Social Engineering - Network Privacy Methods
Table of Contents
1.1 - What is Tor Browser?
1.2 - Operating Principle of Tor Network
2.1 - What is VPN?
2.2 - Does VPN Hide You from Cyber Crimes?
3.1 - Tor vs VPN
3.2 - Why VPN?
3.3 - Why Tor?
Hello, dear readers, in this topic, we will discuss privacy methods such as Tor and VPN. I hope you enjoy reading it.
Social Engineering, when used correctly, is a strategic weapon. To use it correctly, you need to know the person closely, understand their weaknesses, and gain their trust. And most importantly, privacy is essential. The person should not learn your real identity. In this case, it is necessary to hide yourself in the best possible way. Now let's take a closer look at these methods.

1.1 Tor Browser
When we look at its logo, we see an onion, and the reason for this is its layered structure. Therefore, it is likened to an onion and used as a logo. When you enter a Tor Network, you first connect to an entry computer, then to a device in the middle layer, and finally, you connect to an exit device as the third step. All of these processes occur in an encrypted manner, and encryption is completed when you reach the final exit.
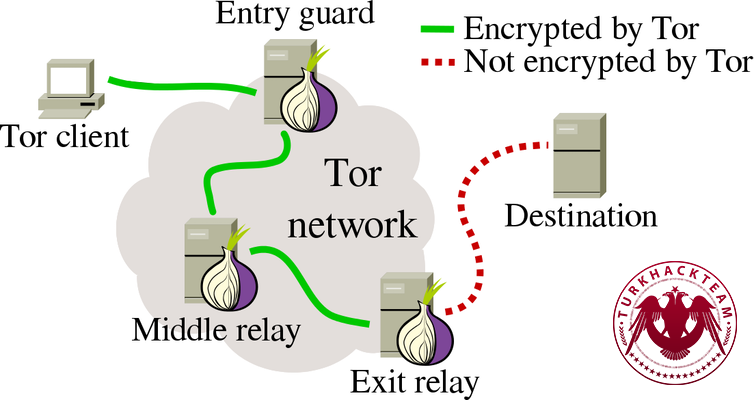
1.2 When we look at the diagram, we can see the working principle of the Tor Network.
In the first stage, you become a "Tor Client" when you are here, which means you become a device on the "Tor Network," and this could mean being someone else's Middle Relay or Exit Relay. In short, you become someone else's machine. From the moment you connect, you make connections through others. The "Entry Guard" is the entry point where your information passes through; the second layer is the "Middle Relay," and the third layer is the "Exit Relay," connecting to the network from there. Then, communication moves in the opposite direction from the "Destination" section. In other words, it reconnects in the opposite direction, making the Tor Network quite secure.
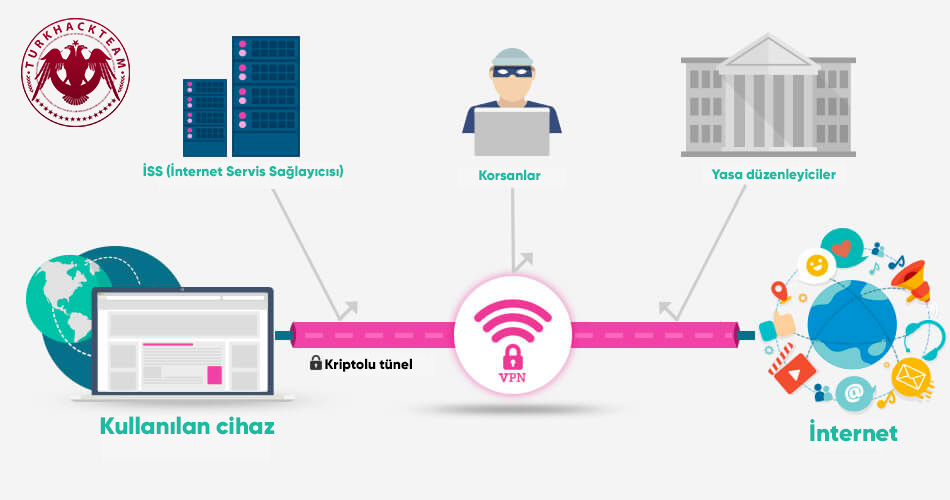
2.1 VPN
Our next method of concealment is VPN. What is it, and let's learn about it now.
VPN has an encrypted tunnel connection. For example, if you send information from your personal device, let's say "ARS," this information is encrypted in the VPN layer, and the encrypted form could be, for example, "RAS." Because the encrypted information is different from its essence, it ensures privacy. The protocol used here is called "IPSEC." As you can see in the graphic, the communication between them is not visible to ISPs, hackers, and the government. This encrypted tunnel can provide you with the guarantee of that.
2.2 Does VPN Hide You in Cyber Crimes?
This depends on the VPN provider you use. For example, if you engage in illegal activities on the "abc.com" site, the first ones to be identified are the ones who made contact. Your VPN provider is visible here, and victims contact the provider, specifying the date and time the crime was committed. The IP addresses of the devices connected on that date are revealed, and they can easily find you. However, since there is no concrete evidence, the likelihood of being accused is low. In this case, the device of the identified person is examined to see if there is any element constituting a crime, and necessary legal action is taken if a criminal element is found.
3.1 Tor VS VPN
Now, Let's Make a Comparison;
3.2 Why VPN?
If you want to ensure that your online banking information does not fall into the wrong hands,
If you want to provide online anonymity,
If you live in a country where there are online access restrictions,
If you want to block targeted, personalized advertisements,
If you are using public networks,
If you want to bypass the network firewall,
If you want to be free, you can choose VPN.
Advantages
It protects your data with end-to-end encryption, ensuring the security of your information. Since it is not tied to a specific browser, it can fully protect your device. By masking your IP address, it allows you to easily bypass country-based restrictions. It is simple and fast to use, and it can be used on any device.
Disadvantages
To use a high-quality VPN, you need to pay a fee, and even though the prices may be affordable, subscriptions can be a disadvantage for you. The fact that you are using a VPN can be easily detected, and exposure is inevitable. There will be a loss of speed due to encryption.
3.3 Why Tor?
If you want to hide your browsing activities, If you are in a country with strict government surveillance, If you want to access restricted content, If you want to express your ideas freely and secretly, If you desire a high level of anonymity, you can choose Tor Browser.
Advantages
It's free, the most cost-effective privacy method. Prioritizes privacy, does not record your browsing activity, and has no subscription-like situations since it's free. Does not store your banking information. Cannot be shut down, Tor servers are distributed worldwide, making it nearly impossible for authorities to intervene or launch attacks. In other words, it has no fixed server.
Disadvantages
The Tor network is very slow, making it less than ideal for normal use. If the site you connect to is not on the DarkWeb and lacks HTTPS support, there is an increased risk of your information being leaked. Using Tor can be detectable, drawing more attention to you and potentially leading to tracking. Only the traffic in your browser is protected.
Dear friends, in this topic, we learned about the methods for the privacy branch of Social Engineering, and gained detailed information about Tor and VPN. We learned which one is more advantageous. Until our next topic, stay well.