- 23 Nis 2020
- 297
- 1
Hello everyone, in this topic i am going to talk about "what is dos/ddos",their specify.
What is DoS and DDoS
DoS: DoS is also known as the Denial of Service Attack; It is a type of attack made by a single person or a computer. This Denial of Service Attack occurs when the target system sends packet data beyond the bandwidth limit. Shortly, the target system cannot respond more requests.. The service will be disabled because the system cannot answer the packets. DOS is easy to prevent.
DDoS: The only difference of this type of attack from DoS is by attacking same time from two or more computers. Data will be sent to the target system as in DoS. Since this data sees it coming from many places, it wont be able to answer all of it and a service deactivation attack will occur. This attack is difficult to prevent.
This type of attacks being difference due to internet connection.
If bandwidth is targeted in DoS / DDoS attacks, there is no way to prevent these attacks. Lets give a example about this. The passenger limit for a bus is 75. If you fill all 75 places, no other passenger will be able to sit. DoS / DDoS attacks are the same. After make overload, the system will be out of service.
Mostly Used Types
We mostly see this attack types;
SYN Flood
HTTP Flood
UDP Flood
DNS Flood
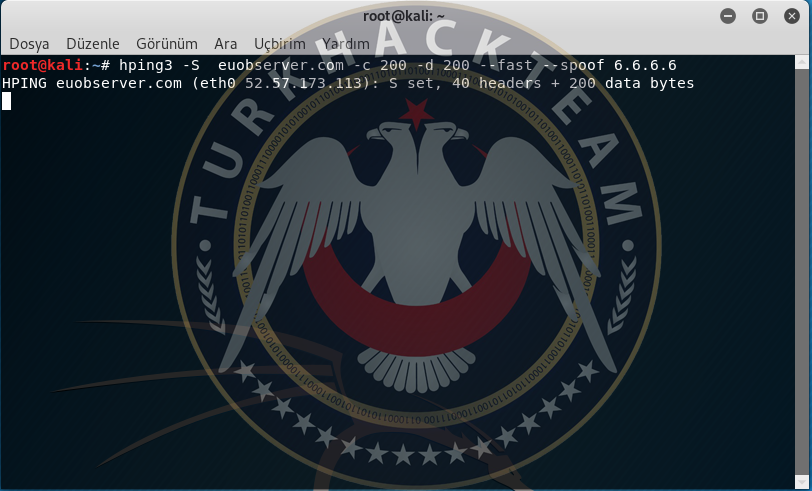
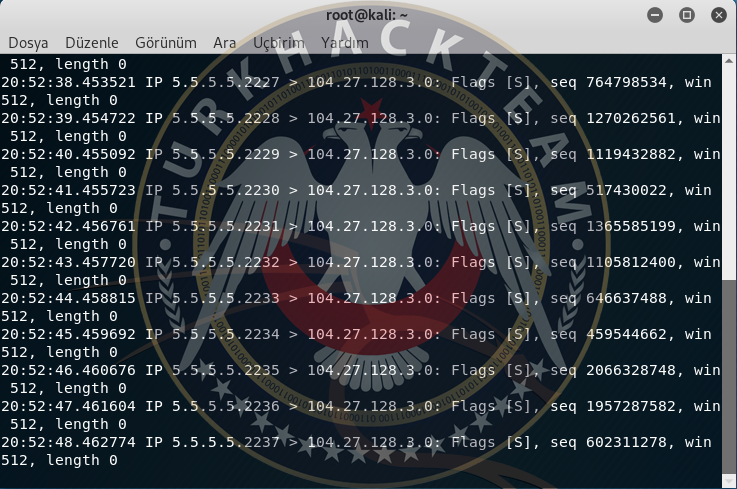
SYN Flood:SYN Flood is maded by sending more than capacity SYN packets to the target system. SYN Flood is an attack against the weak port of the target system. It occurs by sending more packets than the target system can take. While the attack is happening, the attacker uses to spoof.The capacity of the target system is important in this attack. Here is example of SYN Flood
HTTP Flood:HTTP Flood is an attack that made with HTTP protocol. It means the target is doing web streaming using port 80 and secure broadcasting using port 443. This test is doing for efficient usage of website. Here is example of HTTP Flood



UDP Flood:UDP Flood attacks target UDP protocols. UDP protocols can not control the source so there is no solution method for UDP Flood attacks. In UDP Flood attacks the most efficient way is attack to the DNS protocols. We can also use spoofing in this attacks because the target system can not block IP adresses. Here is example of UDP Flood

DNS Flood:This type of attack is done by sending a DNS request until the DNS servers crushed. Spoofing is also using in this attack. İn this attacks usually IP adresses shown as coming from a government site. When faced with tis attacks, it can be really difficult to prevent this. A misunderstanding in this type of attack is that the attack on every UDP 53 port is thought to be a DNS Flood. Here is example of the DNS Flood.

Source: https://www.turkhackteam.org/siber-...dir-en-cok-kullanilan-cesitleri-nelerdir.html
Translator: Baphomet
What is DoS and DDoS
DoS: DoS is also known as the Denial of Service Attack; It is a type of attack made by a single person or a computer. This Denial of Service Attack occurs when the target system sends packet data beyond the bandwidth limit. Shortly, the target system cannot respond more requests.. The service will be disabled because the system cannot answer the packets. DOS is easy to prevent.
DDoS: The only difference of this type of attack from DoS is by attacking same time from two or more computers. Data will be sent to the target system as in DoS. Since this data sees it coming from many places, it wont be able to answer all of it and a service deactivation attack will occur. This attack is difficult to prevent.
This type of attacks being difference due to internet connection.
If bandwidth is targeted in DoS / DDoS attacks, there is no way to prevent these attacks. Lets give a example about this. The passenger limit for a bus is 75. If you fill all 75 places, no other passenger will be able to sit. DoS / DDoS attacks are the same. After make overload, the system will be out of service.
Mostly Used Types
We mostly see this attack types;
SYN Flood
HTTP Flood
UDP Flood
DNS Flood
SYN Flood:SYN Flood is maded by sending more than capacity SYN packets to the target system. SYN Flood is an attack against the weak port of the target system. It occurs by sending more packets than the target system can take. While the attack is happening, the attacker uses to spoof.The capacity of the target system is important in this attack. Here is example of SYN Flood


HTTP Flood:HTTP Flood is an attack that made with HTTP protocol. It means the target is doing web streaming using port 80 and secure broadcasting using port 443. This test is doing for efficient usage of website. Here is example of HTTP Flood



UDP Flood:UDP Flood attacks target UDP protocols. UDP protocols can not control the source so there is no solution method for UDP Flood attacks. In UDP Flood attacks the most efficient way is attack to the DNS protocols. We can also use spoofing in this attacks because the target system can not block IP adresses. Here is example of UDP Flood

DNS Flood:This type of attack is done by sending a DNS request until the DNS servers crushed. Spoofing is also using in this attack. İn this attacks usually IP adresses shown as coming from a government site. When faced with tis attacks, it can be really difficult to prevent this. A misunderstanding in this type of attack is that the attack on every UDP 53 port is thought to be a DNS Flood. Here is example of the DNS Flood.

Source: https://www.turkhackteam.org/siber-...dir-en-cok-kullanilan-cesitleri-nelerdir.html
Translator: Baphomet
Moderatör tarafında düzenlendi:





