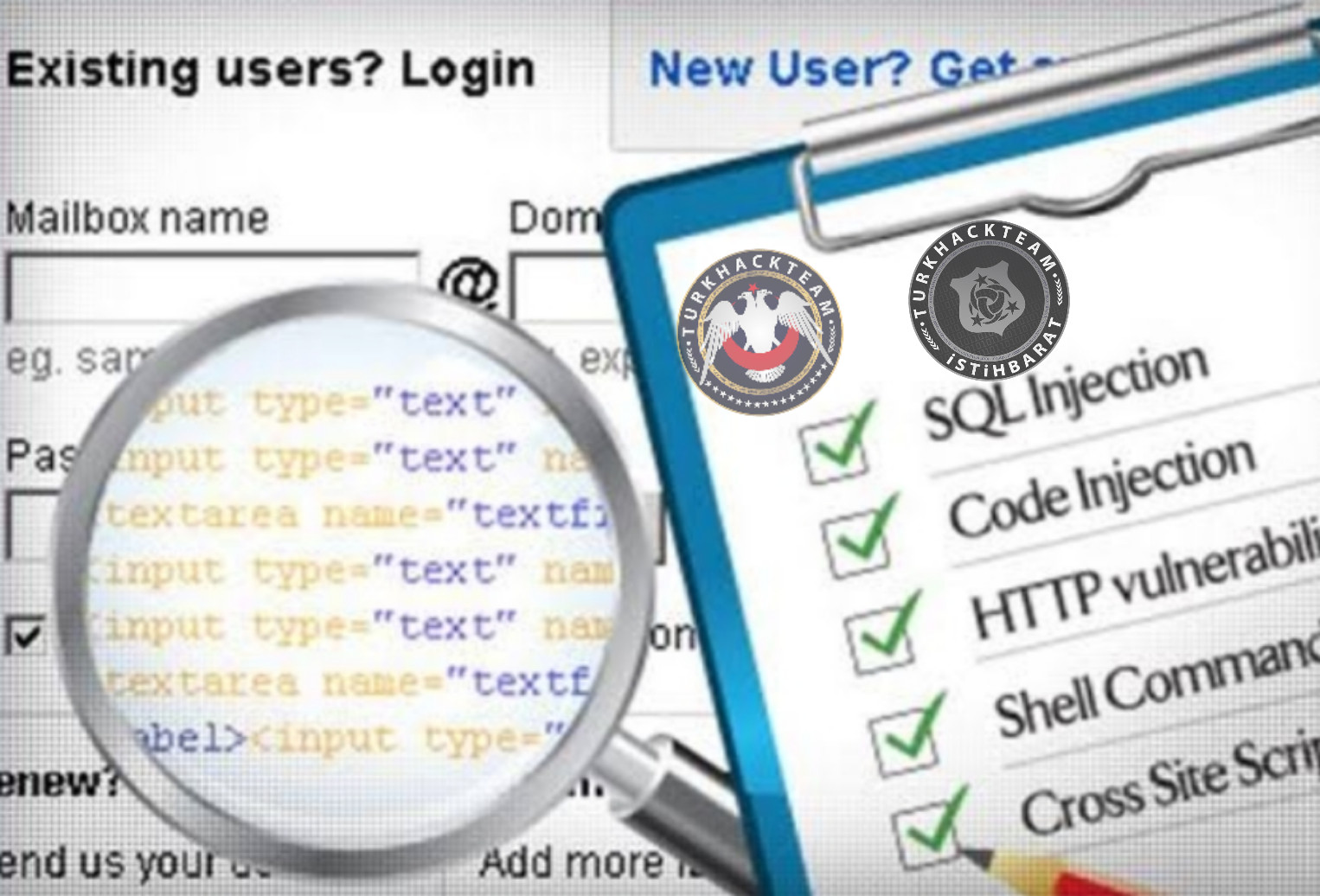
What are website vulnerabilities?
Website are being hacked in these days. Most of them happened because of security vulnerabilities or bad firewall.
Website Vulnerabilities
DoS Attack
Command Injection
SQL Injection
Cross Site Scripting (XSS)
Insecure Direct Object References (IDOR)
File Inclusion
Cross Site Request Forgery (CSRF)
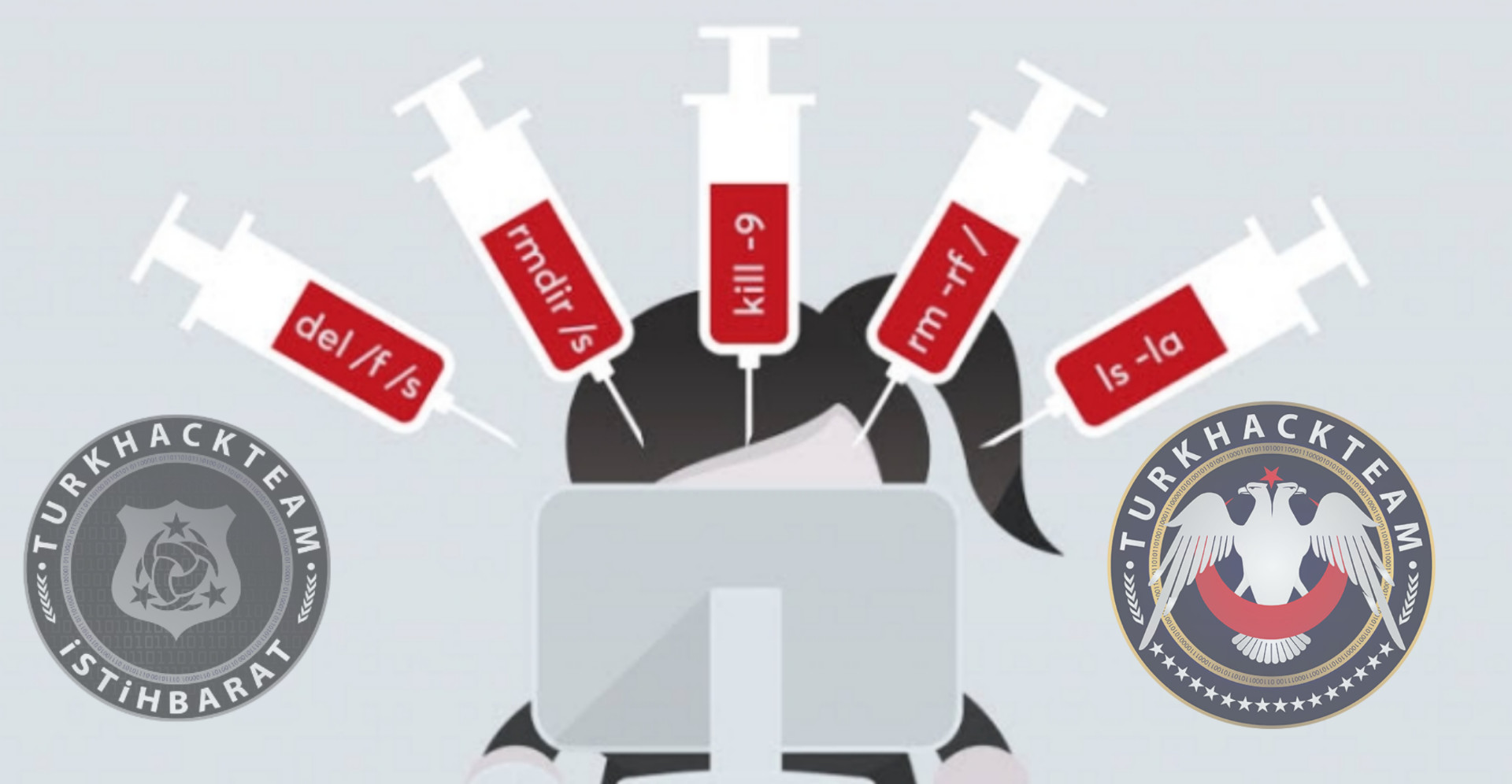
What is DoS?
A Denial-of-Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic, or sending it information that triggers a crash. In both instances, the DoS attack deprives legitimate users (i.e. employees, members, or account holders) of the service or resource they expected.
Command Injection
I've told you that http is not that secure. Command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell.
SQL Injection
SQL injection is a code injection technique that might destroy your database. SQL injection is one of the most common web hacking techniques. SQL injection is the placement of malicious code in SQL statements, via web page input.

Cross Site Scripting
Cross-site scripting is a type of security vulnerability typically found in web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy.

Insecure Direct Object References (IDOR)
Insecure direct object references (IDOR) are a type of access control vulnerability that arises when an application uses user-supplied input to access objects directly.
File Inclusion
Remote File Inclusion (RFI) and Local File Inclusion (LFI) are vulnerabilities that are often found in poorly-written web applications. These vulnerabilities occur when a web application allows the user to submit input into files or upload files to the server.
Cross Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which theyre currently authenticated. With a little help of social engineering (such as sending a link via email or chat), an attacker may trick the users of a web application into executing actions of the attackers choosing.
How does web know what we want?
What are the programming languages used in creating websites?
How can we gather informations from websites?
What is Web Technologies?
The result of the combination of more than one web technology is called "Web Technologies". Web technologies have more than one secondary element.
Secondary Elements of Web Technologies
Web Architect
HTML
HTML Encoding
URL
URL Encoding
What is Web Architect?
Jobs of web architect are creating and editing web software or web design.
HTML
HTML has an important place in web technologies. We've all heard of HTML. It is a language that helps create HTML websites.
HTML Encoding
HTML Encoding helps your website is displayed properly.
URL
We can say that URL is website basically. In the beginning of URL, there is 'http://' or 'https://'. In the middle of URL, there is main link such as www.turkhackteam. In the end of URL, there is extension such as '.com', '.org', etc.
URL Encoding
URL encoding is used to create valid and secure url address. Url encoding is being able to create "HTML".
What are HTTP Basics?
What is HTTP?
We need to know what is HTTP before its basics.
Http leads to users who wanna visit web address. It makes to enter website easier. But http is not that secure.

What is HTTP Protocol?
Let's start with an example.
Let's say you entered into a website. http will be connected with the client while that website's server forwarding you to that page. When client responded, that means you're in the website. These events are happening in only split seconds

What is HTTP Cookie?
HTTP sends its own cookies to URLs that related to itself. Website owners can save these cookies if they want to.
What is HTTP Session?
It's used to recognize a visitor in http related website. It controls activities of each users' and they can show appropriate ads.
What is Burp Suite?
Burp Suite is a Java based Web Penetration Testing framework. It has become an industry standard suite of tools used by information security professionals. Burp Suite helps you identify vulnerabilities and verify attack vectors that are affecting web applications. Because of its popularity and breadth as well as depth of features, we have created this useful page as a collection of Burp Suite knowledge and information.

What are website vulnerabilities?
Website are being hacked in these days. Most of them happened because of security vulnerabilities or bad firewall.
Website Vulnerabilities
DoS Attack
Command Injection
SQL Injection
Cross Site Scripting (XSS)
Insecure Direct Object References (IDOR)
File Inclusion
Cross Site Request Forgery (CSRF)

What is DoS?
A Denial-of-Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic, or sending it information that triggers a crash. In both instances, the DoS attack deprives legitimate users (i.e. employees, members, or account holders) of the service or resource they expected.
Command Injection
I've told you that http is not that secure. Command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell.

SQL Injection
SQL injection is a code injection technique that might destroy your database. SQL injection is one of the most common web hacking techniques. SQL injection is the placement of malicious code in SQL statements, via web page input.

Cross Site Scripting
Cross-site scripting is a type of security vulnerability typically found in web applications. XSS attacks enable attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy.

Insecure Direct Object References (IDOR)
Insecure direct object references (IDOR) are a type of access control vulnerability that arises when an application uses user-supplied input to access objects directly.
File Inclusion
Remote File Inclusion (RFI) and Local File Inclusion (LFI) are vulnerabilities that are often found in poorly-written web applications. These vulnerabilities occur when a web application allows the user to submit input into files or upload files to the server.
Cross Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which theyre currently authenticated. With a little help of social engineering (such as sending a link via email or chat), an attacker may trick the users of a web application into executing actions of the attackers choosing.
Source: https://www.turkhackteam.org/web-server-guvenligi/1911256-web-uygulama-guvenligi.html
Translator: R4V3N
Moderatör tarafında düzenlendi:





