A CSRF attack forces an authenticated user(victim) to send a forged HTTP request, including the victim's session cookie to a vulnerable web application which allows the attacker to force the victim's browser to generate request such that the vulnerable app perceives as legitimate requests from the victim.
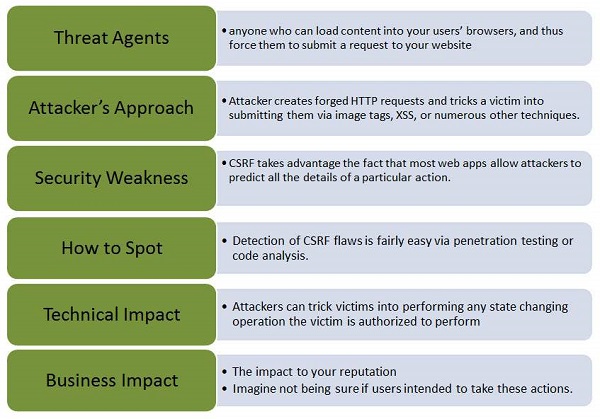
Let us understand Threat Agents, Attack Vectors, Security Weakness, Technical Impact and Business Impacts of this flaw with the help of simple diagram.
Example
Below is a classic example of CSRF :
1. Let us say, the vulnerable app sends a state changing request as a plain text without any encryption.
2. Now the hacker constructs a request that will transfer money from the victim's account to the attacker's account by embedding the request in an image that is stored on various sites under the attacker's control:
Hands ON
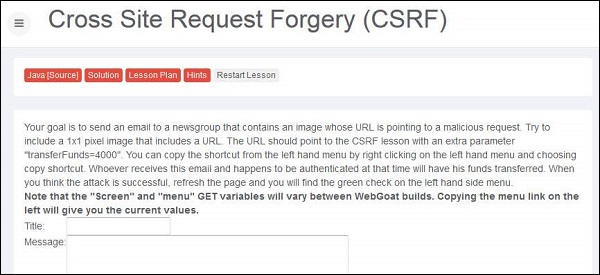
1 .Let us perform a CSRF forgery by embedding a javascript into an image. The snapshot of the problem is listed below.
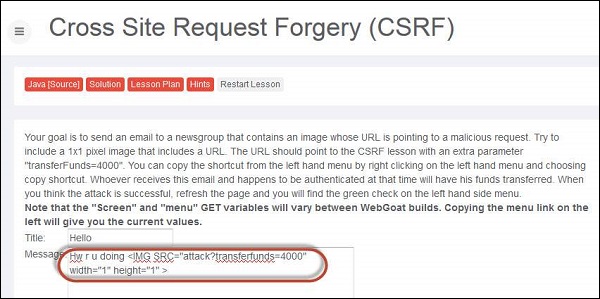
2 .Now we need to mock up the transfer into a 1x1 image and make the victim to click on the same.
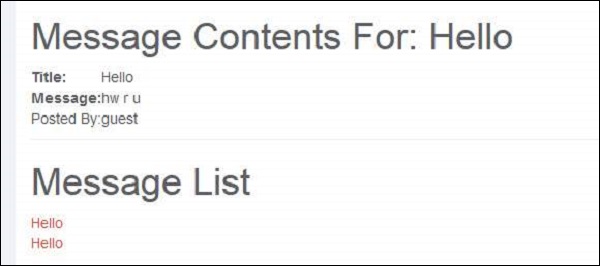
3 .Upon submitting the message, the message is displayed as highlighted below.
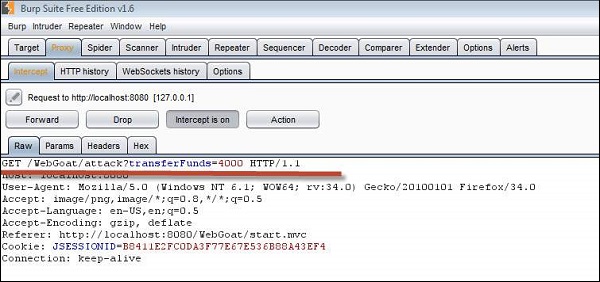
3 .Now if the victim clicks the below URL, the transfer would be executed which can be found be intercepting the user action using burp suite. We are able to see the transfer by spotting it in Get message as shown below.
4 .Now upon clicking ******* the lesson completion mark would be shown.
Preventing Mechanisms
CSRF can be a****ed by creating an unique token in a hidden field which would be sent in the body of the HTTP request rather than in an URL, which is more prone to exposure.
Forcing the user to reauthenticate or proving that they are a user in order to protect CSRF (e.g - CAPTCHA).
Let us understand Threat Agents, Attack Vectors, Security Weakness, Technical Impact and Business Impacts of this flaw with the help of simple diagram.

Example
Below is a classic example of CSRF :
1. Let us say, the vulnerable app sends a state changing request as a plain text without any encryption.
Kod:
[url]http://bankx.com/app?action=transferFund&amount=3500&destinationAccount=4673243243[/url]
Kod:
<img src="http://bankx.com/app?action=transferFunds&amount=14000&destinationAccount=attackersAcct#" width="0" height="0" />Hands ON
1 .Let us perform a CSRF forgery by embedding a javascript into an image. The snapshot of the problem is listed below.

2 .Now we need to mock up the transfer into a 1x1 image and make the victim to click on the same.

3 .Upon submitting the message, the message is displayed as highlighted below.

3 .Now if the victim clicks the below URL, the transfer would be executed which can be found be intercepting the user action using burp suite. We are able to see the transfer by spotting it in Get message as shown below.

4 .Now upon clicking ******* the lesson completion mark would be shown.
Preventing Mechanisms
CSRF can be a****ed by creating an unique token in a hidden field which would be sent in the body of the HTTP request rather than in an URL, which is more prone to exposure.
Forcing the user to reauthenticate or proving that they are a user in order to protect CSRF (e.g - CAPTCHA).
Source : https://www.tutorialspoint.com/security_testing/cross_site_request_forgery.htm




