Hello, today I'll give you information about how to block a DDoS attack,
Titles of How to block DDoS Attack
What is DDoS attack and How Does It Work?
Denial of Service attacks (DoS)
Distributed Denial of Service (DDoS)
Amplification Attacks
What are the types of DDoS Attacks?
How to protect yourself from an attack?
Denial of Service Attacks (DDos), can make any web site offline. Even Google and GitHub with their enormous resources may struggle when fighting against a DDoS attack.
Even worse is anyone with a bit of money can attempt a DDoS attack
What are DDoS attacks and How Does It Work?
Before passing on to DDoS attacks, let's look at how does an old Denial of Service (DoS) attack works.
Denial of Service Attacks (DoS)
Denial of Service (DoS) Attack, is an attempt related to crash a server with malicious aspirations and connections. A server's primary purpose is accepting and processing
network connections, network queries. Each query and connection requests uses a specific amount of bandwidth, memory and processing power. A lot of people can use all of current
server resources thus it can block new connections. This way websites cannot be reached, actually web sites are deprived of processing power.

Distributed Denial of Service (DDoS) Attacks
In a DDoS attack, the attacker uses a BotNet of security breached devices that can be anyting from other servers to end-users laptops and surveiilance cameras that are connected to networks. A BotNet contains thousands of nodes that the attacker can remotely instruct to overwhelm the target with queries and disable them. It is very difficult to block them all because there are too many bots.

Amplification Attacks
DDoS attacks can become even mroe deceptive. Attackers have a hard time creating BotNets that can generate sufficient data to shut out a well-prepared hosting provider. Instead of directly attacking the taget, they look for an online service to increase their requests.
When you open a web page you initially send a small amount of data and the server sends a much bigger respose. The same also applies for DNS servers, Network Time Protocol (NTP) servers, databases and caches and others like.
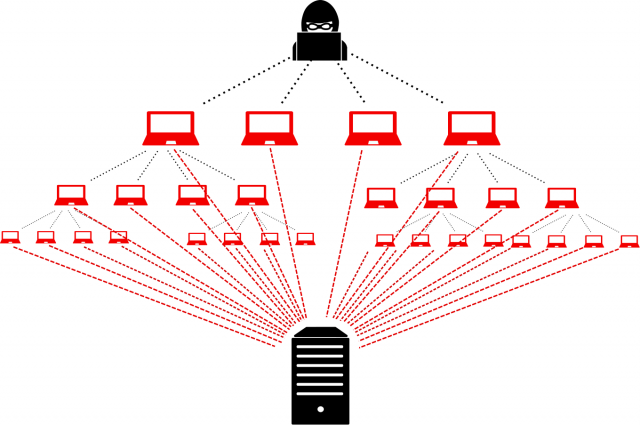
For an example, an attacker can use the BotNet Network to send a request to an open NTP server. The first request is small, originating in a few bytes. But the response can be 200 times bigger. An attacker who sends one megabyte can generate 200 megabytes of response. If they spoof the IP address of the initial query, the data will go directly to the target and not the BotNet network.
What are the types of DDoS Attacks?
The most popular way to classify DDoS attacks is according to the network part that is targeted. You can think connections as link by link, as protocols and data formats. For an example, the HTTP of the web depends on the low level TCP protocol.
Popular Open Systems Interconnection (OSI) Model Seperates Connections to 7 layers
Layer 1 - The physical layer that transmits raw data through the hardware of the network's or server's.
Layer 2 - The data link (datalink) layer that determines the format of the data.
Layer 3 - The network layer that decides which path the data will take.
Layer 4 - The transportation layer, which is the level of TCP and UDP transmission protcols.
Layer 5 - The session layer that manages connections and sessions.
Layer 6 - The presentation layer that handles encryption and data formats.
Layer 7 - The application layer, which is the layer we use when we click links or communicate with web applications.
How to Protect Yourself From an Attack?
As a server or a website manager, there is nothing you can do to prevent attackers from sending malicious network requests. However, you can configure both your server's firewall and web server to disable or block requests coming from malfunctioning IP addresses.
cPanel which is a software accepted among popular server softwares, has a attack reducing tool to help users prevent DDoS attacks.

I present all of you my gratitude, see you on another topic.

Titles of How to block DDoS Attack
What is DDoS attack and How Does It Work?
Denial of Service attacks (DoS)
Distributed Denial of Service (DDoS)
Amplification Attacks
What are the types of DDoS Attacks?
How to protect yourself from an attack?
Denial of Service Attacks (DDos), can make any web site offline. Even Google and GitHub with their enormous resources may struggle when fighting against a DDoS attack.
Even worse is anyone with a bit of money can attempt a DDoS attack
What are DDoS attacks and How Does It Work?
Before passing on to DDoS attacks, let's look at how does an old Denial of Service (DoS) attack works.
Denial of Service Attacks (DoS)
Denial of Service (DoS) Attack, is an attempt related to crash a server with malicious aspirations and connections. A server's primary purpose is accepting and processing
network connections, network queries. Each query and connection requests uses a specific amount of bandwidth, memory and processing power. A lot of people can use all of current
server resources thus it can block new connections. This way websites cannot be reached, actually web sites are deprived of processing power.

Distributed Denial of Service (DDoS) Attacks
In a DDoS attack, the attacker uses a BotNet of security breached devices that can be anyting from other servers to end-users laptops and surveiilance cameras that are connected to networks. A BotNet contains thousands of nodes that the attacker can remotely instruct to overwhelm the target with queries and disable them. It is very difficult to block them all because there are too many bots.

Amplification Attacks
DDoS attacks can become even mroe deceptive. Attackers have a hard time creating BotNets that can generate sufficient data to shut out a well-prepared hosting provider. Instead of directly attacking the taget, they look for an online service to increase their requests.
When you open a web page you initially send a small amount of data and the server sends a much bigger respose. The same also applies for DNS servers, Network Time Protocol (NTP) servers, databases and caches and others like.

For an example, an attacker can use the BotNet Network to send a request to an open NTP server. The first request is small, originating in a few bytes. But the response can be 200 times bigger. An attacker who sends one megabyte can generate 200 megabytes of response. If they spoof the IP address of the initial query, the data will go directly to the target and not the BotNet network.
What are the types of DDoS Attacks?
The most popular way to classify DDoS attacks is according to the network part that is targeted. You can think connections as link by link, as protocols and data formats. For an example, the HTTP of the web depends on the low level TCP protocol.
Popular Open Systems Interconnection (OSI) Model Seperates Connections to 7 layers
Layer 1 - The physical layer that transmits raw data through the hardware of the network's or server's.
Layer 2 - The data link (datalink) layer that determines the format of the data.
Layer 3 - The network layer that decides which path the data will take.
Layer 4 - The transportation layer, which is the level of TCP and UDP transmission protcols.
Layer 5 - The session layer that manages connections and sessions.
Layer 6 - The presentation layer that handles encryption and data formats.
Layer 7 - The application layer, which is the layer we use when we click links or communicate with web applications.
How to Protect Yourself From an Attack?
As a server or a website manager, there is nothing you can do to prevent attackers from sending malicious network requests. However, you can configure both your server's firewall and web server to disable or block requests coming from malfunctioning IP addresses.
cPanel which is a software accepted among popular server softwares, has a attack reducing tool to help users prevent DDoS attacks.

I present all of you my gratitude, see you on another topic.

Moderatör tarafında düzenlendi:




