
Identity Hunt Attacking
One Scenario example of a identity hunt swindler's attempt;
A fake email is sent to so many users.
This e-mail says "There is a copyright in your one post". Also, It says "You need to renew your password. Go to instagramfakecopyright.cf"
That mail:
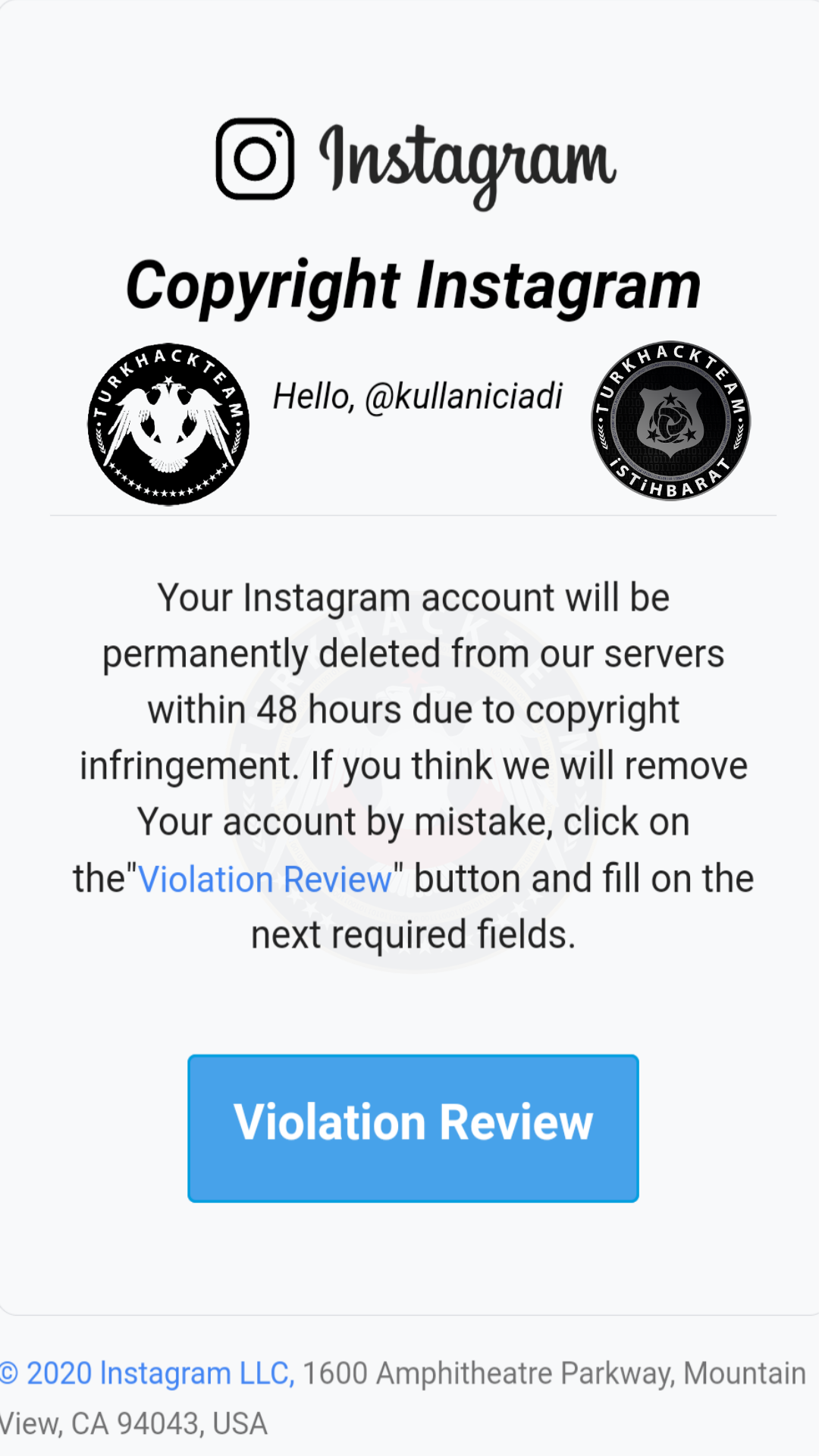
You need to use VPN for clicking that links. There can be iplogger or something.

As you can see, we are seeing a fake script. There will be many people believe that.

This form wants your username password, your e-mail and e-mail password. You can protect yourself with reading my this heading; "How can we protect ourselves for identity hunting"
You can see something with clicking that emails. For example;
User directs instagramfakescript.cf with clicking that link. That page wants your password and your informations. And, Attacker steals your original password for access to safe zone in Instagram web. User directs to original password renewing page. But attacker started malwares in backround. So, while that user directing to real password into renewing page, the attacker reaches that password.

E-mail Identity Hunt Swindlers
E-mail identity hunting is a number game. An attacker who sends thousands of short messages for fraud can clarify the information and aggregate amounts even if only a small percentage of recipients decrease for the trick. Attackers use some technics for increase their successes.
Firstly, they spend much effort for imitate real e-mails. They need to make their fake e-mails like legal e-mails. So, they use some logos, text characters, signatures etc.
Also, they try to make victim feel urgent. They threat victims. For example; they can say "Your e-mail's duration almost full" or something like this. If victim believes this, he/she will be vulnerable.
While attackers are taking their url's, they try to make like real url. For example;


How can we protect ourselves from identity hunting ?
Users need to be awake. Fake e-mails generally contain mistakes. Sometimes they have text mistakes or domain mistakes. So, users must think "Why did I get this e-mail".
Business accounts, can use these steps for decrease spear identity hunting and identity hunting attacks;
Two factored verification (2FA)is a best method for identity attacks. Because it adds an extra verification layer. 2FA is based on two things that users have; password and username or like devices somethings user had. If workers' personal informations are violated, 2FA blocks to use that informations harmfuly. Because that informations not enough for sign in.
Also, business accounts must use strict password management policy. Workers frequently need to change their passwords. They shouldn't use same password for a lot applications.
Don't click unnecessary links is a way of decrease identity hunting attacks.
Source:
Translater: M3m0ry
Son düzenleme:





