- 7 Tem 2013
- 8,208
- 4
- 690



HiveJack is a tool that can be used during internal penetration testing to reveal windows credentials from a compromised host. The system allows for dumping the security and sam registry hives, provides the option to delete these files to clear the trace after being copied to the attacker machines.


This is an repetitive process usually, the next step when an attacker gains root access to compromised host dumping hives values. Time is invaluable when it comes to internal penetration testing.


So HiveJack saves you time on dumping and deleting files. You'll never have to remember the command to perform processes.


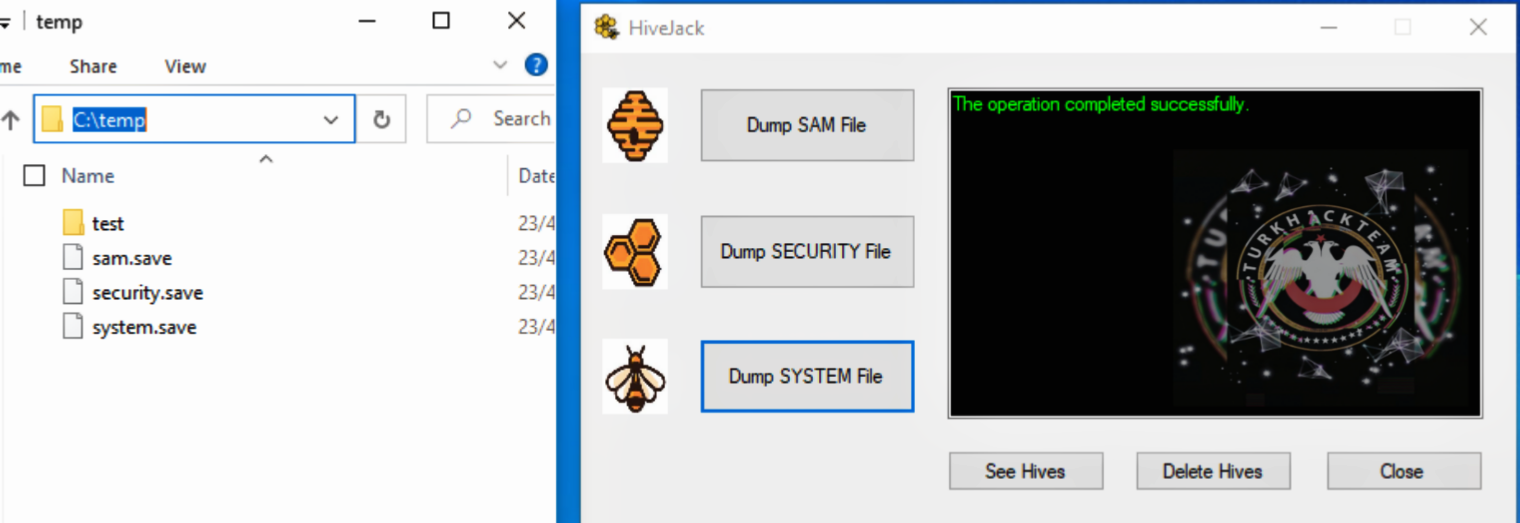
files dumped in the compromised host c:\temp\ path (dump system file)
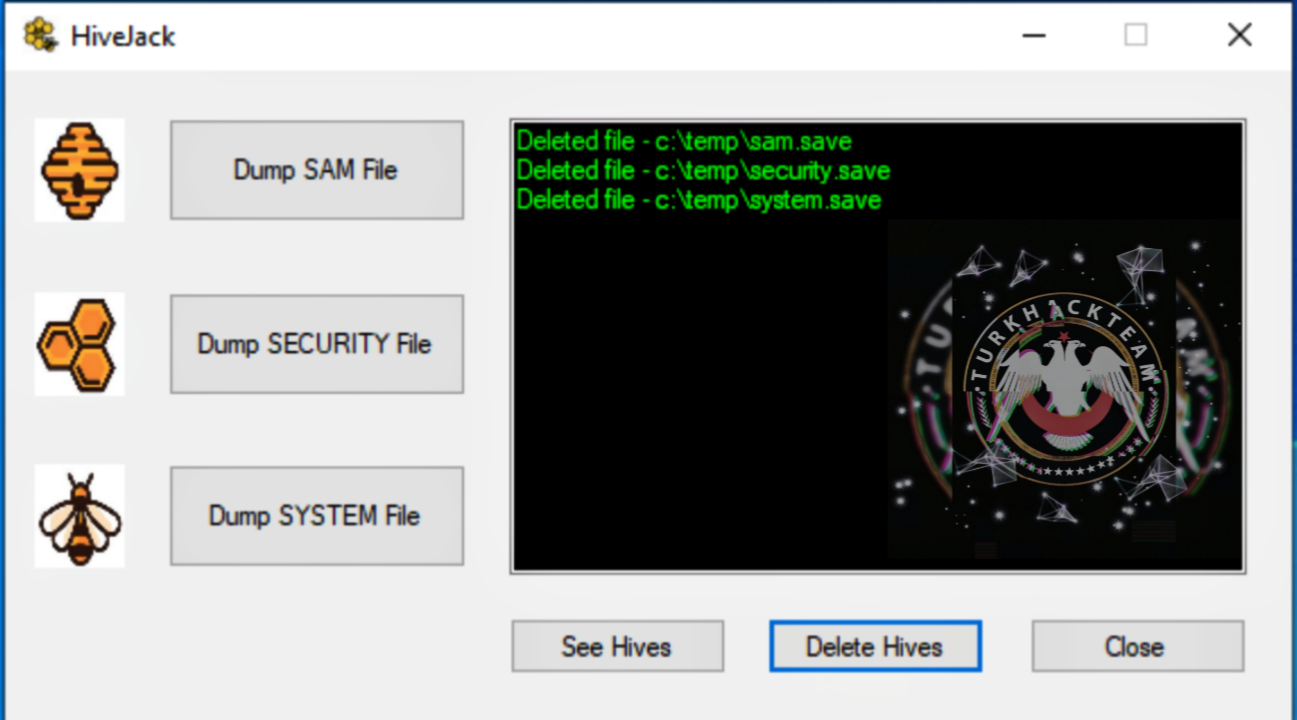
Files are successfully deleted from the compromised host when the Delete Hives button is clicked.
Hives is a subkey and value group that contains a set of supporting files that are loaded into memory when the operating system starts or user logs in


registry files have two formats:
standart format: windows 2000 support, also later versions of windows for backward-compatibility
latest format: supported starting from Windows XP
HKEY_CURRENT_USER, HKEY_LOCAL_MACHINE \ SAM, HKEY_LOCAL_MACHINE \ Security and HKEY_USERS.DEFAULT; all other hives use the latest format.


During internal penetration testing, the attacker usually wants to make a lateral movement from one host to another and account credentials are usually required to switch from one host to another. HiveJack can collect credentials through system hives.


HiveJack is a useful tool when the attacker successfully gains local administrator or system privileges on one of the compromised hosts. You can use registry hives to gain more access within the network attacker. These hives will allow an attacker to capture the password hash of system users. you can use a tool like secretsdump by dumping registry hives into the attacking box


Once the password hashes are obtained, it opens the door to a variety of attacks such as hash switching, pushing, or password cracking to perform a lateral move within the network


Once the hives files are copied to the attacking machine, it is good to delete files from the temporary folder to prevent important files leaking or cleaning traces.


please make sure you have a temporary folder on the compromised host's C: drive, before dumping registry hives.
Source: https://www.turkhackteam.org/siber-guvenlik/1916818-hivejack-nedir.html
Translator Gauloran
Son düzenleme:





