

What is CVE-2023-3519 RCE Security Vulnerability?
Today, we will review a very frustrating CVE with a score of 9.8.
On July 18, 2023, Citrix issued a security advisory regarding vulnerabilities affecting Citrix NetScaler ADC and NetScaler Gateway products. These devices can be vulnerable to remote code execution initiated by an attacker when configured as a gateway or authentication server and managed by a customer (i.e., not managed by Citrix). Vulnerabilities on Citrix-managed servers have already been addressed.
Citrix reports observing attacks against unpatched devices targeting CVE-2023-3519. The Cybersecurity and Infrastructure Security Agency (CISA) has also released an advisory detailing an attack leveraging this vulnerability.
Palo Alto Networks customers can protect and mitigate against CVE-2023-3519 as follows:
With the Advanced Threat Prevention security subscription on the Next-Generation Firewall, it can help block attacks.
Cortex Xpanse customers can identify exposed instances of the application using the "Insecure Citrix Application Delivery Controller" attack surface rule.
Palo Alto Networks recommends patching these vulnerabilities, including CVE-2023-3519, with the software update provided by Citrix.
| Vulnerabilities Discussed | CVE-2023-3519, CVE-2023-3466, CVE-2023-3467 |
Details of Vulnerabilities

The most frustrating part of the incident is the severity score of 9.8.
CVE-2023-3519, an Remote Code Execution (RCE) vulnerability with a CVSS severity score of 9.8, was disclosed on July 18, 2023. This vulnerability affects older versions of NetScaler ADC (an application delivery controller software used to secure network traffic) used for securing network traffic and also NetScaler Gateway, which serves as a remote access gateway providing VPN and Single Sign-On (SSO) capabilities for end users.
Additional vulnerabilities addressed in this security advisory that affect NetScaler users include CVE-2023-3466 and CVE-2023-3467. According to Citrix, CVE-2023-3466 is a reflected Cross-Site Scripting (XSS) vulnerability that requires a victim to visit a link controlled by an attacker who can establish a connection to the virtual NetScaler device with NetScaler IP (NSIP) on the same network via a web browser.
CVE-2023-3467 is a privilege escalation vulnerability that requires attackers to have unauthenticated access and potentially allows privilege escalation to root administrator access while granting access to the management interface with NetScaler IP (NSIP) or Subnet IP (SNIP). CVE-2023-3466 and CVE-2023-3467 have severity scores of 8.3 and 8, respectively.
According to Citrix, these three vulnerabilities affect the following versions of Citrix NetScaler ADC and NetScaler Gateway:
NetScaler ADC and NetScaler Gateway prior to 13.1-49.13 for 13.1 versions
NetScaler ADC and NetScaler Gateway prior to 13.0-91.13 for 13.0 versions
NetScaler ADC version 12.1 (End of Life)
NetScaler ADC 13.1-FIPS prior to 13.1-37.159
NetScaler ADC 12.1-FIPS prior to 12.1-55.297
NetScaler ADC 12.1-NDcPP prior to 12.1-55.297
CISA also emphasizes that the device should be configured as a gateway or Authentication, Authorization, and Accounting (AAA) server. Updates provided by Citrix address all three vulnerabilities.
Scope of the Attack
CISA has reported at least one attack where threat actors exploited this vulnerability as a zero-day attack to gain access to a critical infrastructure organization's NetScaler device. In this incident, the threat actor utilized CVE-2023-3519 to drop a PHP web shell on the targeted device.
Subsequently, the threat actor used the deployed web shell to enumerate and exfiltrate Active Directory data. The threat actor also attempted further reconnaissance activities but failed due to the segmented nature of the NetScaler device environment.
Citrix has released a patch for this vulnerability and recommends that all customer-managed devices be updated as soon as possible. Additionally, CISA has published an advisory article along with accompanying documentation that provides detection methods, incident response tips, mitigations, and verification knowledge to protect your organization against this vulnerability and similar ones.
CISA's detection methods include:
Instructions for modifying specific parameters related to your NetScaler device setup
Specific commands to check logs for anomalies
Guidance on reviewing various network logs that may contain abnormal Application Delivery Controller (ADC) activity
The incident response guidance covers fundamental steps such as quarantining affected devices, providing account credentials, and examining system and network components, including processes, services, and logs.
Regarding mitigations, CISA recommends:
Installing the relevant updated versions of NetScaler ADC and NetScaler Gateway as soon as possible.
Following cybersecurity best practices, including mandating phishing-resistant multi-factor authentication (MFA) for all personnel and services in production and corporate environments.
For further best practices, consult CISA's Sector-Specific Cybersecurity Performance Objectives.
Cortex Xpanse
Cortex Xpanse customers can identify exposed instances of the application using the "Insecure Citrix Application Delivery Controller" attack surface rule. This rule is provided to all customers by default and is set to "Open" status.
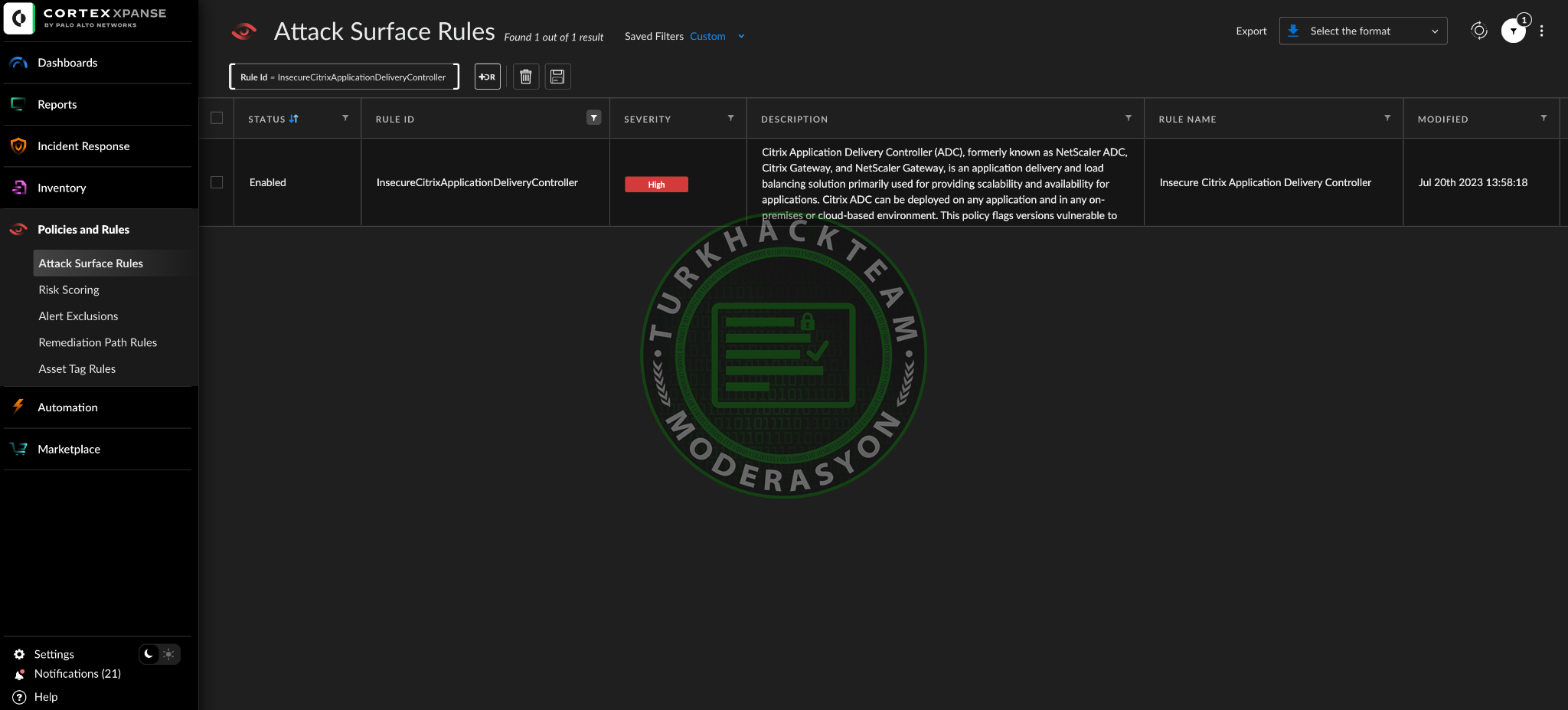
Figure 1. A screenshot of the Cortex Xpanse interface demonstrating that the Insecure Citrix Application Delivery Controller rule is active.
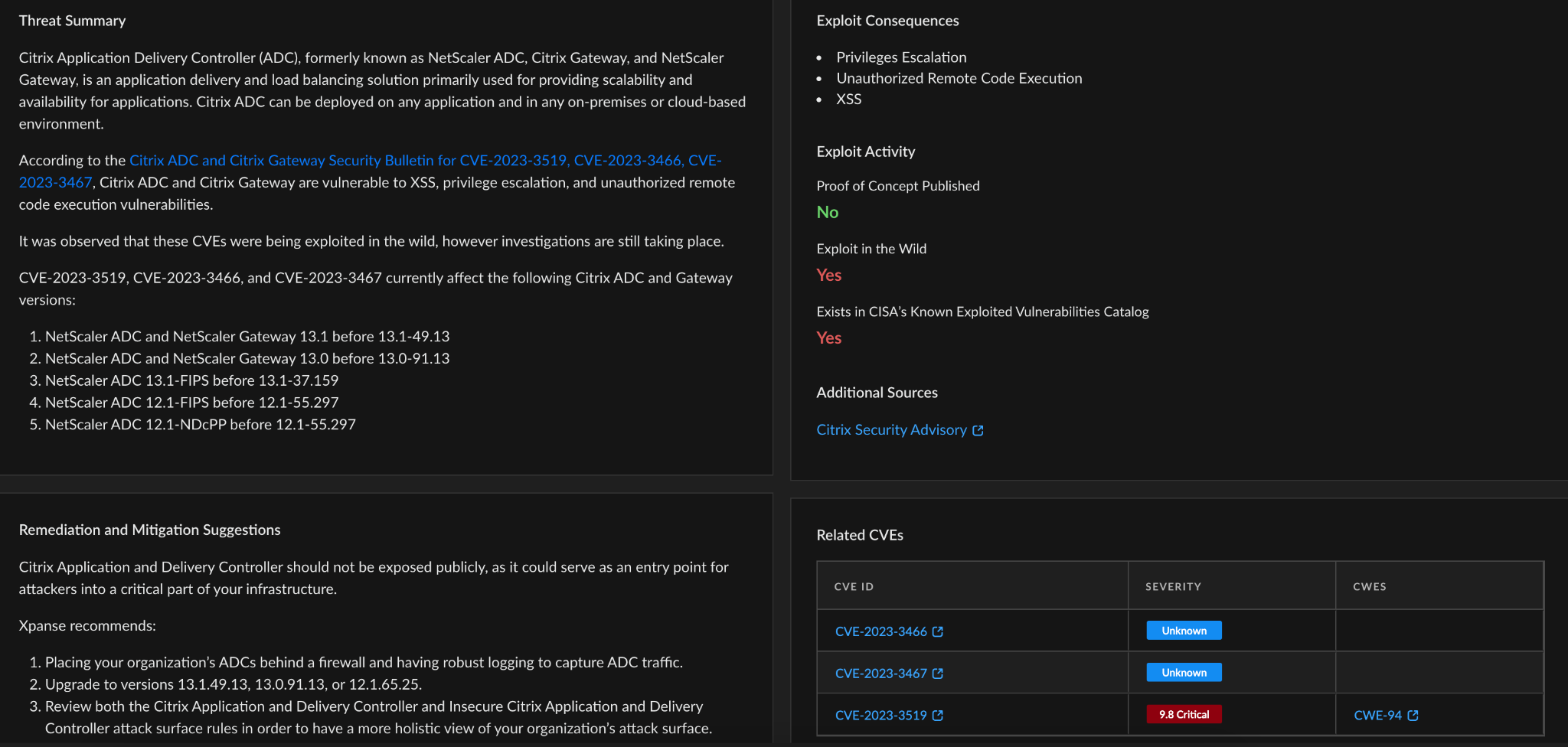
Figure 2. A screenshot of the Cortex Xpanse interface displaying the Threat Summary, including Improvement and Mitigation Recommendations.
Threat Indicators
SHA-256 Hash Value
293fe23849cffb460e8d28691c640a5292fd4649b0f94a019b45cc586be83fd9
IP Addresses
216.41.162[.]172
216.51.171[.]17
Blocked Interesting Resources


Source : https://www.turkhackteam.org/konular/cve-2023-3519-rce-guvenlik-acigi-nedir.2047881/

Figure 2. A screenshot of the Cortex Xpanse interface displaying the Threat Summary, including Improvement and Mitigation Recommendations.
Threat Indicators
SHA-256 Hash Value
293fe23849cffb460e8d28691c640a5292fd4649b0f94a019b45cc586be83fd9
IP Addresses
216.41.162[.]172
216.51.171[.]17
Blocked Interesting Resources


Source : https://www.turkhackteam.org/konular/cve-2023-3519-rce-guvenlik-acigi-nedir.2047881/





